[ad_1]

Hundreds of thousands of FortiGate firewalls are vulnerable to a critical security issue identified as CVE-2023-27997, nearly a month after Fortinet released an update that fixes the problem.
The vulnerability is a remote code execution with a severity score of 9.8 out of 10 resulting from a heap-based buffer overflow issue in FortiOS, the operating system that connects all Fortinet networking components to integrate them into the vendor’s Security Fabric platform.
CVE-2023-27997 is exploitable and allows an unauthenticated attacker to execute code remotely on vulnerable devices with the web-exposed SSL VPN interface. In a notice in mid-June, the supplier warned that the problem may have been exploited in attacks.
Fortinet patched the vulnerability on June 11 before disclosing it publicly, in FortiOS firmware release versions 6.0.17, 6.2.15, 6.4.13, 7.0.12 and 7.2.5.
Offensive security solutions company Bishop Fox reported Friday that despite calls for patches, more than 300,000 FortiGate firewall appliances are still vulnerable to attack and accessible on the public internet.
The Bishop Fox researchers used the Shodan search engine to find devices that responded in a way that indicated an exposed SSL VPN interface. They did this by looking for appliances that returned a specific HTTP response header.
They filtered the results to those that were redirected to “/remote/login”, a clear indication of an exposed SSL VPN interface.
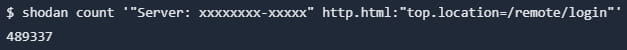
The query above showed 489,337 devices, but not all of them were vulnerable to CVE-2023-27997, also known as Xortigate. Further investigation revealed that 153,414 of the discovered devices had been updated to a safe version of FortiOS.
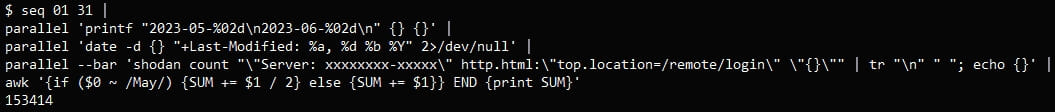
This means that about 335,900 of the web-accessible FortiGate firewalls are vulnerable to attack, a number significantly higher than the 250,000 recent estimates based on other less precise queries, according to Bishop Fox researchers.
Another discovery made by Bishop Fox researchers is that many of the FortiGate devices on display have not received an update in the last eight years, with some of them working FortiOS 6, which has reached end of support last year on September 29.
These devices are vulnerable to several critical-severity flaws whose proof-of-concept exploit code is publicly available.
To demonstrate that CVE-2023-27997 can be used to execute code remotely on vulnerable devices, Bishop Fox created an exploit that allows “breaking the heap, reconnecting to an attacker-controlled server, downloading a BusyBox binary and open an interactive shell.”

source: Bishop Fox
“This exploit very closely follows the steps detailed in the original Lexfo blog post […] and runs in about a second, which is significantly faster than the demo video on a 64-bit device presented by Lexfo,” notes Bishop Fox in their report.
[ad_2]
Source link
