[ad_1]

A new ‘Nitrogen’ initial access malware campaign uses Google and Bing search ads to promote fake software sites that infect unsuspecting users with Cobalt Strike and ransomware payloads.
The goal of the Nitrogen malware is to provide the threat actors initial access to corporate networks, allowing them to conduct data-theft, cyberespionage, and ultimately deploying the BlackCat/ALPHV ransomware.
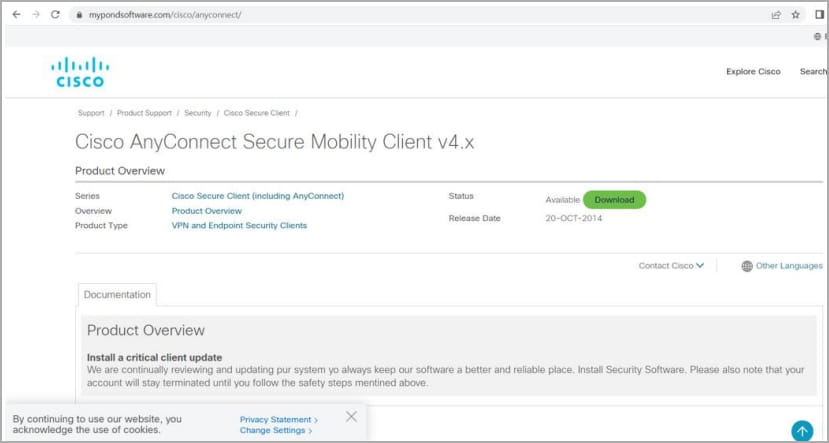
Today, Sophos released a report on the Nitrogen campaign, detailing how it primarily targets technology and non-profit organizations in North America, impersonating popular software like AnyDesk, Cisco AnyConnect VPN, TreeSize Free, and WinSCP.
Trend Micro was the first to document this activity at the start of the month, seeing WinSCP ads leading to BlackCat/ALPHV ransomware infections on a victim’s network.
However, that report focused on the post-infection stage and lacked extensive IoCs (Indicators of Compromise) due to being based on a single response incident.
The Nitrogen malware campaign
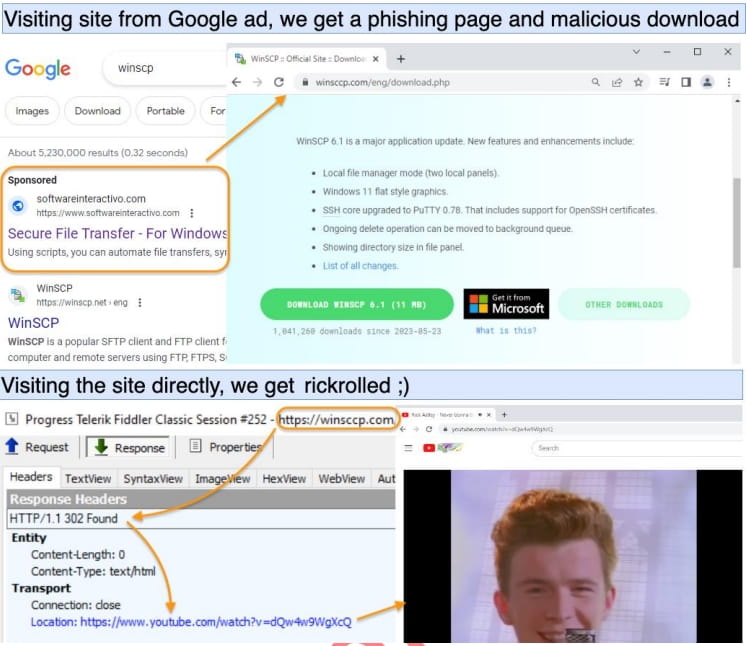
The Nitrogen malware campaign starts with a person performing a Google or Bing search for various popular software applications.
The software seen as lures for the Nitrogen malware campaign includes:
- AnyDesk (remote desktop application)
- WinSCP (SFTP/FTP client for Windows)
- Cisco AnyConnect (VPN suite)
- TreeSize Free (disk-space calculator and manager)
Depending on the targeting criteria, the search engine will display an advertisement that promotes the searched-for software.
Clicking the link brings the visitor to compromised WordPress hosting pages that imitate the legitimate software download sites for the particular application.
Only visitors of specific geographic regions are redirected to the phishing sites, while direct hits onto the malicious URLs trigger a rick-rolling redirection to YouTube videos instead.
Source: Sophos
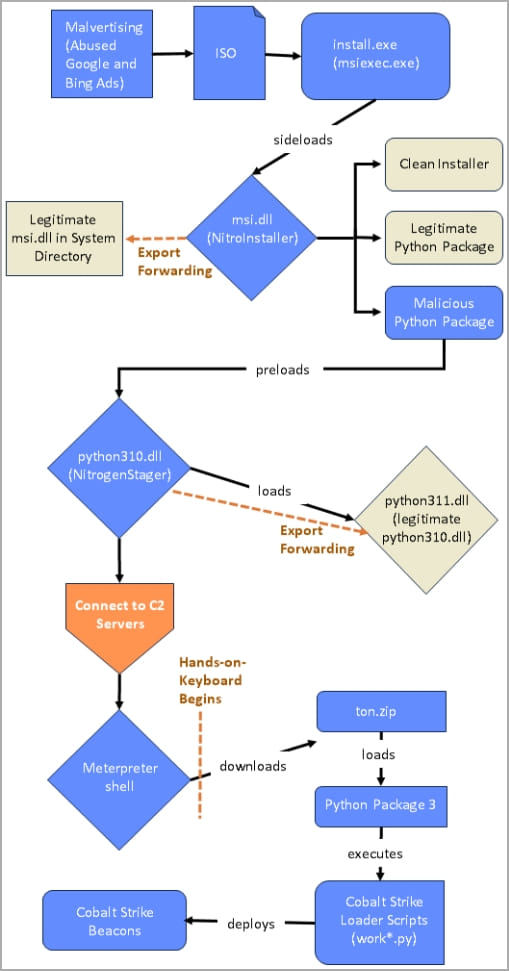
From those fake sites, users download trojanized ISO installers (“install.exe”), which contain and sideload a malicious DLL file (“msi.dll”).
The msi.dll is the installer for the Nitrogen initial access malware called internally “NitrogenInstaller,” which further installs the promised app to avoid suspicion and a malicious Python package.
Source: Sophos
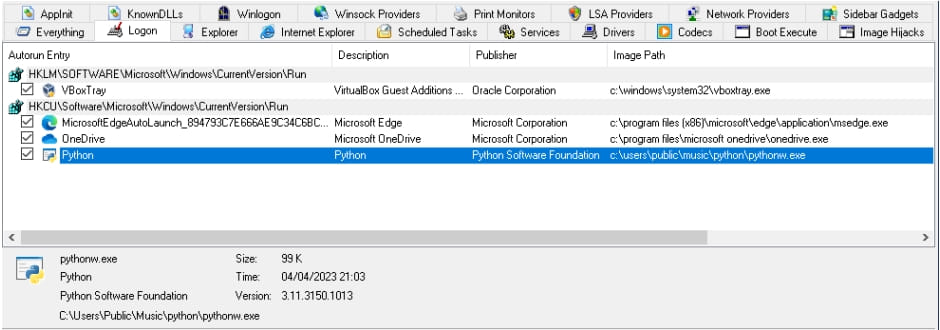
The NitrogenInstaller also creates a registry run key named “Python” for persistence, pointing to a malicious binary (“pythonw.exe”) that runs every five minutes.
Source: Sophos
The Python component will execute “NitrogenStager” (“python.311.dll”), which is responsible for establishing communication with the threat actor’s C2 and launching a Meterpreter shell and Cobalt Strike Beacons onto the victim’s system.
In some cases observed by Sophos analysts, the attackers moved to hands-on activity once the Meterpreter script was executed on the target system, executing manual commands to retrieve additional ZIP files and Python 3 environments.
The latter is needed for executing Cobalt Strike in memory, as the NitrogenStager cannot run Python scripts.
Source: Sophos
Sophos says due to successfully detecting and stopping the observed Nitrogen attacks, it has not determined the threat actor’s goal, but the infection chain point to staging the compromised systems for ransomware deployment.
However, Trend Micro had previously reported that this attack chain led to the deployment of the BlackCat ransomware in at least one case.
This campaign is not the first time ransomware gangs abused search engine advertisements to gain initial access to corporate networks, with both the Royal and Clop ransomware operations using this tactic in the past.
Users are recommended to avoid clicking on “promoted” results in search engines when downloading software and instead only downloading from the developer’s official site.
Also, be wary of any downloads utilizing ISO files for software, as that is an uncommon method to distribute legitimate Windows software, which usually comes as an .exe or .zip archive.
[ad_2]
Source link
