[ad_1]

Threat actors are promoting a new “Exfiltrator-22” post-exploitation framework designed to spread ransomware in corporate networks while evading detection.
CYFIRMA threat analysts claim that this new framework was created by former Lockbit 3.0 affiliates, experts in anti-analysis and defense evasion, offering a robust solution in exchange for a subscription.
Exfiltrator-22 prices range from $1,000 per month to $5,000 for lifetime access, offering continuous updates and support.
Buyers of the framework receive an administration panel hosted on a bulletproof VPS (virtual private server) from which they can monitor framework malware and issue commands to compromised systems.
The first version of the Exfiltrator-22 (EX-22) appeared in the wild on November 27, 2022, and about ten days later, its authors created a Telegram channel to announce the framework to other cybercriminals.
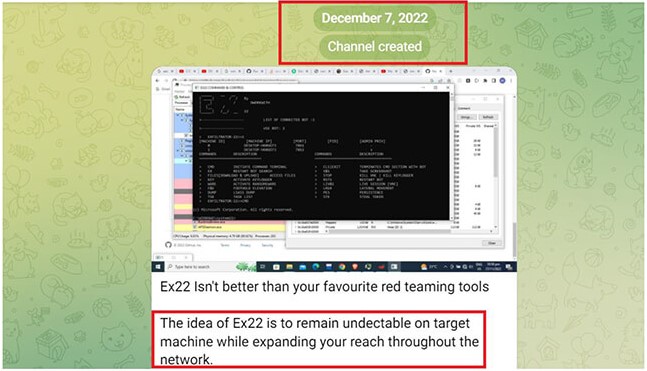
At the end of the year, threat actors announced new features that helped conceal traffic on compromised devices, indicating that the framework was under active development.
In January 2023, EX-22 was deemed 87% ready by its authors, and subscription prices were announced, inviting interested users to purchase access to the tool.
On February 10, 2023, threat actors released two demonstration videos on YouTube to showcase the EX-22’s lateral movement and ransomware spreading capabilities.
Features of the Exfiltrator-22
EX-22 includes features commonly found in other post-exploit toolkits, but also additional features aimed at ransomware deployment and data theft.
The main features included in the framework are:
- Establish a reverse shell with elevated privileges.
- Upload files to the hacked system or upload files from host to C2.
- Enable a keylogger to capture keyboard input.
- Activate a ransomware module to encrypt files on the infected device.
- Capture a screenshot of the victim’s computer.
- Start a live Virtual Network Computing (VNC) session for real-time access to the compromised device.
- Get higher privileges on the infected device.
- Establish persistence between system restarts.
- Activate a worm module that spreads malware to other devices on the same network or the public internet.
- Extract data (passwords and tokens) from LSAAS (Local Security Authority Subsystem Service).
- Generate cryptographic hashes of files on the host to help closely monitor file locations and content change events.
- Retrieve the list of processes running on the infected device.
- Extract authentication tokens from the hacked system.
The above commands are sent to compromised devices through the “EX22 Command & Control” Windows console program.
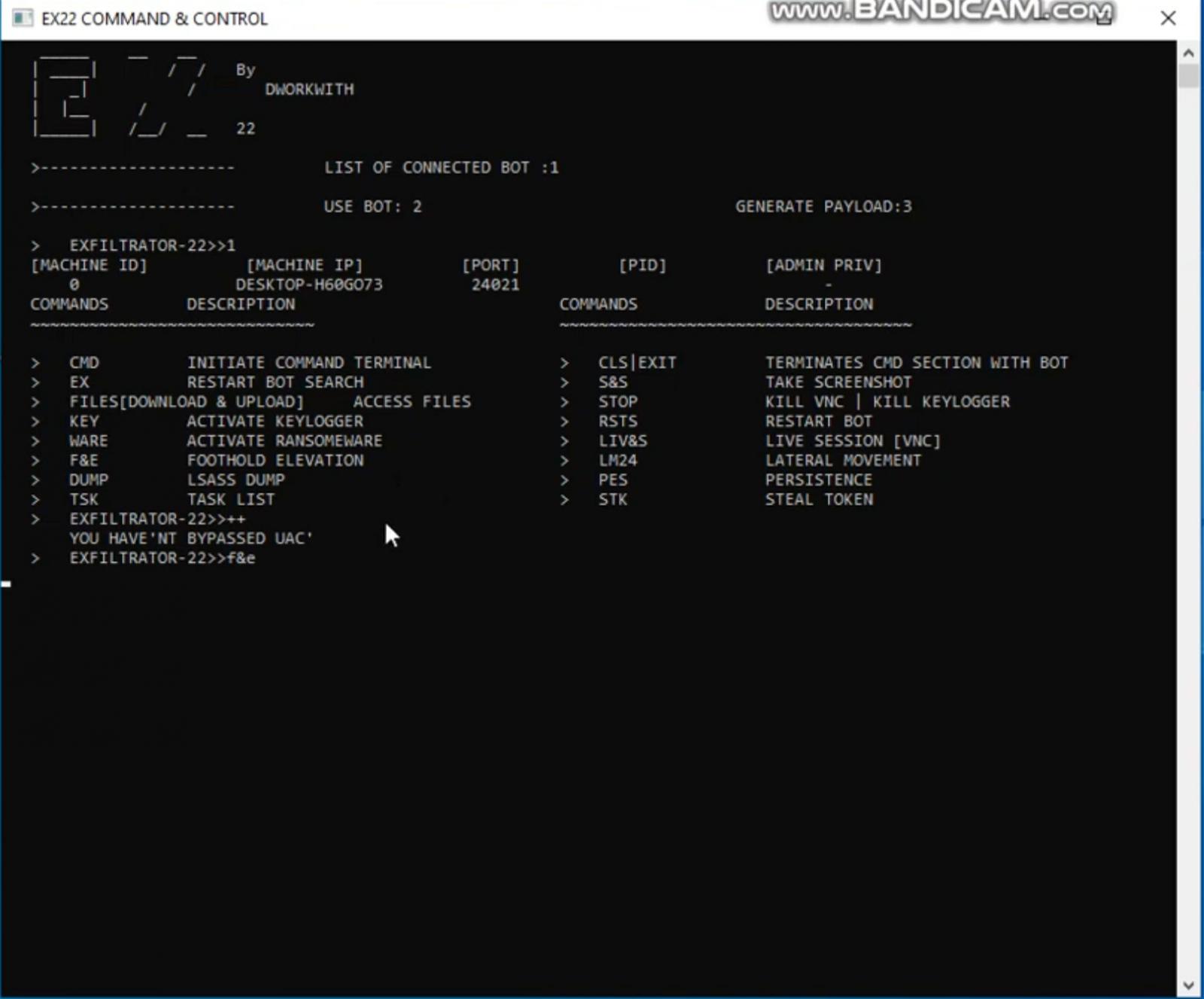
The outputs of these commands are then sent back to the command and control server and displayed directly in the console application, as shown below.
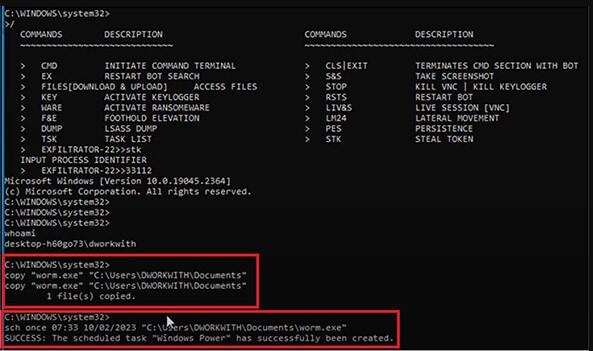
Using the service’s web panel, cybercriminals can also set scheduled tasks, update agents to a new version, modify a campaign’s configuration, or create new campaigns.
Linked to LockBit ransomware members
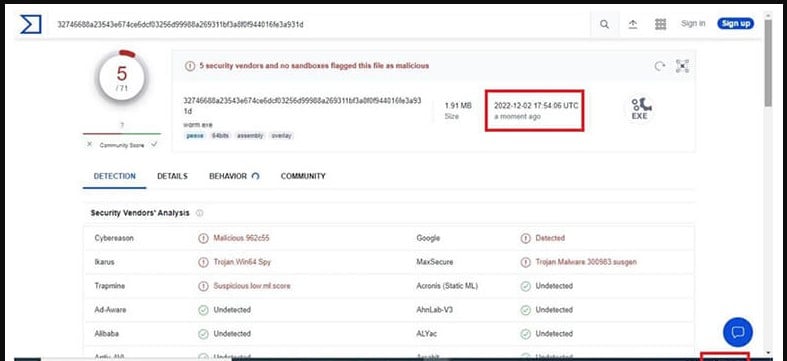
The CYFIRMA team has found evidence that LockBit 3.0 affiliates or members of the ransomware operation’s development team are behind EX-22.
First, they noticed that the framework uses the same “front-end domain” technique associated with LockBit and the TOR Meek obfuscation plugin, which hides malicious traffic inside legitimate HTTPS connections to reputable platforms.
After further investigation, CYFIRMA has found this EX-22 also uses the same C2 infrastructure previously exposed in a LockBit 3.0 sample.
Unfortunately, Exfiltrator-22 seems to have been created by experienced malware authors who have the skills to develop an evasive framework.
Therefore, it is expected to generate a lot of interest in the cybercrime community despite its high price tag, naturally leading to additional code development and feature enhancements.
[ad_2]
Source link
