[ad_1]

Suspected Chinese hackers exploited a newly disclosed FortiOS SSL-VPN vulnerability in December, targeting a European government and an African MSP with new custom Linux and Windows malware “BOLDMOVE”.
The vulnerability is identified as CVE-2022-42475 and was quietly patched by Fortinet in November. Fortinet publicly disclosed the vulnerability in December, encourage customers to patch their devices as threat actors actively exploited the flaw.
The flaw allows unauthenticated remote attackers to remotely crash targeted devices or achieve remote code execution.
However, it is only this month that Fortinet shared more details on how hackers exploited it, explaining that threat actors had targeted government entities with custom malware specifically designed to run on FortiOS devices.
Attackers focused on maintaining persistence on exploited devices by using the custom malware to patch FortiOS logging processes so that specific log entries could be deleted or to disable the logging process altogether.
Yesterday, Mandiant published a report on an alleged Chinese spy campaign exploiting the FortiOS flaw since October 2022 using new malware “BOLDMOVE” explicitly designed for attacks on FortiOS devices.
The new BOLDMOVE malware
BOLDMOVE is a complete backdoor written in C that allows Chinese hackers to gain next-level control over the device, with the Linux version specifically created to run on FortiOS devices.
Mandiant has identified several versions of BOLDMOVE with varying functionality, but the core feature set observed in all samples includes:
- Carrying out a system survey.
- Receiving commands from the C2 server (command and control).
- Creating a remote shell on the host.
- Relay traffic through the hacked device.
The commands supported by BOLDMOVE allow hackers to remotely manage files, execute commands, create interactive shells and control backdoors.
The Windows and Linux variants are largely the same but use different libraries, and Mandiant believes the Windows version was compiled in 2021, almost a year before the Linux variant.
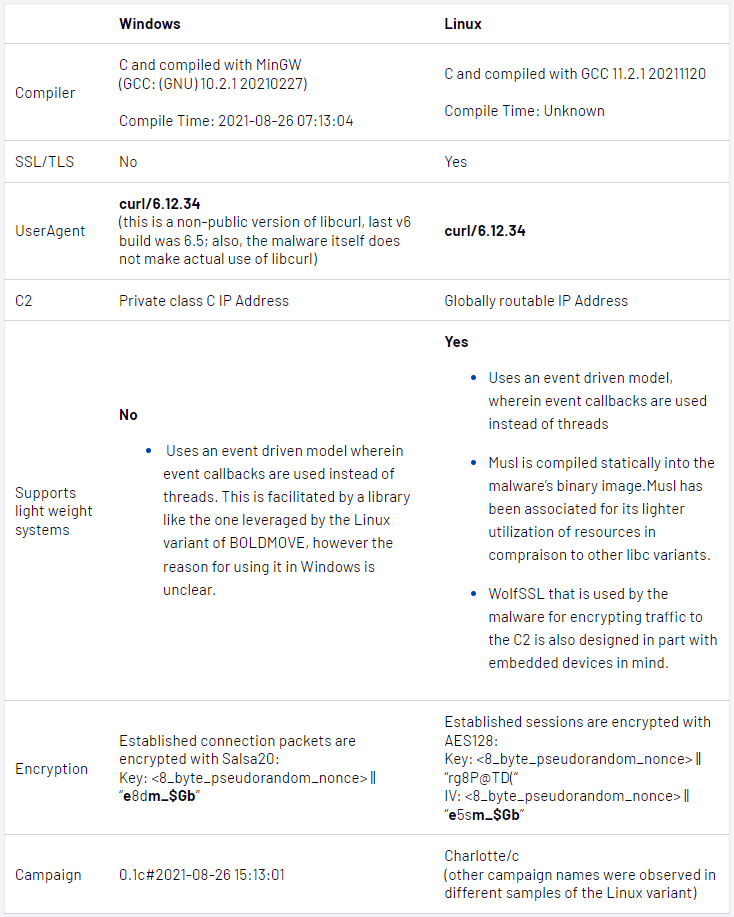
However, the most significant difference between the Linux and Windows versions is that one of the Linux variants contains features that specifically target FortiOS devices.
For example, a Linux BOLDMOVE release allows attackers to modify Fortinet logs on the compromised system or completely disable logging daemons (miglogd and syslogd), making it harder for defenders to track the intrusion.
Additionally, this version of BOLDMOVE can send requests to internal Fortinet services, allowing attackers to send network requests to the entire internal network and spread laterally to other devices.
The Chinese cyber espionage group will continue to target unpatched Internet-connected devices, such as firewalls and IPS/ISD devices, as they provide easy network access without requiring interaction.
Unfortunately, it’s not easy for defenders to examine the processes running on these devices, and Mandiant says the native security mechanisms don’t work very well to protect them.
“There is no mechanism to detect malicious processes running on such devices, nor telemetry to proactively scan for malicious images deployed to them as a result of a vulnerability being exploited,” explains Mandiant in the report.
“This makes network devices a blind spot for security practitioners and allows attackers to hide in them and remain stealthy for long periods of time, while using them to gain a foothold in a targeted network.”
The appearance of a tailor-made backdoor for one of these devices demonstrates the threat actors’ deep understanding of how the perimeter network devices work and the initial access opportunity they represent.
[ad_2]
Source link
