[ad_1]

Microsoft today released a step-by-step guide to help customers discover signs of compromise through exploiting a recently patched Outlook zero-day vulnerability.
Tracked as CVE-2023-23397, this privilege escalation security flaw in the Outlook for Windows client allows attackers to steal NTLM hashes without user interaction in NTLM relay zero-click attacks.
Threat actors can exploit it by sending messages with extended MAPI properties containing UNC paths to SMB shares controlled by the attacker.
In today’s report, Microsoft shared several techniques to discover if credentials have been compromised via CVE-2023-23397 exploits, as well as mitigations to defend against future attacks.
While the company also has published a script To help administrators verify whether Exchange users have been targeted, Redmond said defenders should look for other signs of exploitation if threat actors have cleaned up their tracks by deleting all incriminating messages.
Other sources of indicators of compromise related to this Outlook flaw include telemetry extracted from multiple sources such as firewall, proxy, VPN, and RDP gateway logs, as well as Azure Active Directory connection logs for Exchange Online users and IIS logs for Exchange. Server.
Other places security teams should look for signs of compromise are endpoint forensic data like Windows event logs and endpoint telemetry from endpoint detection and response solutions. termination (EDR) (if available).
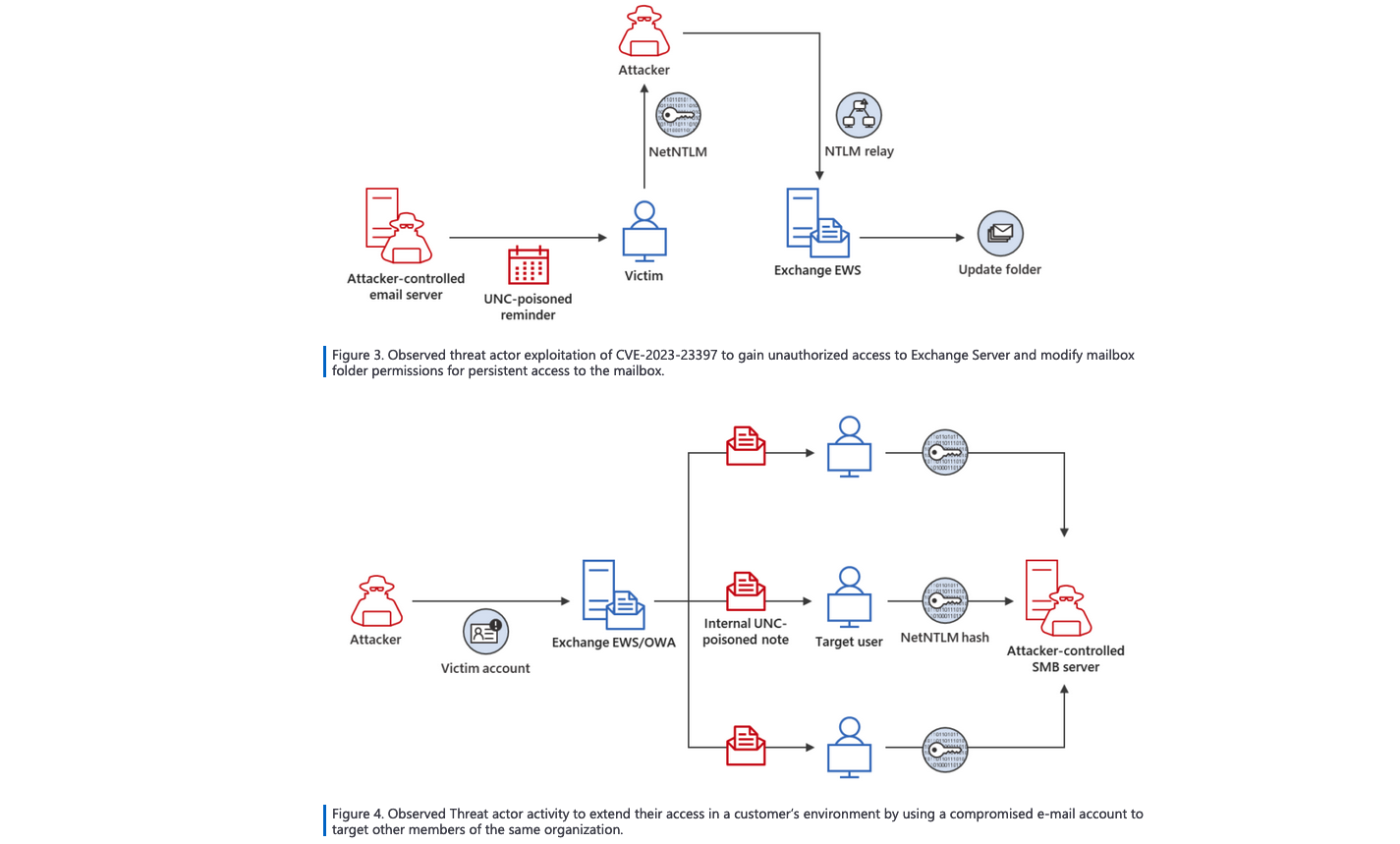
In compromised environments, post-exploit indicators relate to targeting of Exchange EWS/OWA users and malicious mailbox folder permission changes allowing attackers to gain persistent access to victims’ emails.
CVE-2023-23397 Mitigation Measures
Microsoft also shared guidance on how to block future attacks targeting this vulnerability, urging organizations to install the recently released Outlook security update.
“To address this vulnerability, you must install the Outlook Security Update regardless of where your email is hosted (e.g., Exchange Online, Exchange Server, another platform) or taken your organization supports NTLM authentication,” the Microsoft Incident Response team said. said.
Other steps at-risk organizations can take to mitigate these attacks and post-exploit behaviors include:
- For organizations using on-premises Microsoft Exchange Server, apply the latest security updates to ensure that defense-in-depth mitigations are active.
- When suspicious or malicious callback values are observed, be sure to use the script to suppress messages or just properties, and consider initiating incident response activities.
- For any targeted or compromised user, reset the passwords of any account connected to computers from which the user received suspicious callbacks and initiate incident response activities.
- Use multi-factor authentication to mitigate the impact of potential Net-NTLMv2 relay attacks. NOTE: This will not prevent a threat actor from leaking credentials and breaking them offline.
- Disable unnecessary services on Exchange.
- Restrict SMB traffic by blocking connections on ports 135 and 445 from all incoming IP addresses except those on a controlled allow list.
- Disable NTLM in your environment.
Operated by Russian military hackers
CVE-2023-23397 has been in active operation since at least April 2022 and was used to breach the networks of at least 15 government, military, energy and transport organizations in Europe.
While Microsoft has publicly linked these attacks to “a Russian-based threat actor”, Redmond also said in a private threat analysis report seen by BleepingComputer that it believes the hacking group is APT28 (also followed as STRONTIUMSednit, Sofacy and Fancy Bear).
This threat actor was previously linked to the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU), the Russian military intelligence service.
The credentials they stole in these attacks were used for lateral moves and to change Outlook mailbox folder permissions, a tactic that allowed them to exfiltrate emails from specific accounts. .
“While exploiting NTLMv2 hashes to gain unauthorized access to resources is not a new technique, exploiting CVE-2023-23397 is new and stealthy,” the Microsoft Incident Response team added.
“Even when users reported suspicious task reminders, initial security review of the messages, tasks, or calendar items involved did not result in detection of the malicious activity. absence of any required user interaction contributes to the unique nature of this vulnerability.”
[ad_2]
Source link
