[ad_1]

A new attack method named COVID-bit uses electromagnetic waves to transmit data from systems isolated from the internet over a distance of at least two meters (6.5 feet), where it is picked up by a receiver.
The information transmitted by the isolated device could be picked up by a nearby smartphone or laptop, even if a wall separates them.
The COVID-bit attack was developed by Mordechai Guri, a researcher at Ben-Gurion University, who devised several methods to stealthily steal sensitive data from isolated systems. Previous works include the “ETHERLED” and “Satanattacks.
Initial compromise
Isolated systems are computers found in high-risk environments such as energy infrastructure, government, and arms control units, so they are isolated from the public internet for security reasons.
For any attack on these systems, a rogue insider or opportunistic intruder must first plant tailored malware on the target computers through physical contact with the isolated device or network.
Although it seems impractical or even far-fetched, history provides several examples of such attacks, including the Stuxnet worm at a uranium enrichment facility, Agent.BTZ infected a US military base via USB drives and Remsec malware, which collected information. government networks that have been isolated for more than five years.
To transmit the data, the researchers created a malicious program that regulates processor load and core frequency in a particular way so that isolated computer power supplies emit electromagnetic radiation in a low frequency band (0 – 48 kHz ).
“The main source of electromagnetic radiation in SMPSs is due to their internal design and switching characteristics,” Guri explains in the technical document.
“During AC-DC and DC-DC conversion, MOSFET switching components that turn on or off at specific frequencies create a square wave.”
The electromagnetic wave can carry a payload of raw data, following a stub of eight bits that signify the start of transmission.
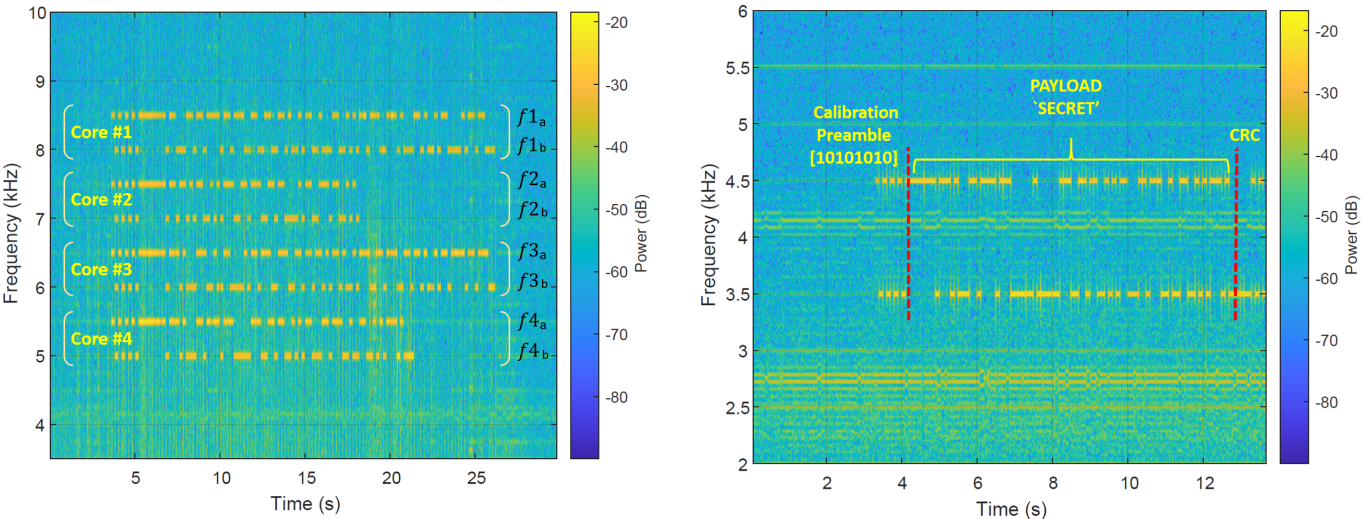
The receiver can be a laptop or smartphone using a small loop antenna connected to the 3.5mm audio jack, which can be easily spoofed as headphones/earphones.
The smartphone can capture the transmission, apply a noise reduction filter, demodulate the raw data, and optionally decode the secret.

The results
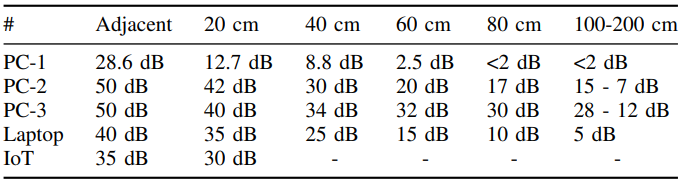
Guri tested three desktop computers, a laptop and a single board computer (Raspberry Pi 3) for different bitrates, maintaining zero bit error rate up to 200 bps on PCs and IoT and up to 100 bps for the laptop.
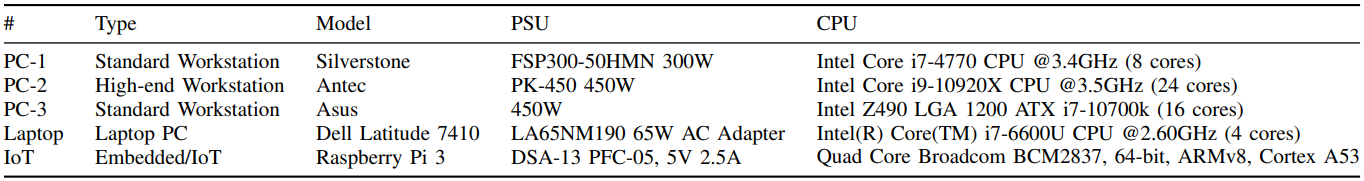
Laptops perform less well because their power-saving profiles and more power-efficient processor cores cause their power supplies to not generate strong enough signals.
Desktop PCs could achieve a transmission rate of 500 bps for a bit error rate between 0.01% and 0.8% and 1000 bps for a bit error rate of up to 1.78%, which is still acceptable.
The machine’s distance was limited for the IoT due to its low power supply, while the signal-to-noise ratio was also worse for the laptop as the test probes moved away.
At the tested maximum transmission rate (1000 bps), a 10 KB file would be transmitted in 80 seconds, an RSA encryption key would be transmitted in approximately 4 seconds, and an hour’s worth of keystroke logging raw data would be sent to the receiver in 20 seconds. seconds.
Live keylogging would work in real time, even for transmission rates as low as five bits per second.
.png)
The researcher also experimented with virtual machines, finding that interrupts from VM output interrupts to the hypervisor manager cause signal degradation between 2 dB and 8 dB.
Protect yourself against the COVID-bit
The most effective defense against the COVID-bit attack would be to strictly restrict access to isolated devices to prevent installation of the required malware. However, this does not protect you from insider threats.
For this attack, the researchers recommend monitoring CPU core usage and detecting suspicious loading patterns that do not match the expected behavior of the computer.
However, this countermeasure has the disadvantage of having many false positives and adds data processing overhead which reduces performance and increases power consumption.
Another countermeasure would be to lock the CPU core frequency to a specific number, which would make it harder to generate the data-carrying signal, even if it didn’t completely stop it.
This method has the disadvantage of reducing CPU performance or wasting a lot of power, depending on the selected lock frequency.
[ad_2]
Source link
