[ad_1]

Honda’s e-commerce platform for electrical, marine, lawn and garden equipment was vulnerable to unauthorized access by anyone due to API flaws that allow password reset for anyone. which account.
Honda is a Japanese manufacturer of automobiles, motorcycles and electrical equipment. In this case, only this last division is affected, so owners of Honda cars or motorcycles are not affected.
The security flaw in Honda’s systems was discovered by a security researcher using the pseudonym “Eaton Works”, which is the same one who hacked into Toyota’s supplier portal. few months agoexploiting similar vulnerabilities.
For Honda, Eaton Works leveraged a password reset API to reset the password of valuable accounts and then gain unrestricted access to admin-level data on the corporate network.
“The broken/missing access controls allowed access to all platform data, even while logged in as a test account,” explains the researcher.
As a result, the following information was exposed to the security researcher and possibly threat actors exploiting the same vulnerability:
- 21,393 customer orders across all dealerships from August 2016 to March 2023 – this includes customer name, address, phone number and items ordered.
- 1,570 dealer websites (of which 1,091 are active). It was possible to modify any of these sites.
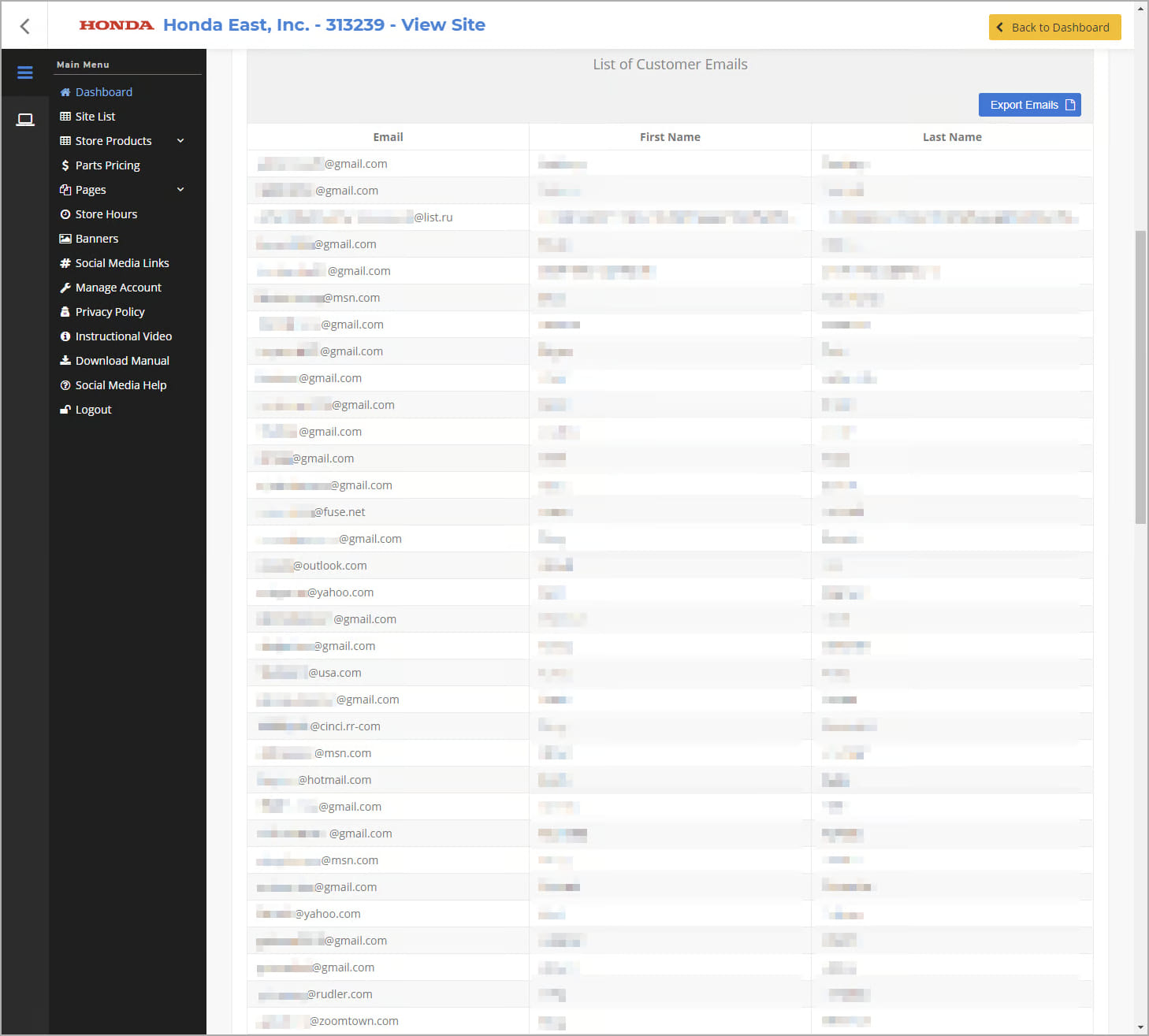
- 3,588 users/dealer accounts (includes first and last name, email address). It was possible to change the password of each of these users.
- 1,090 dealer emails (includes first and last name).
- 11,034 customer emails (including first and last name).
- Potentially: Stripe, PayPal, and Authorize.net private keys for resellers who provided them.
- Internal financial reports.
The above data could be used to launch phishing campaigns, social engineering attacks or sold on hacker forums and dark web marketplaces.
Additionally, by gaining access to reseller sites, attackers could plant credit card skimmers or other malicious JavaScript code snippets.
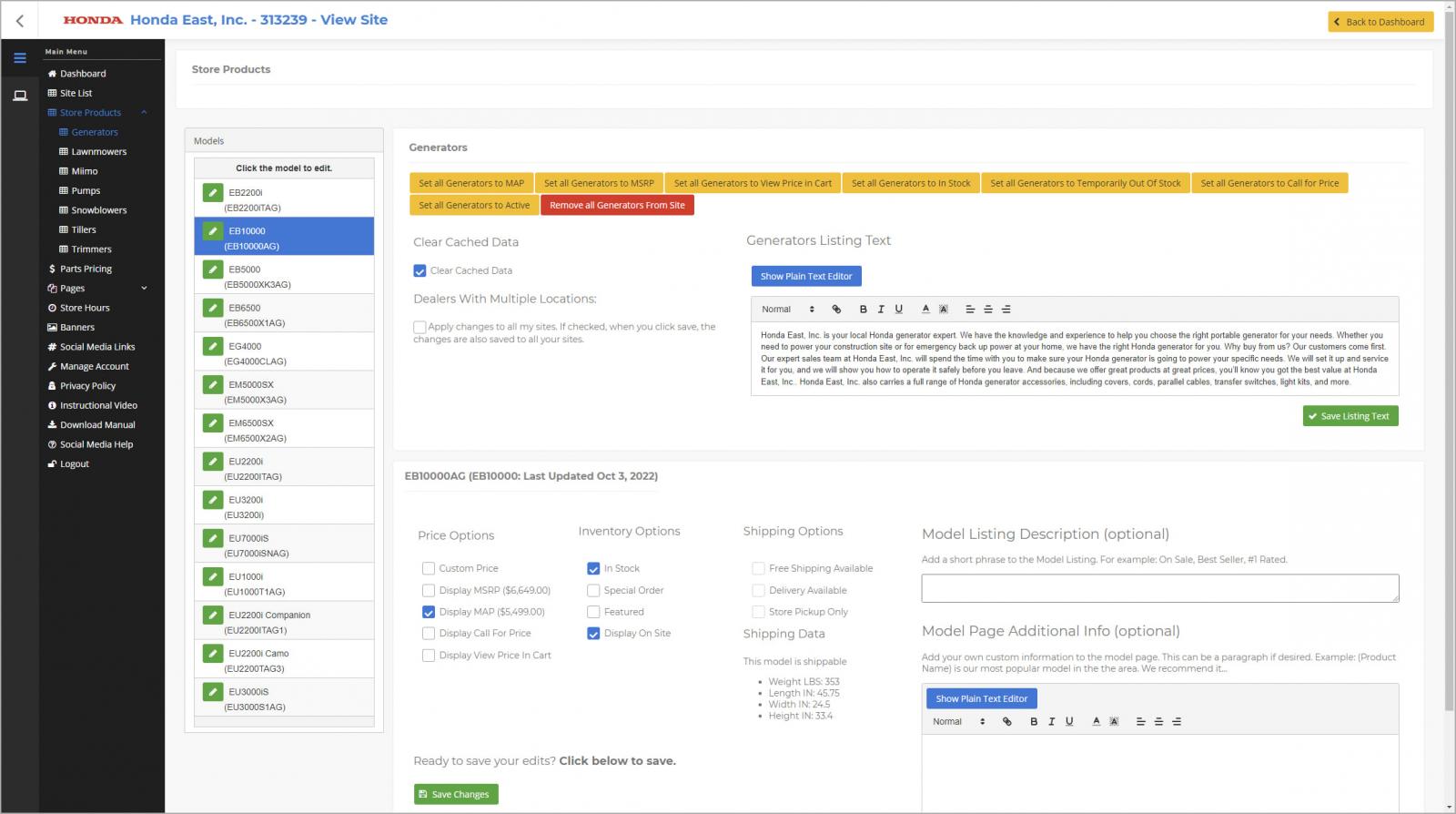
Access admin panels
EatonWorks says the API flaw resided in Honda’s e-commerce platform, which assigns “powerdealer.honda.com” subdomains to registered dealers/dealers.
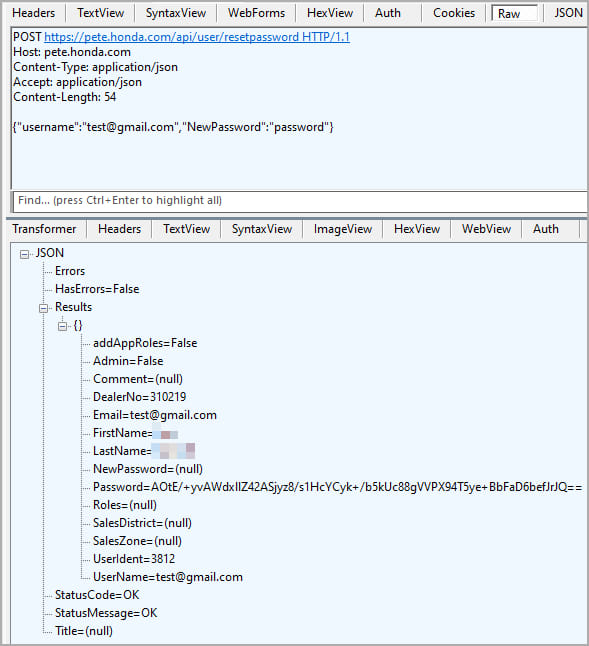
The researcher found that the password reset API on one of Honda’s sites, Power Equipment Tech Express (PETE), handled reset requests without a token or previous password, requiring only an e -email valid.
Although this vulnerability is not present on the e-commerce subdomain login portal, credentials transferred through the PETE site will still work on them, so anyone can access the dealer’s internal data via this simple attack.
The only missing piece is having a valid email address belonging to a reseller, which the researcher obtained from a YouTube video that showcased the reseller dashboard using an account of testing.
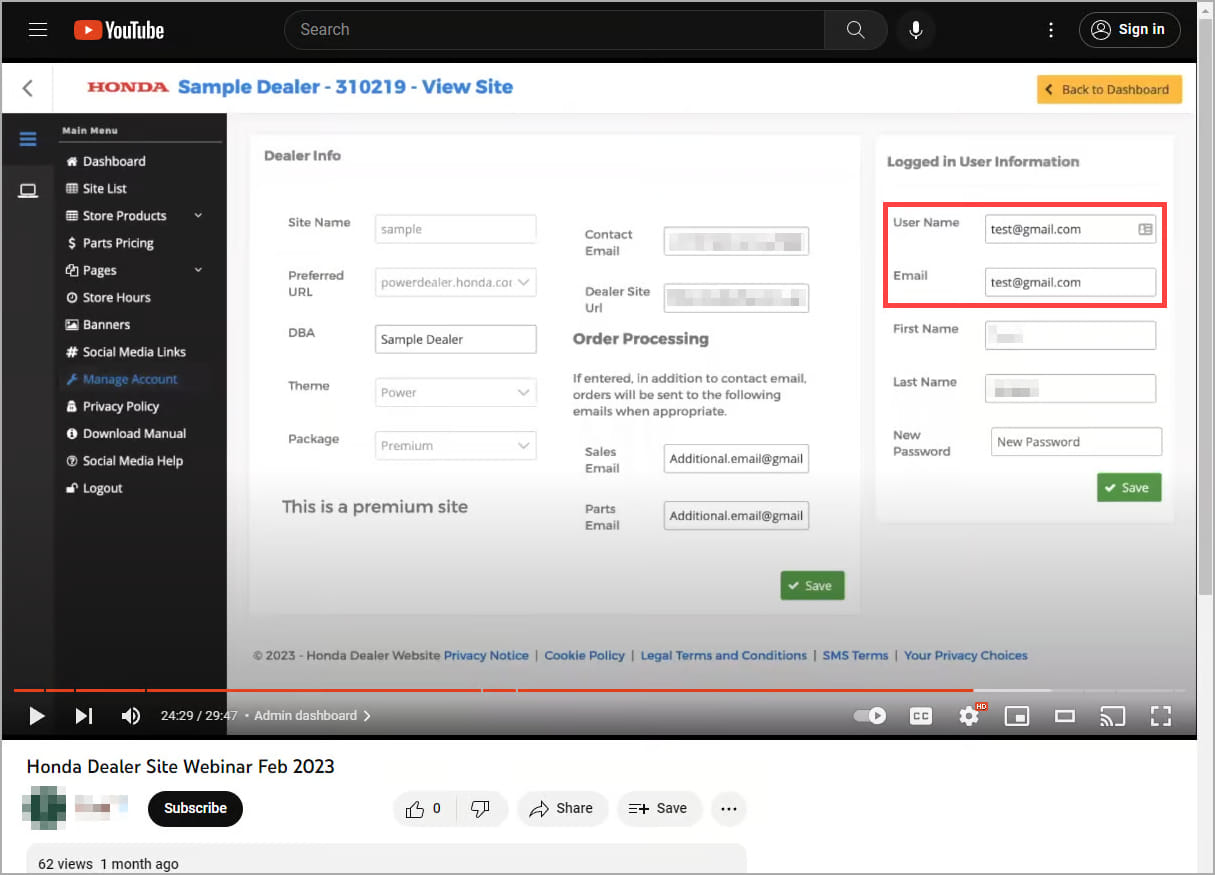
The next step was to access information from real resellers in addition to the test account. However, it would be better to do so without disrupting their operation and without having to reset the passwords of hundreds of accounts.
The solution found by the researcher was to take advantage of a second vulnerability, namely the sequential assignment of user credentials in the platform and the lack of access protections.
This allowed access to all Honda dealer data panels arbitrarily by incrementing the user ID by one until there were no more results.
“Just by incrementing this ID, I could access each dealer’s data. The underlying JavaScript code takes this ID and uses it in API calls to retrieve the data and display it on the page. Fortunately, this discovery made resetting passwords unnecessary.” said eaton works.
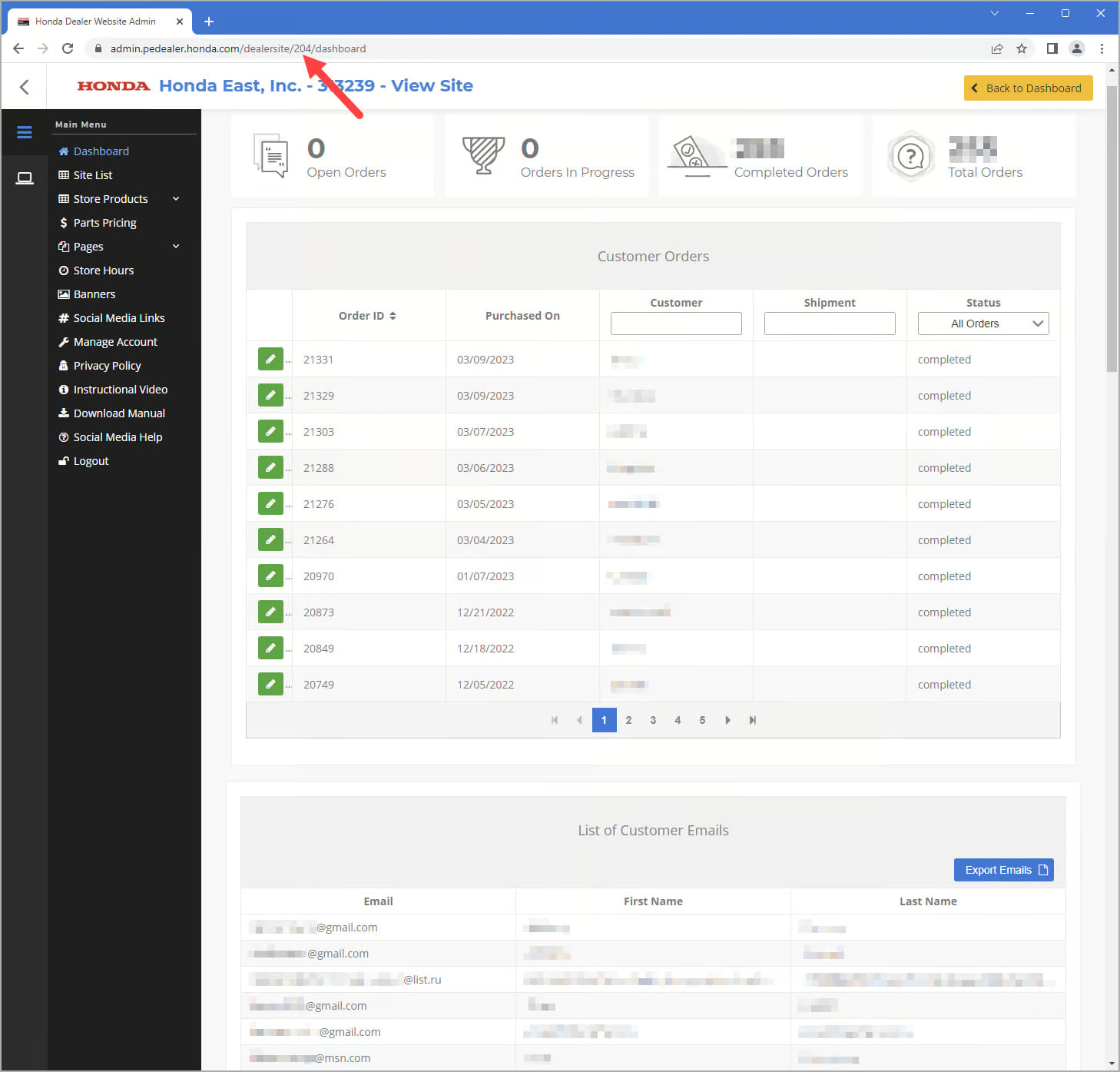
It should be noted that the above flaw could have been exploited by registered Honda dealers to gain access to other dealers’ panels, and by extension, their orders, customer details, etc.
The final stage of the attack involved accessing Honda’s admin panel, which is the central control point for the company’s e-commerce platform.
The researcher accessed it by modifying an HTTP response to make it appear as if he were an administrator, giving him unrestricted access to the Honda Dealer Sites platform.
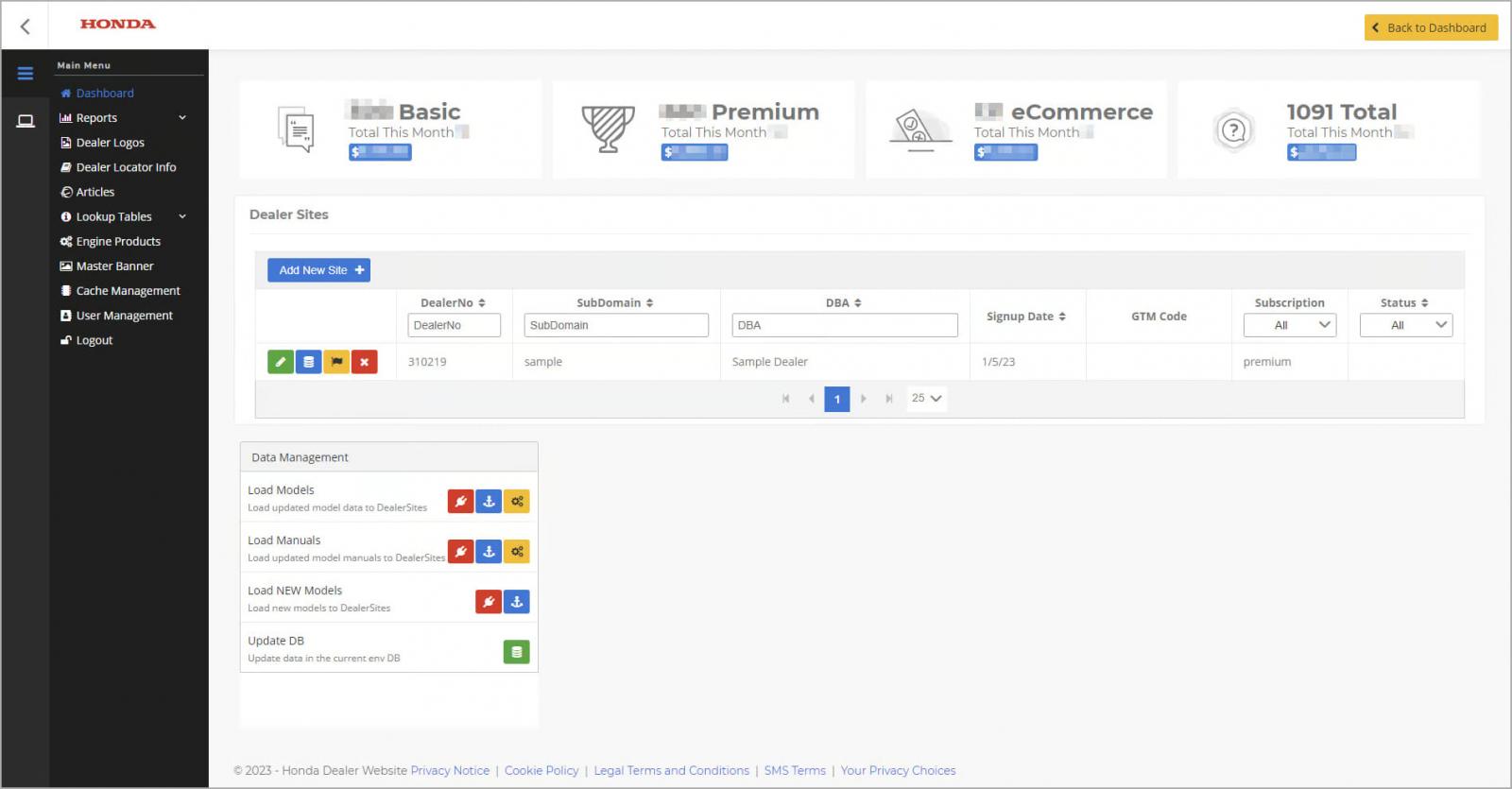
The above was reported to Honda on March 16, 2023 and on April 3, 2023 the Japanese firm confirmed that all issues had been resolved.
Not having a bug bounty program in place, Honda did not reward Eaton Works for responsible reporting, which is the same result as in the Toyota case.
[ad_2]
Source link
