[ad_1]

GitHub warns of an ongoing phishing campaign that began on September 16 and targets its users with emails that impersonate continuous integration and delivery platform CircleCI.
The bogus messages inform recipients that the Terms of Service and Privacy Policy have changed and that they must log in to their GitHub account to accept the changes and continue using the services.
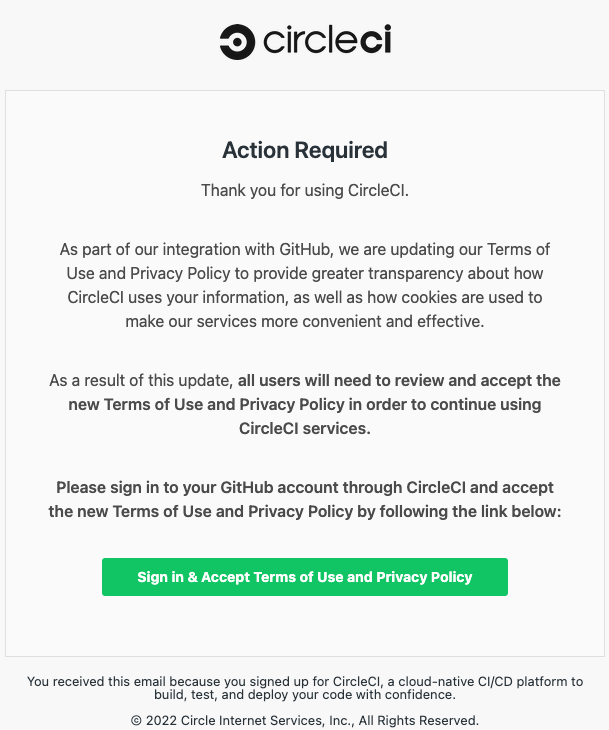
The hackers’ goal is to steal GitHub account credentials and two-factor authentication (2FA) codes by relaying them through reverse proxies.
Accounts protected by hardware security keys for multi-factor authentication (MFA) are not vulnerable to this attack.
“While GitHub itself was unaffected, the campaign did impact many victim organizations,” GitHub advises in a notice Wednesday.
CircleCI also posted a notice on its forums to raise awareness of the malicious campaign, explaining that the platform would never ask users to enter credentials to view changes to its terms of service.
“All emails from CircleCI must only include links to circleci.com or its subdomains,” the CircleCI Reviews.
If you believe that you or a member of your team accidentally clicked on a link in this email, please immediately rotate your credentials for GitHub and CircleCI, and audit your systems for any unauthorized activity.
The phishing domains that distribute the phishing messages try to imitate those of the official CircleCI (circleci.com). So far, the following have been confirmed:
- circle here[.]com
- emails-circleci[.]com
- circle-key[.]com
- email-circleci[.]com
After obtaining valid account credentials, threat actors create Personal Access Tokens (PATs), authorize OAuth applications, and sometimes add SSH keys to the account so that they persist even after a system reset. password.
GitHub Reports see content exfiltration from private repositories almost immediately after compromise. Threat actors use VPN or proxy services to make it harder to track them.
If the compromised account has organization management permissions, hackers create new user accounts and add them to the organization to maintain persistence.
GitHub has suspended accounts where signs of fraud could be identified. The platform has reset the passwords of affected users, who will see personalized notifications about the incident.
If you have not received a notice from GitHub but have reasonable grounds to believe that you may be a victim of the phishing campaign, the recommendation is to reset your account password and 2FA recovery codes , review your PATs and, if possible, start using an MFA hardware key.
GitHub also lists these security checks which all users should perform regularly to ensure that stealthy hackers have not compromised their accounts.
[ad_2]
Source link
