[ad_1]

Microsoft says Linux and Internet of Things (IoT) devices exposed to the Internet are being hijacked in brute force attacks as part of a recently observed cryptojacking campaign.
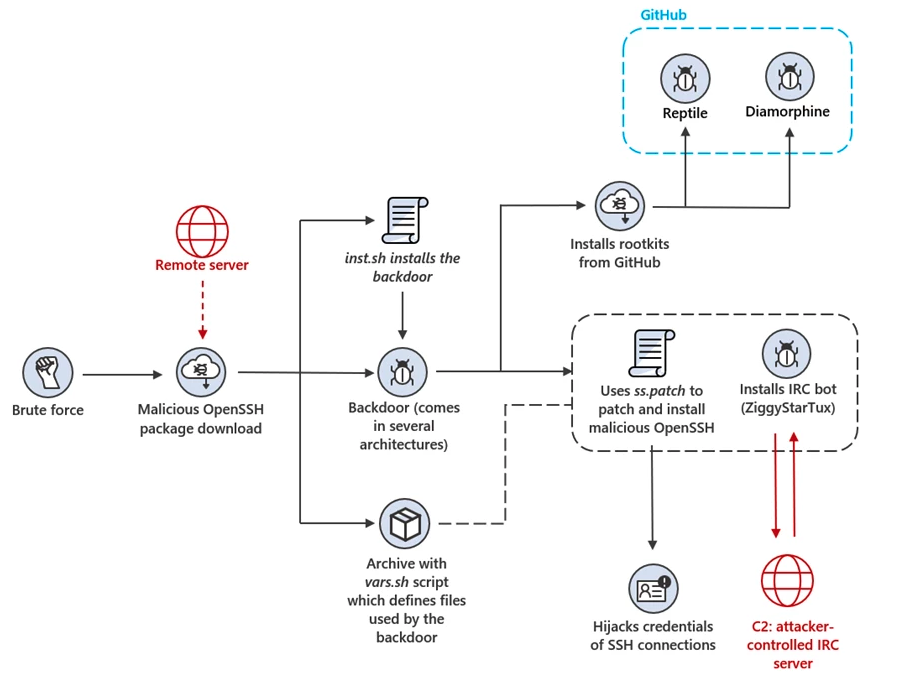
After gaining access to a system, attackers deploy an OpenSSH package containing a Trojan that helps them outwit compromised devices and steal SSH credentials to maintain persistence.
“The patches install hooks that intercept the device’s SSH login passwords and keys, whether as a client or server”, Microsoft said.
“Additionally, the patches enable root login via SSH and conceal the presence of the intruder by suppressing logging of SSH sessions of threat actors, which are distinguished by a special password.”
The backdoor shell script deployed alongside the trojanized OpenSSH binary will add two public keys to the authorized_keys file for persistent SSH access.
It further allows threat actors to harvest system information and install Reptile And Diamorphine open source LKM rootkits to hide malicious activity on hacked systems.
Threat actors are also using the backdoor to eliminate other miners by adding new iptables rules and entries to /etc/hosts to remove traffic to hosts and IP addresses used by cryptojacking competitors from the operation .
“It also identifies miner processes and files by name and terminates or blocks access to them, and removes SSH access configured in authorized keys by other adversaries,” Microsoft said.
A version of ZiggyStarTux The open-source IRC bot also deployed in the attack has distributed denial-of-service (DDoS) capabilities and allows operators to run bash commands.
The backdoor malware uses several techniques to ensure its persistence on compromised systems, duplicating the binary to multiple disk locations and creating cron jobs to run it periodically.
Additionally, it registers ZiggyStarTux as a systemd service, configuring the service file in /etc/systemd/system/network-check.service.
C2 communication traffic between ZiggyStarTux bots and IRC servers is camouflaged using a subdomain belonging to a legitimate Southeast Asian financial institution hosted on the attacker’s infrastructure.
While investigating the campaign, Microsoft saw the bots instructed to download and run additional shell scripts to brute force each live host into the hacked device’s subnet and outwit all systems vulnerable using the trojanized OpenSSH package.
After moving laterally within the victim’s network, the attackers’ end goal appears to be the installation of mining malware targeting Linux-based Hiveon operating systems designed for cryptocurrency mining.
“The modified version of OpenSSH mimics the appearance and behavior of a legitimate OpenSSH server and therefore may pose a greater challenge for detection than other malicious files,” Microsoft said.
“The patched OpenSSH could also allow threat actors to access and compromise additional devices. This type of attack demonstrates the techniques and persistence of adversaries seeking to infiltrate and control exposed devices.”
[ad_2]
Source link
