[ad_1]

Malware operators are increasingly abusing the Google Ads platform to deliver malware to unsuspecting users looking for popular software products.
Among the products spoofed in these campaigns are Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Office, Teamviewer, Thunderbird and Brave.
Threat actors clone official websites of above projects and distribute trojanized versions of software when users click download button.
Some of the malware delivered to victimized systems in this way include Raccoon Stealer variants, a customized version of Vidar Stealer, and the IcedID malware loader.
BleepingComputer recently reported on such campaigns, helping to reveal a massive typosquatting campaign which used over 200 domains masquerading as software projects. Another example is a campaign using fake MSI Afterburner portals to infect users with the RedLine thief.
However, one missing detail was how users were exposed to these websites, information that is now known.
Two reports from Guardio Labs and Trend Micro explain that these malicious websites are promoted to a wider audience through Google Ad campaigns.
Abuse of Google Ads
The Google Ads platform helps advertisers promote pages on Google Search, placing them at the top of the results list as advertisements, often above the official project website.
This means that users looking for legitimate software on a browser without an active ad blocker will see the promotion first and are likely to click on it because it closely resembles the actual search result.
If Google detects that the destination site is malicious, the campaign is blocked and the ads are removed. Hackers therefore need to use a trick at this stage to bypass Google’s automated checks.
According to Guardio and Trend Micro, the trick is to direct victims who click the ad to an irrelevant but benign site created by the threat actor and then redirect them to a malicious site posing as the project. software.
.png)
“The moment these ‘disguised’ sites are visited by targeted visitors, the server immediately redirects them to the rogue site and from there to the malicious payload”, explains Guardio Labs in the report.
“These malicious sites are virtually invisible to visitors who do not reach the true promotional stream and present themselves as benign and unrelated sites to crawlers, bots, casual visitors and, of course, managers Google Policy Enforcement” – Guardio Labs
The payload, which comes in ZIP or MSI form, is downloaded from reputable file-sharing and code-hosting services such as GitHub, Dropbox, or Discord’s CDN. This ensures that any antivirus program running on the victim’s machine will not oppose the download.
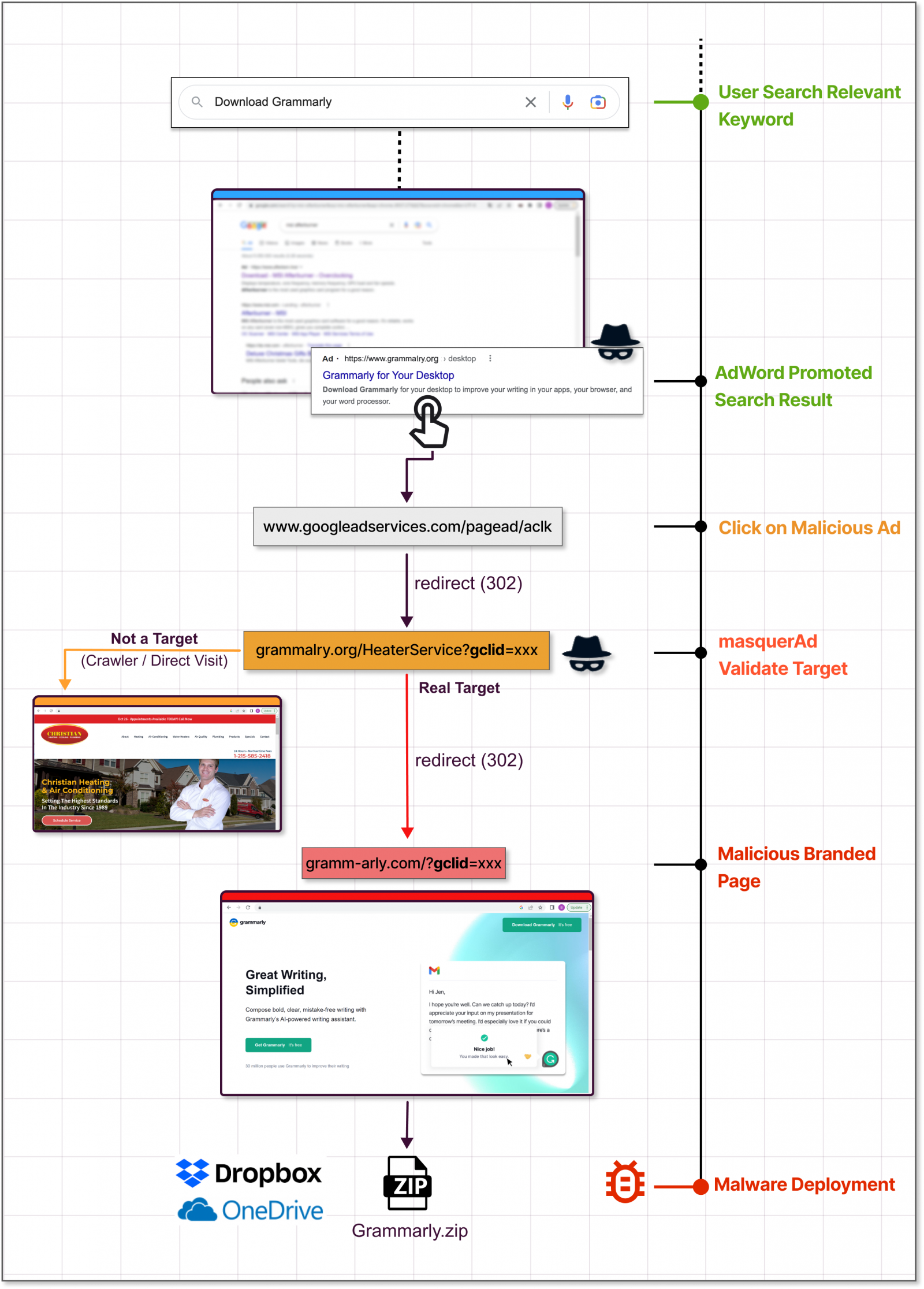
Guardio Labs says that in a campaign they observed in November, the threat actor lured users with a trojanized version of Grammarly that delivered Raccoon Stealer.
The malware was associated with the legitimate software. Users would get what they download and the malware would install silently.
Trend Micro Report, which focuses on an IcedID campaign, claims that threat actors abuse the Keitaro traffic-directing system to detect whether the website visitor is a valid researcher or victim before the redirect occurs. Abuse of this TDS has been seen since 2019.
Avoid harmful downloads
Promoted search results can be tricky because they carry all the signs of legitimacy. The FBI recently issued a warning on this type of advertising campaign, urging Internet users to exercise the greatest caution.
A good way to block these campaigns is to enable an ad blocker in your web browser, which filters out promoted Google search results.
Another precaution would be to scroll down until you see the official domain of the software project you are looking for. If in doubt, the official domain is listed on the software’s Wikipedia page.
If you frequently visit the website of a particular software project to check for updates, it is best to bookmark the URL and use it for direct access.
A common sign that the installer you are about to download might be malicious is an abnormal file size.
Another clear sign of foul play is the domain of the download site, which may look like the official site but has swapped out characters in the name or a single wrong letter, known as “typosquatting”.
[ad_2]
Source link
