[ad_1]
The Emotet malware operation has been spamming malicious emails again since Tuesday morning after a three-month hiatus, rebuilding its network and infecting devices around the world.
Emotet is a notorious malware distributed via email containing malicious attachments of Microsoft Word and Excel documents. When users open these documents and macros are enabled, the Emotet DLL will be downloaded and loaded into memory.
Once Emotet has loaded, the malware will remain silent, awaiting instructions from a remote command and control server.
Eventually, the malware will steal victims’ emails and contacts for use in future Emotet campaigns or download additional payloads such as Cobalt Strike or other malware that usually leads to ransomware attacks.
While Emotet was considered the most distributed malware in the past, it has gradually slowed down, with its last spam operation seen in November 2022. However, even then the spam only lasted for two weeks.
Emotet returns in 2023
Today, the cybersecurity company Cofense and Emotet monitoring group Cryptolaemus warned that the Emotet botnet has resumed sending emails again.
“As of 12:00 UTC, Ivan finally managed to spam E4. We are seeing very large Red Dawn models coming in at over 500MB. We are currently seeing a decent stream of spam. Payload URL Septet and ugly macros”, tweeted Cryptolaemus.
Cofense also confirmed to BleepingComputer that the spam campaign began at 7:00 a.m. ET, with current volumes remaining low.
“The first email we saw was around 7:00 a.m. EST. Volume remains low at this time as they continue to rebuild and gather new credentials to mine and address books to target,” said Cofense to BleepingComputer.
Instead of using response string emails like in the previous campaign, threat actors are using emails that pretend to be invoices as shown below.
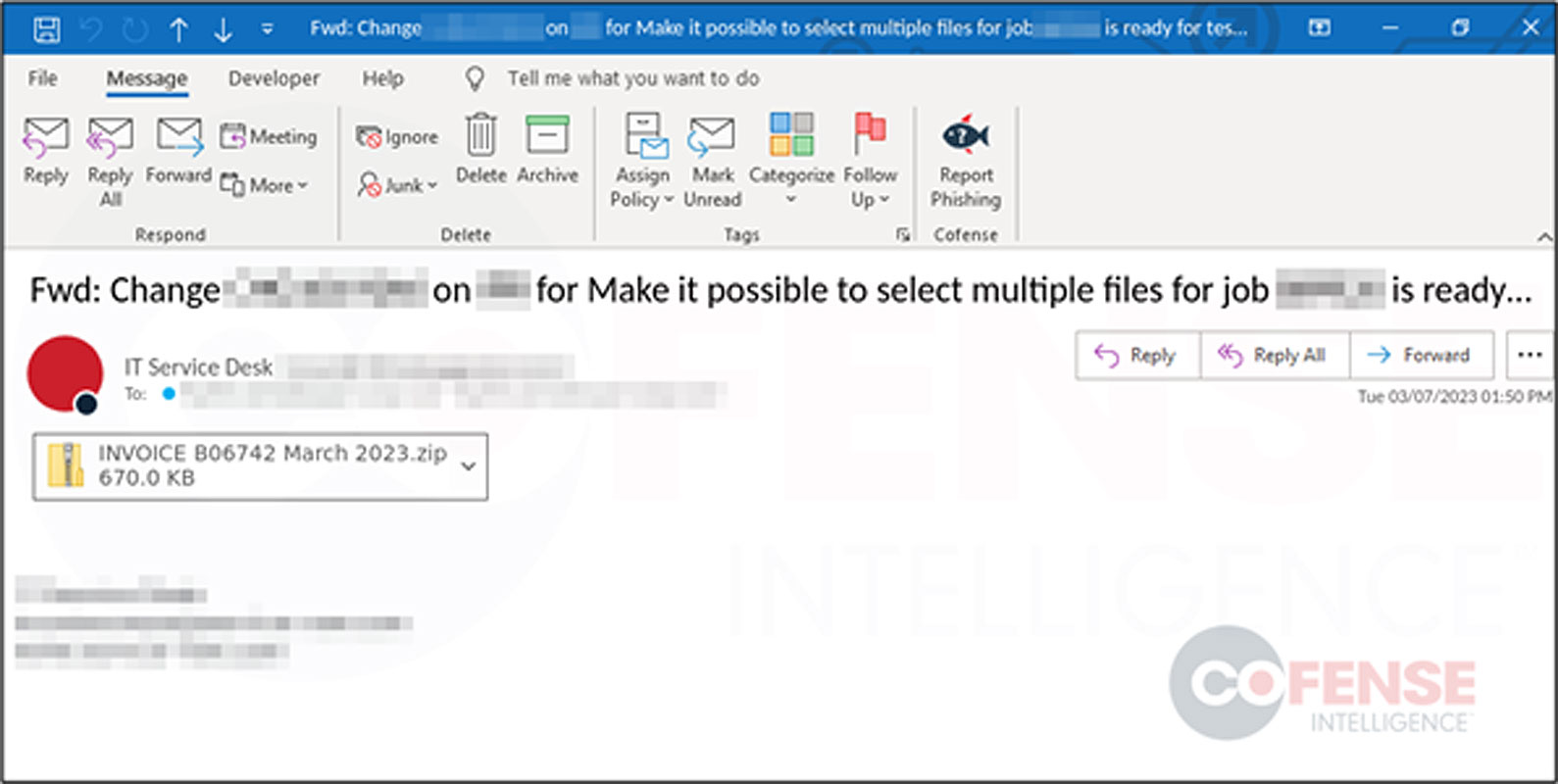
Source: Cofense
Attached to these emails are ZIP archives containing bloated Word documents larger than 500MB. They are bloated to make it harder for antivirus solutions to scan them and detect them as malicious.
These Microsoft Word documents use ‘Red Dawn‘ document template, prompting users to enable document content to see it correctly.
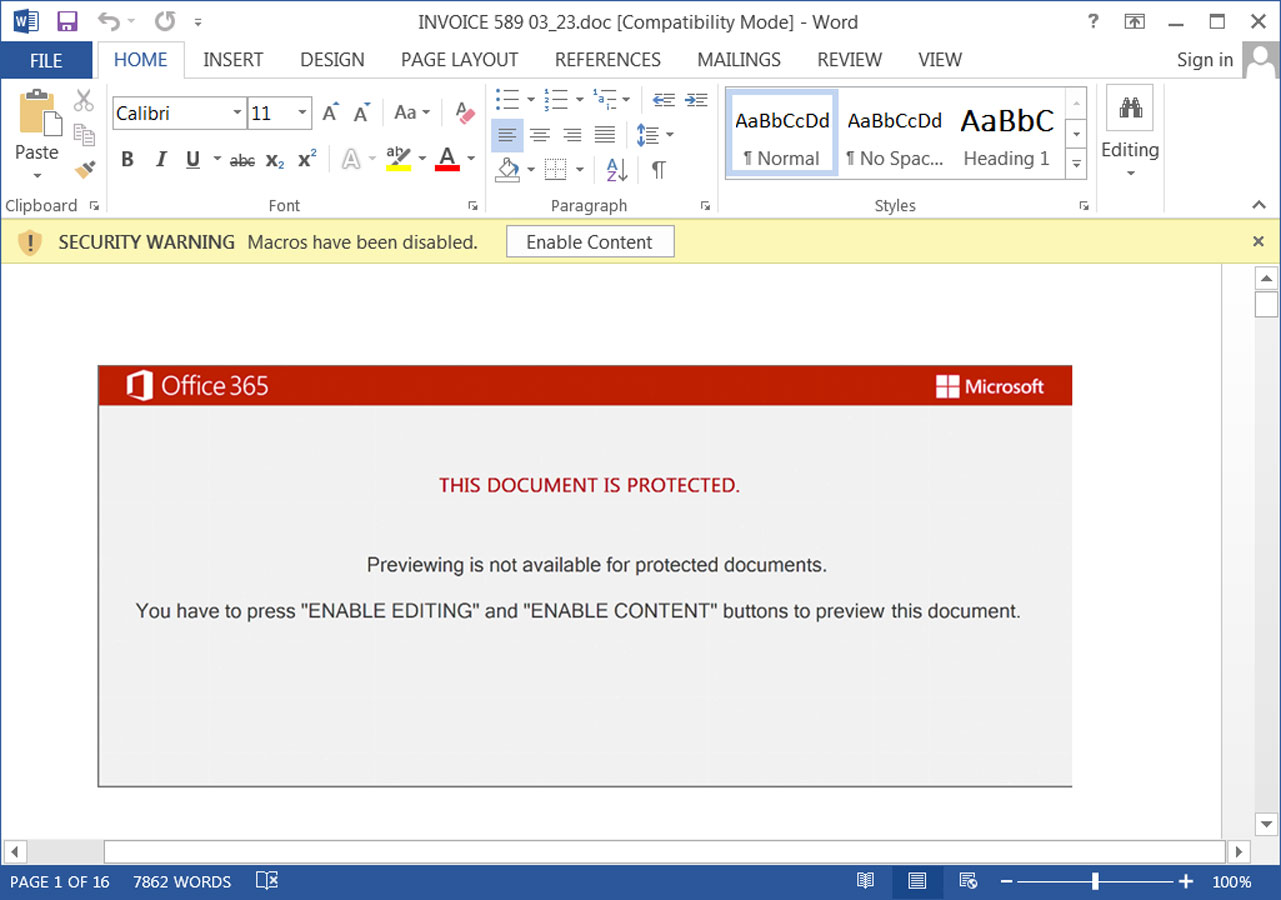
Source: BleepingComputer
These documents contain a bunch of macros that will download the Emotet Loader as DLLs from compromised sites, many of which are hacked WordPress blogs.
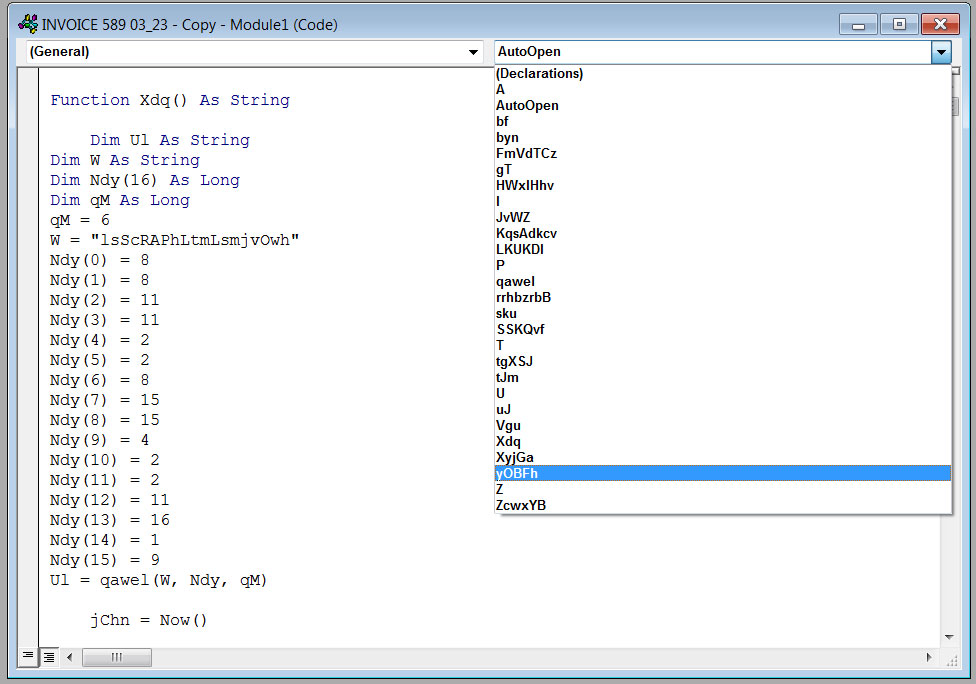
Source: BleepingComputer
Once downloaded, Emotet will be saved in a randomly named folder under %LocalAppData% and launched using regsvr32.exe.
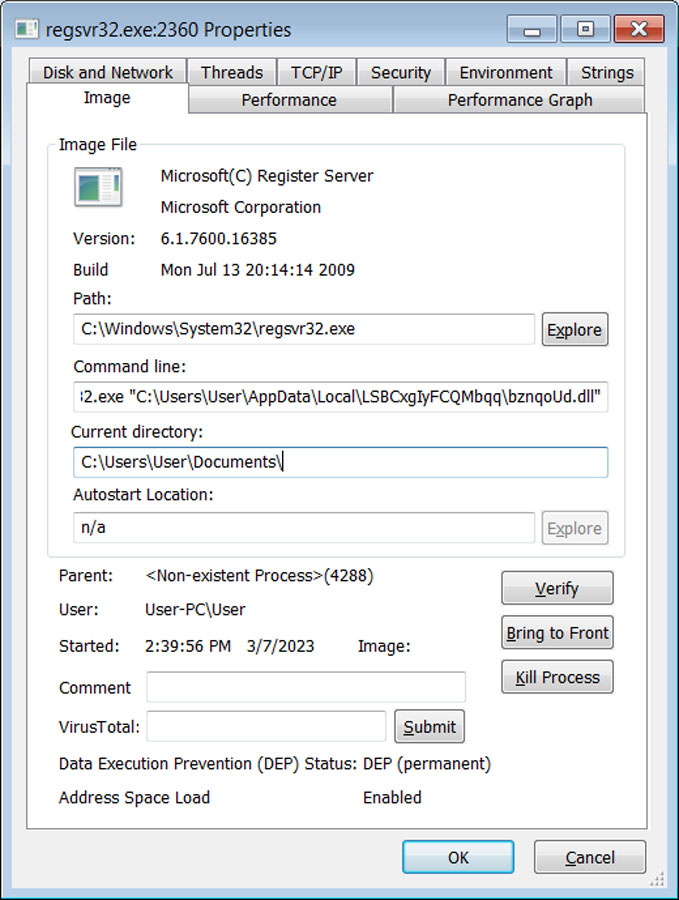
Source: BleepingComputer
Like the Word document, the Emotet DLL was bloated to 526MB to hamper the ability of antivirus software to detect it as malicious.
This evasion technique pays off, as illustrated by a VirusTotal Scan where the malware is only detected by one security vendor out of 64 engines, with that vendor only detecting that it has been inflated.
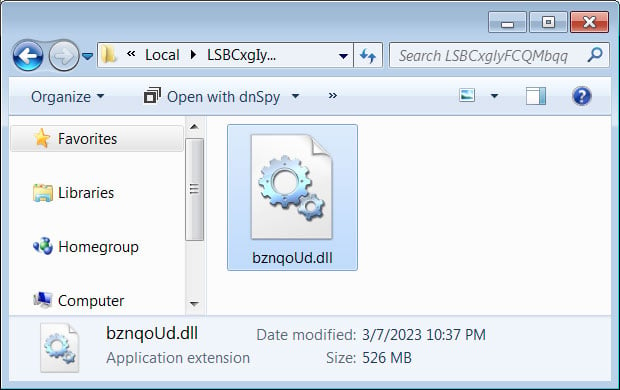
Source: BleepingComputer
Once executed, the malware will run in the background, waiting for commands, which will likely install other payloads on the device.
Payloads allow other threat actors to remotely access the device, which is then used to further spread through the compromised network.
These attacks typically lead to data theft and large-scale ransomware attacks on hacked networks.
Cofense says they haven’t seen any additional payloads dropped now, and the malware is just collecting data for future spam campaigns.
Recent changes from Microsoft save the day
As Emotet rebuilds its network, the current method may not have much success after recent changes from Microsoft.
In July 2022, Microsoft has finally disabled macros by default in Microsoft Office documents downloaded from the Internet.
Due to this change, users opening an Emotet document will be greeted with a message that macros are disabled because the source of the file is untrusted.
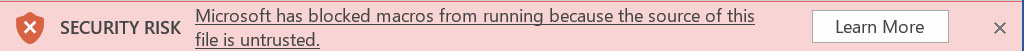
Source: BleepingComputer
ANALYGENCE senior vulnerability analyst, Will Dormantold BleepingComputer that this change also affects attachments saved from emails.
For most users receiving Emotet emails, this feature will likely protect them from mistakenly enabling macros unless they make a concerted effort to enable them.
This shift has led other threat actors to move away from Word and Excel documents and abuse other file formats, like Microsoft OneNoteISO images and JS files.
It wouldn’t be surprising to see Emotet also switch to different types of attachments after this initial campaign didn’t go as planned.
[ad_2]
Source link
