[ad_1]

The Clop ransomware gang has been looking for ways to exploit a now patched zero-day in the managed file transfer (MFT) solution MOVEit Transfer since 2021, according to security experts at Kroll.
When analyzing logs on compromised networks of some customers while investigating recent Clop data theft attacks targeting vulnerable MOVEit Transfer instances, they found malicious activity matching the method the gang used to deploy the new LemurLoot web shell.
“Activity during the period of May 27-28 appeared to be a chain of automated exploit attacks that ultimately culminated in the deployment of the human2.aspx web shell. The exploit centered on the interaction between two components legitimate MOVEit Transfer files: moveitisapi/moveitisapi.dll and guestaccess.aspx,” Kroll said.
“Kroll’s review of affected customer Microsoft Internet Information Services (IIS) logs found evidence of similar activity occurring in multiple customer environments last year (April 2022) and in some cases as early as July 2021.”
They also discovered that threat actors were testing ways to collect and extract sensitive data from compromised MOVEit Transfer servers as early as April 2022, likely using automated tools.
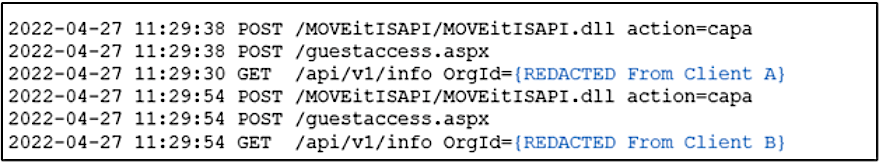
“Kroll observed activity consistent with the MOVEit Transfer exploit that collectively occurred on April 27, 2022, May 15-16, 2023, and May 22, 2023, indicating that the actors were testing access to organizations through means likely automated and removed information from MOVEit Transfer servers to identify which organization they were accessing,” the report reveals.
Automated malicious activity resumed on a much larger scale beginning May 15, 2023, just before the massive zero-day bug exploit began on May 27.
This also matched similar commands issued manually against MOVEit Transfer servers in July 2021, indicating that the ransomware gang waited until they had the tools to launch the final attack in late May 2023.
The servers of “hundreds of companies” have been hacked
Over the weekend, the Clop ransomware gang told Bleepingomputer that they were behind recent data theft attacks which allowed them to breach MOVEit Transfer servers allegedly belonging to “hundreds of companies”.
While the threat actors’ comments cannot be taken at face value, Clop’s statement confirmed a Microsoft report linking the attacks to the hacking group they track as Lace Tempest (also known as the name of TA505 and FIN11).
“Microsoft attributes attacks exploiting CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations and running the Clop extortion site,” Microsoft Threat Intelligence Team tweeted Sunday night.
“The threat actor has used similar vulnerabilities in the past to steal data and extort victims.”
Cybercrime group Clop was also behind other high-impact data theft campaigns targeting other managed file transfer platforms, including zero-day operation of Accellion FTA servers in December 2020, the 2021 SolarWinds Serv-U Managed File Transfer Attacksthe massive exploitation of a zero-day GoAnywhere MFT in January 2023.
Since Clop’s MOVEit data theft attacks were detected, the first organizations that were breached have also slowly started to surface, with UK payroll and HR solutions provider Zellis reporting that they suffered a data breach that will affect probably also some of his clients.
Zellis customers who have already confirmed they have been affected include Irish airline Aer Lingus and British airline British Airways.
Clop threatened all relevant organizations to reach out and negotiate a ransom if they don’t want their data leaked online in six days, June 14.

[ad_2]
Source link
