[ad_1]

The Clop ransomware gang now also uses a malware variant that explicitly targets Linux servers, but a flaw in the encryption system has allowed victims to quietly retrieve their files for free for months.
This new Linux version of Clop was spotted in December 2022 by Antonis Terefos, researcher at Sentinel Labsafter the threat group used it with the Windows variant in an attack on a university in Colombia.
Although very similar to the Windows version, as they both use the same encryption method and almost identical process logic, there are still some differences, mainly limited to operating system API calls and features that await still to be implemented in the Linux variant.
Clop’s Linux malware is also in its early stages, as it still lacks proper obfuscation and evasion mechanisms, and is plagued with flaws that allow victims to recover their files without paying any money. to crooks.
Targeting Oracle database servers
The Linux executable (ELF) of Clop ransomware creates a new process on launch that attempts to elevate permissions to a level that allows data encryption.
The files and folders it targets include the user’s “/home” directory, which contains all personal files, the “/root” directory, “/opt” and the Oracle directories (“/u01” – “/ u04”) used to store database files or as mount points for Oracle software.
Specific targeting of Oracle database folders is not commonly seen in Linux ransomware encryptors, which typically focus on encrypting ESXi virtual machines.
The Linux variant also does not support the hashing algorithm used by the Windows version to exclude certain types of files and folders from encryption. Also, there is no mechanism to treat files of different sizes differently in Linux.
Other features not present in the Linux version of Clop include no drive enumeration, which would help find the starting point for encrypting folders recursively, and command line parameters to provide control extra on the encryption process.
Encryption flaws
The current version of Linux will also not encrypt RC4 keys used for file encryption with the RSA-based asymmetric algorithm used in the Windows variant.
Instead, in the Linux version, Clop uses a hard-coded RC4 “master key” to generate the encryption keys, then uses the same key to encrypt it and store it locally on file. Moreover, the RC4 key is never validated, whereas under Windows, it is validated before launching the encryption.
This weak scheme does not protect the keys from being freely retrieved and the encryption from being reversed, which SentinelLabs did (a Python script that does exactly that is now available on GitHub).
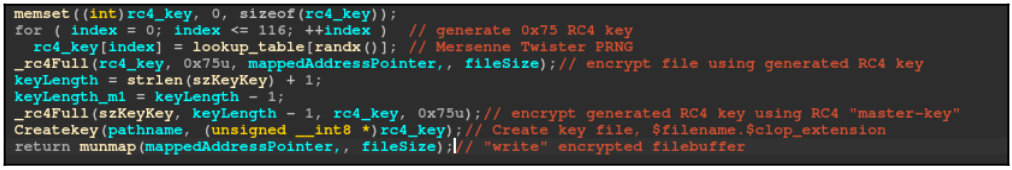
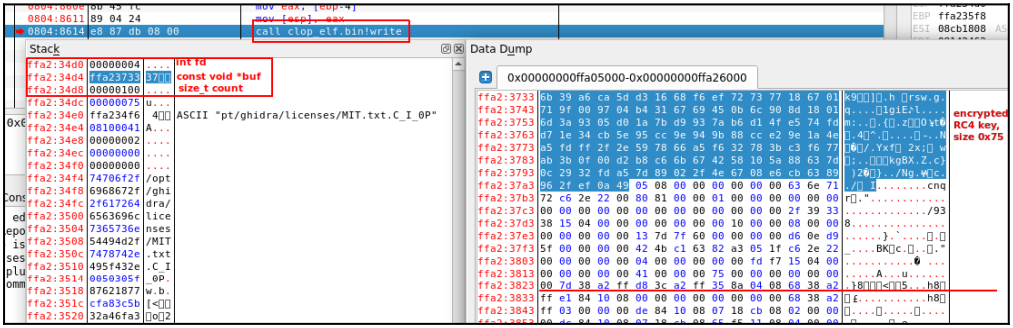
In addition to the lack of key security, SentinelLabs also found that when the encrypted key is written to a file, the malware also writes additional data, such as details about the file, such as its size and time of encryption. .
This data should be concealed, as it could help forensic specialists perform targeted decryption of specific and valuable files.
Clop ransomware for Linux is unlikely to become a widespread threat in its current form. The release of a decryptor will likely cause its authors to release secure and enhanced versions with an appropriate encryption scheme.
SentinelLabs told BleepingComputer that they shared their decryptor with law enforcement, so they could help victims recover their files.
“We shared our findings early on with relevant law enforcement and intelligence partners and will continue to work with relevant organizations to affect the economy of the ransomware space in favor of defenders,” said SentinelLabs at BleepingComputer.
Despite its weaknesses, the use of the Linux variant in actual Clop attacks demonstrates that, for threat actors, having a Linux version, even one that is easy to compromise, is still better than not being able to attack Linux systems within target organizations.
[ad_2]
Source link
