[ad_1]

The “Classiscam” scam-as-a-service operation has broadened its reach worldwide, targeting many more brands, countries, and industries, causing more significant financial damage than before.
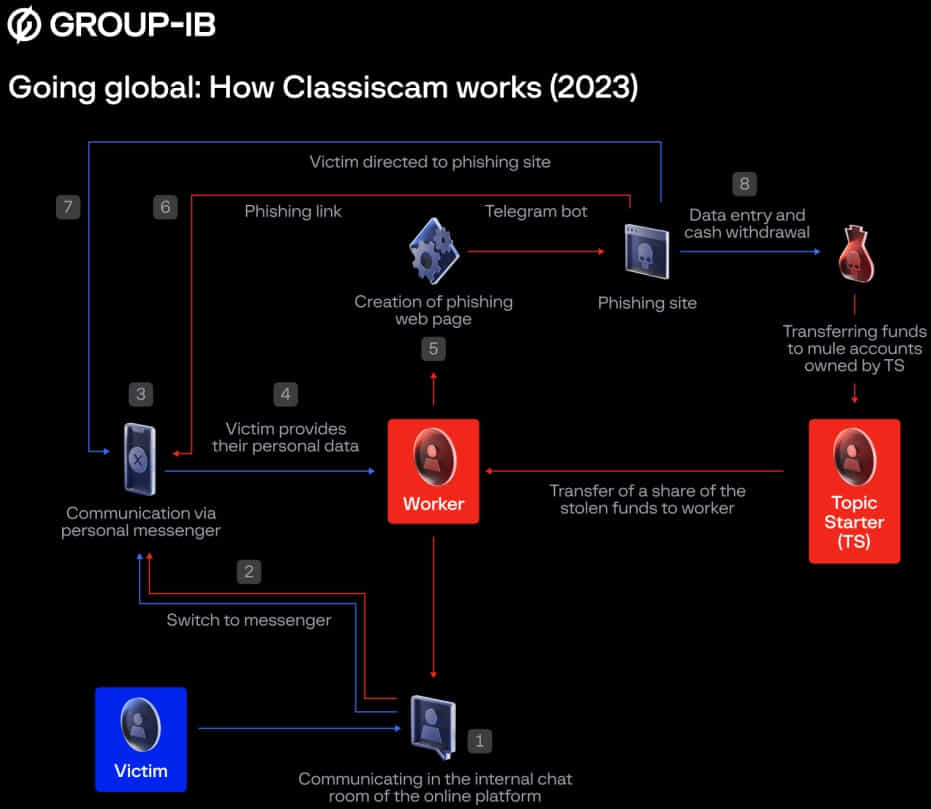
Like a ransomware-as-a-service operation, this Telegram-based operation recruits affiliates who use the service’s phishing kits to create fake ads and pages to steal money, credit card information, and, more recently, banking credentials.
The developers then split any proceeds with the affiliate, with the devs receiving 20-30% of the revenue and the affiliate receiving the rest.
The criminal platform was first discovered by Group-IB in 2019, with the researchers reporting it grew quickly, used by 40 cybercrime gangs that made $6.5 million throughout 2020.
In 2021, Classiscam’s operational scale grew further to include 90 Telegram channels selling the scam kits, 38,000 registered members, and an estimated total damage of $29 million.
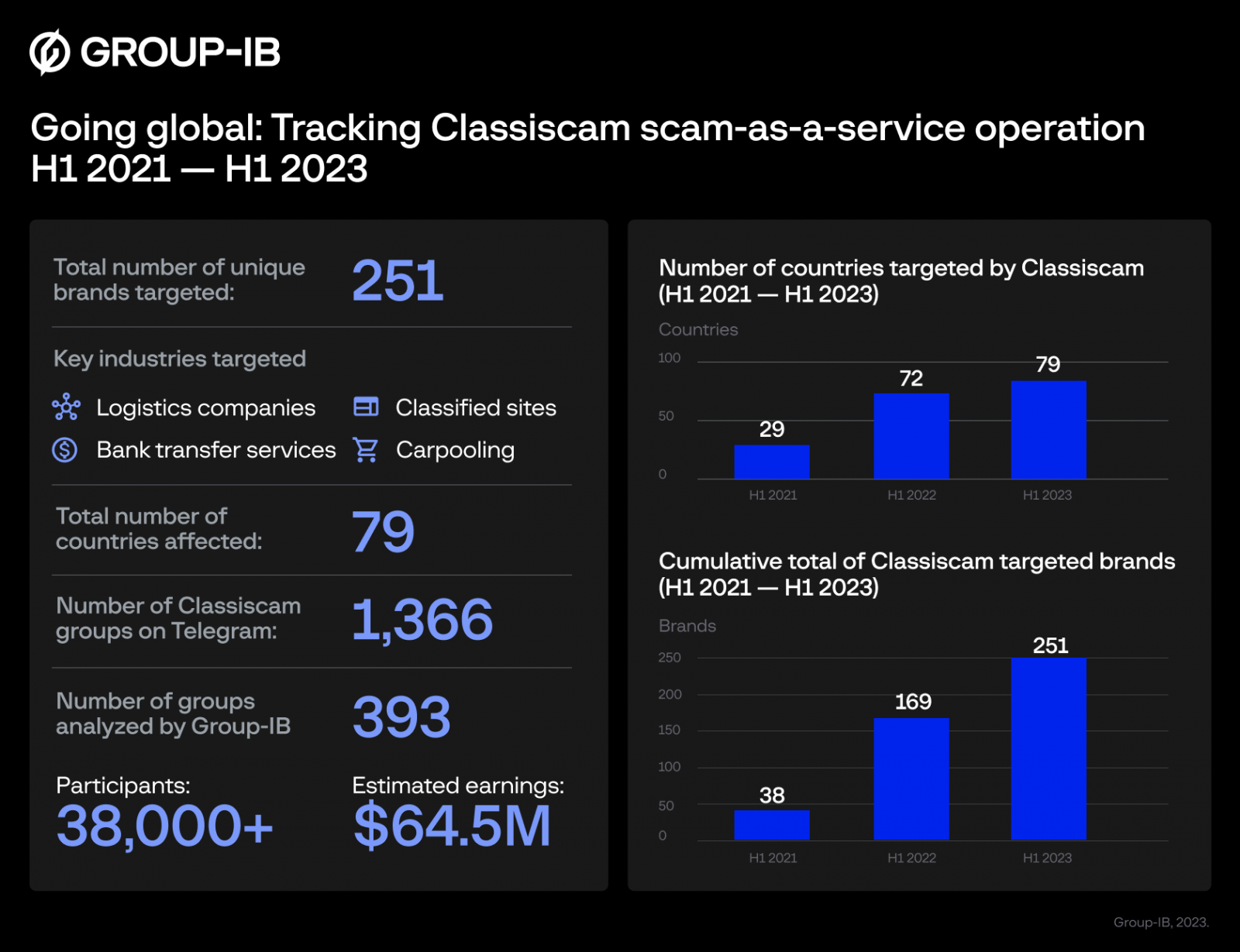
Group-IB has published new information on the operation today, reporting that Classiscam has made $64.5 million in combined earnings from scamming users of classifieds sites and stealing their money and payment card details.
The number of targeted brands has also grown from 169 brands last year to 251 this year, and there are now 393 criminal gangs targeting users in 79 countries, coordinating in one of the operation’s 1,366 Telegram channels.
The highest targeting focus is reserved for Europe, where Germany tops the list with the most prolific victims, followed by Poland, Spain, Italy, and Romania.
Internet users from the UK lost the highest average amount per Classiscam transaction, at $865, while the global average stands at $353.
Group-IB reports that Classiscam has become much more automated, using Telegram bots to create phishing and scam ad pages in just a few seconds.
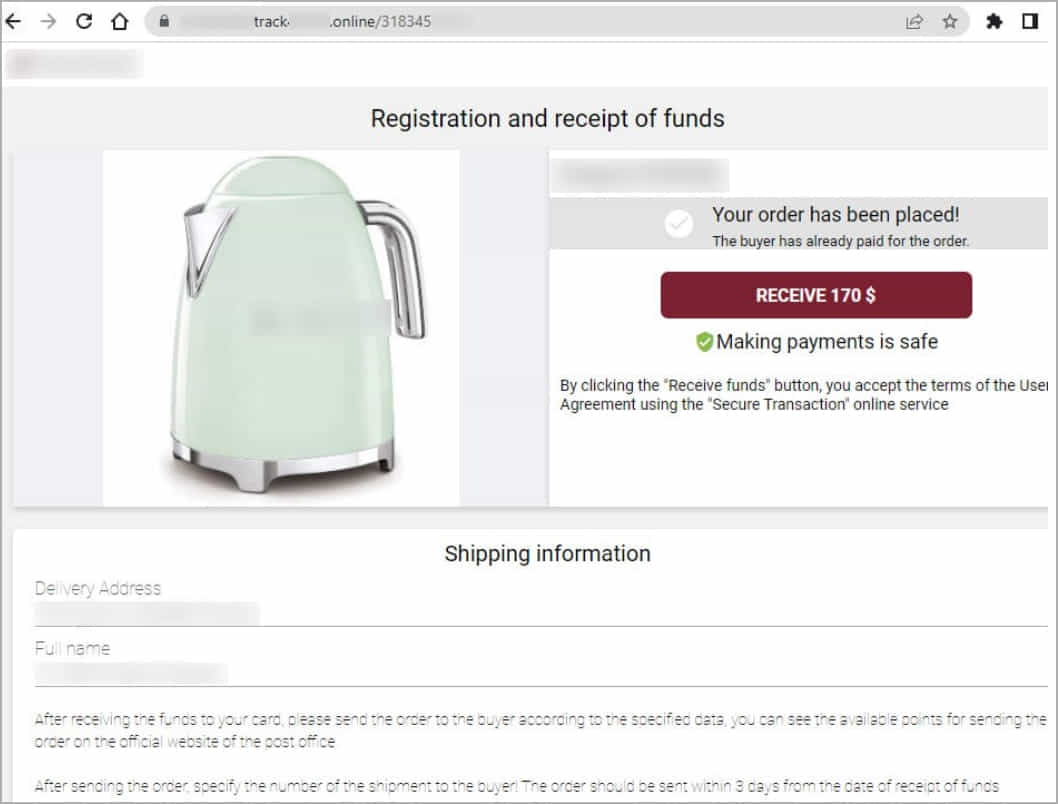
Moreover, the hierarchy of the gangs participating in the operation has become more intricate, and the phishing sites have been greatly enhanced.
Now, the Classiscam phishing sites also perform balance checks to assess the maximum charges they can incur on a victim and feature fake bank login pages to steal people’s e-banking account credentials.
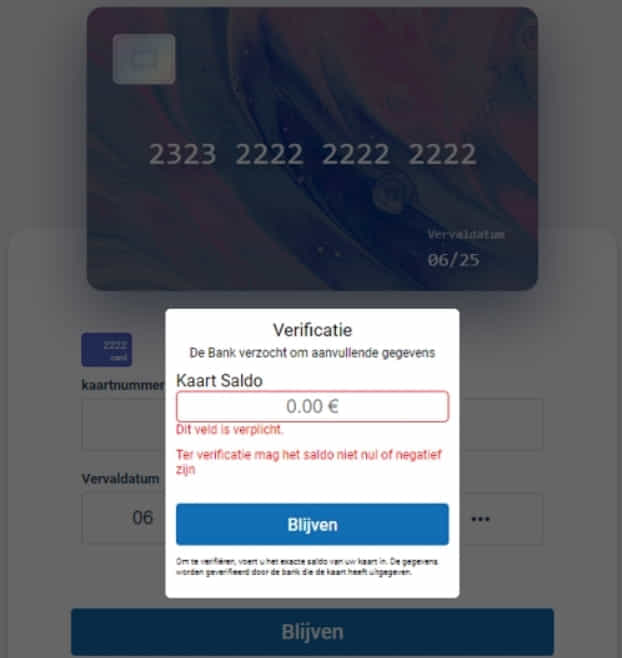
Group-IB’s analysts have seen 35 scam groups using phishing sites that mimic the login pages of 63 banks in 14 countries, including financial institutes in Belgium, Canada, Czech Republic, France, Germany, Poland, Singapore, and Spain.
Unfortunately, the Classiscam operation continues to grow and become more effective in stealing people’s money, which will only encourage more cybercriminals to join its ranks.
Users of classified sites can protect themselves from these scams by never accepting to communicate outside the site’s messaging system, avoiding wiring money to sellers, treating extremely low prices as red flags, and using only secure payment methods that offer fraud protection.
[ad_2]
Source link
