[ad_1]

Bitwarden and other password managers are targeted in Google Ads phishing campaigns to steal users’ password vault credentials.
As business and consumers adopt unique passwords on every site, it has become essential to use password managers to keep track of all passwords.
However, unless you are using a local password manager, like KeePassmost password managers are cloud-based, allowing users to access their passwords through websites and mobile apps.
These passwords are stored in the cloud in “password vaults” which hold the data in an encrypted format, usually encrypted using users’ master passwords.
Recent security vulnerabilities at LastPass and Credential stuffing attacks at Norton illustrated that a master password is a weak point for a password vault.
For this reason, malicious actors have been spotted creating phishing pages that target your Password Vault login credentials, potentially authentication cookies, because once they gain access , they have full access to your vault.
Bitwarden Users Targeted by Google Ads Phishing
On Tuesday, Bitwarden users started seeing a Google ad titled “Bitward – Password Manager” in search results for “bitwarden password manager.”
Although BleepingComputer was unable to reproduce this ad, it was seen by Bitwarden users on Reddit [1, 2] and the Bitward Forums.
The domain used in the ad was “appbitwarden.com” and when clicked, users were redirected to the “bitwardenlogin.com” site.
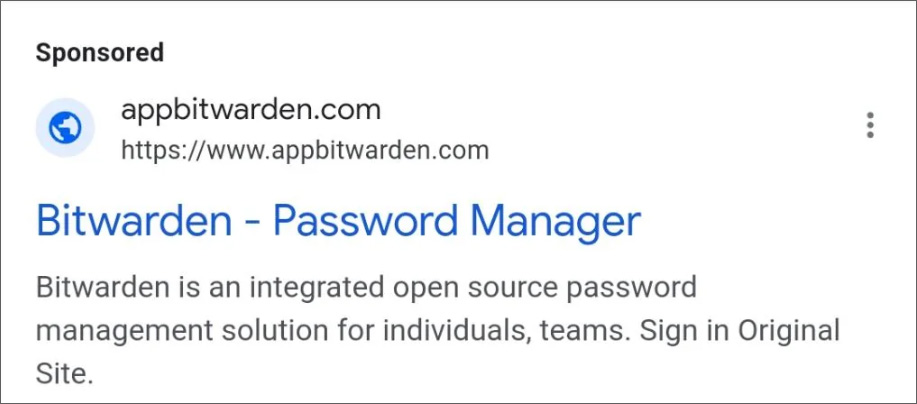
Source: Reddit
The page on ‘bitwardenlogin.com’ was an exact replica of the legitimate Login to Bitwarden Web Vault page, as shown below.
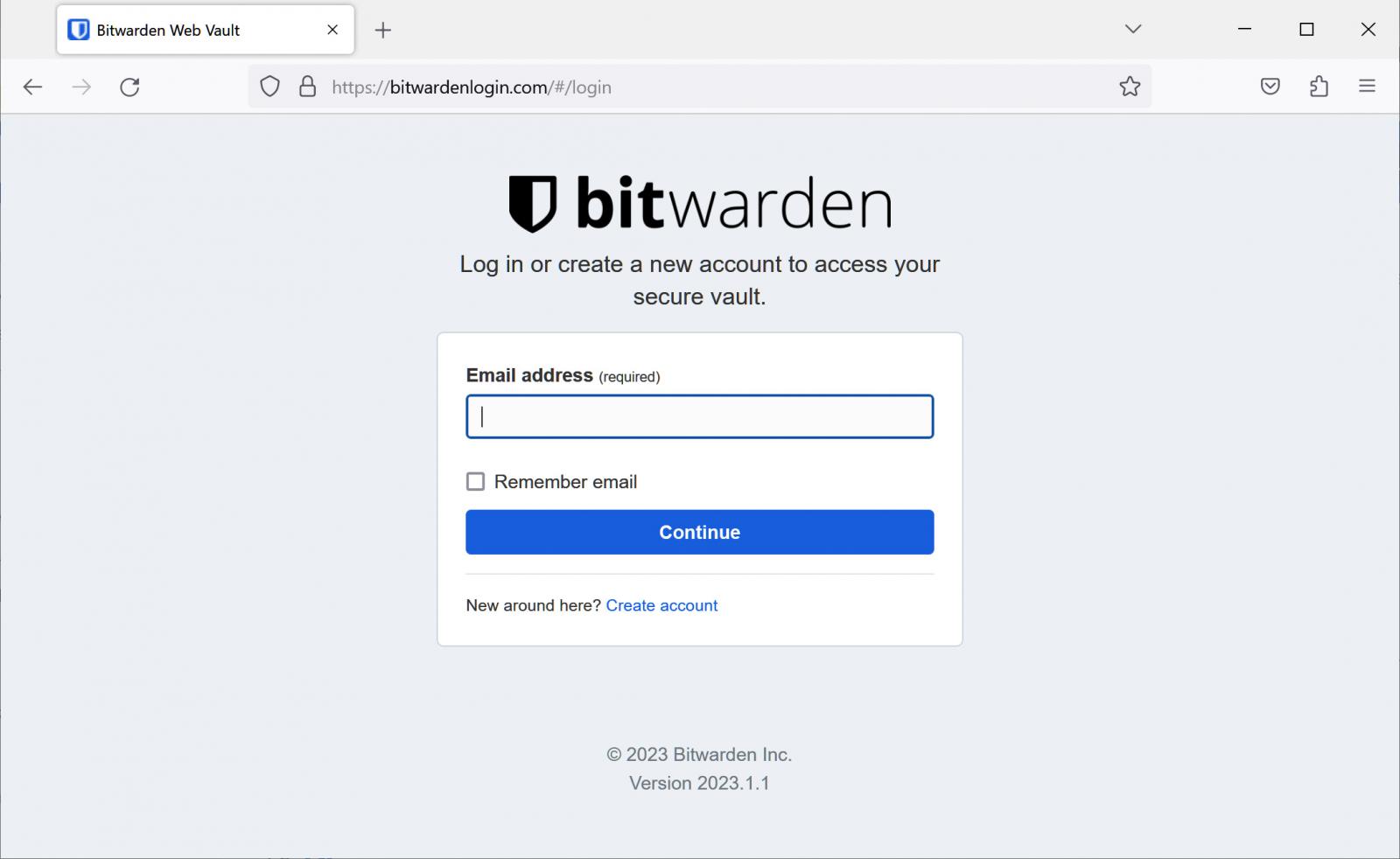
Source: BleepingComputer
In our testing, the phishing page will accept credentials and, when submitted, redirect users to the legitimate Bitwarden login page.
However, our initial tests used fake credentials and the page was closed the moment we started testing with real Bitwarden test login credentials.
Therefore, we could not see if the phishing page would also attempt to steal MFA-backed session cookies (authentication tokens) like many advanced phishing pages.
While many people thought the URL was a dead giveaway that it was a phishing page, others couldn’t tell if it was fake or not.
“Good God. In situations like this, how can I detect the fake? It’s really scary,” said the poster of a Reddit topic about the phishing page.
“People say look at the URL, maybe it’s just my little brain but I can’t tell which one is the real one,” another user commented on the same Reddit post.
To make matters worse, it’s not just Bitwarden that is being targeted by malicious phishing pages in Google Ads.
Security researcher MalwareHunterTeam also recently found google ads targeting credentials for the 1Password password manager.
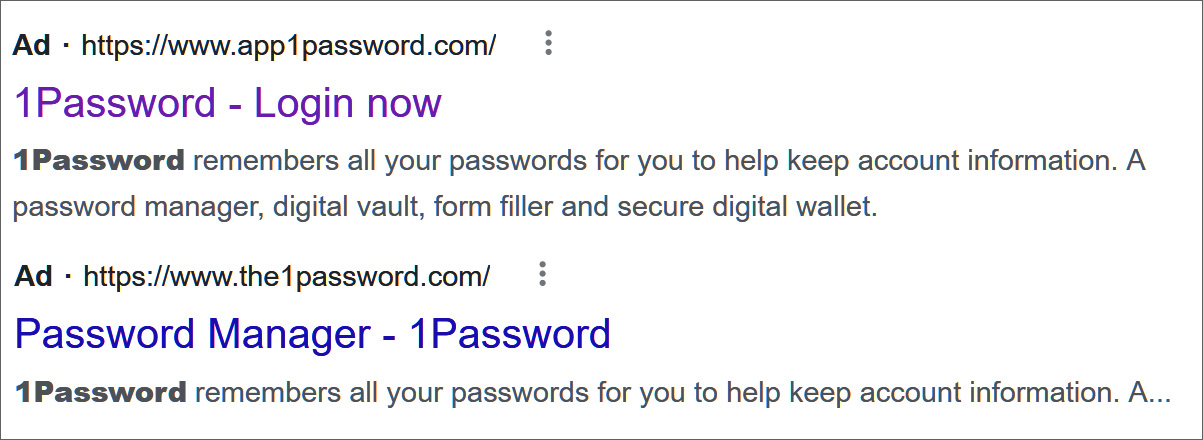
Source: MalwareHunterteam
BleepingComputer was unable to find any other ads targeting other password managers, but Google search results ads have become a huge cybersecurity issue lately.
Recent research has shown that threat actors use Google ads to power their malware delivery campaigns for initial access to corporate networks, steal credentialsand for phishing attacks.
Protect your password safes
With password safes containing some of your most valuable online data, it’s important to protect them properly.
When it comes to protecting your password vaults from phishing attacks, the first line of defense is always to confirm that you are entering your credentials on the correct website.
However, if you mistakenly enter your credentials on a phishing site, you must always configure multi-factor authentication with your password manager.
The best MFA verification methods to use when securing your account, from best to worst, are hardware security keys (best but heaviest), an authenticator app (good and easier to use), and SMS verification (can be hacked in sim swap attacks).
Unfortunately, even with MFA protection, your accounts can still be vulnerable to advanced adversary-in-the-middle (AiTM) phishing attacks.
AiTM phishing attacks occur when threat actors use specialized toolkits such as evilginx2, Modlishkaand moray eel to create phishing landing pages that link to legitimate login forms to a targeted service.
Using this method, visitors to the phishing page will see the login form for a legitimate service, such as Microsoft 365. When they enter their credentials and MFA verification codes, this information is also passed to the real site.
However, once a user logs in and the legitimate site sends the MFA-backed session cookie, the phishing toolkit can steal those tokens for later use.
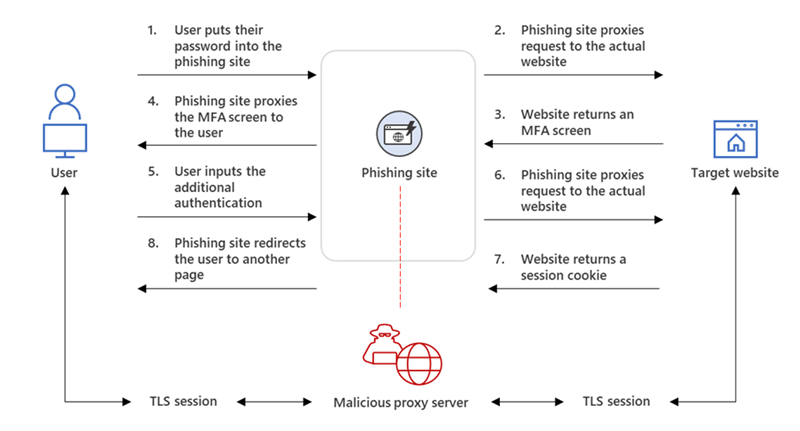
Source: BleepingComputer
Since these tokens have already been verified through MFA, they allow threat actors to log into your account without verifying MFA again.
Microsoft warned in July that this type of attack was used to bypass multi-factor authentication for 10,000 organizations.
Unfortunately, that brings us back to the first line of defense – make sure you only enter your credentials on a legitimate website or mobile app.
[ad_2]
Source link
