[ad_1]

The Xenomorph Android malware has released a new version that adds significant capabilities for conducting malicious attacks, including a new Automated Transfer System (ATS) framework and the ability to steal credentials from 400 banks.
Xenomorph was first spotted by ThreatFabric in February 2022, which discovered the first version of the banking Trojan on the Google Play Store, where it amassed over 50,000 downloads.
This first version targeted 56 European banks using injections for overlay attacks and abusing Accessibility Services permissions to perform notification interception to steal one-time codes.
The development of the malware continued throughout 2022 by its authors, “Hadoken Security”, but its new versions were never distributed in large volumes.
Instead, Xenomorph v2, which was released in June 2022, had only short periods of testing activity in the wild. However, the second version stood out for its complete code overhaul, which made it more modular and flexible.
Xenomorph v3 is much more capable and mature than previous versions, capable of automatically stealing data including credentials, account balances, performing banking transactions and finalizing fund transfers.
“With these new features, Xenomorph is now able to automate the entire fraud chain, from infection to fund exfiltration, making it one of the most advanced and trusted Android Malware Trojans around. more dangerous in circulation,” warns ThreatFabric.
ThreatFabric Reports that it is likely that Hadoken plans to sell Xenomorph to carriers through a MaaS (malware as a service) platform, and the launch of a website promoting the new version of the malware reinforces this hypothesis.
Currently, Xenomorph v3 is distributed through the “Zombinder” Platform on the Google Play Store, posing as a currency converter and switching to using a Play Protect icon after installing the malicious payload.
New xenomorph targets
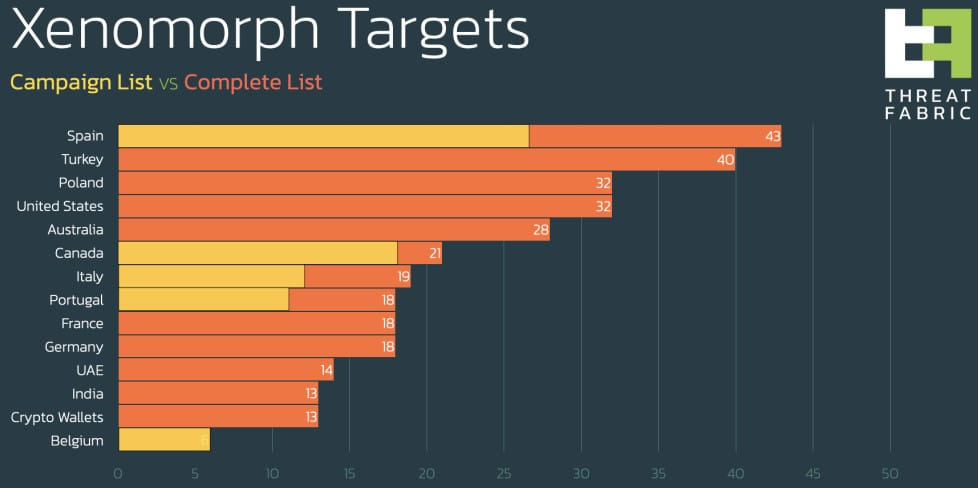
The latest version of Xenomorph targets 400 financial institutions, mainly from the United States, Spain, Turkey, Poland, Australia, Canada, Italy, Portugal, France, Germany, Arab Emirates United and India.
Some examples of targeted institutions include Chase, Citibank, American Express, ING, HSBC, Deutsche Bank, Wells Fargo, Amex, Citi, BNP, UniCredit, National Bank of Canada, BBVA, Santander and Caixa.
The list is too long to include here, but ThreatFabric has listed all of the targeted banks in the appendix to its report.
Additionally, the malware targets 13 cryptocurrency wallets, including Binance, BitPay, KuCoin, Gemini, and Coinbase.
Automatic MFA Bypass
The most notable feature introduced in the new Xenomorph release is the ATS framework, which allows cybercriminals to automatically extract credentials, verify account balances, perform transactions, and steal money from target applications without performing any remote actions.
Instead, the operator simply sends JSON scripts which Xenomorph converts into a list of operations and runs them autonomously on the infected device.
“THE [ATS execution] used by Xenomorph stands out from its competitors thanks to the wide selection of possible actions that can be programmed and can be included in ATS scripts, in addition to a system that allows conditional execution and prioritization of actions”, explains the researchers of ThreatFabrics.
One of the most impressive capabilities of the malware’s ATS framework is its ability to log content from third-party authentication apps, defeating MFA (multi-factor authentication) protections that would otherwise block automated transactions.
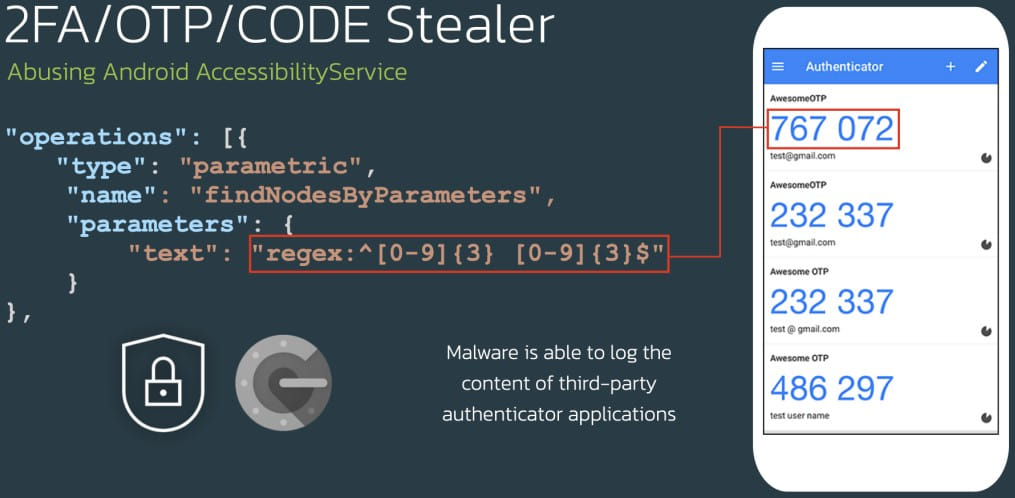
Banks are phasing out SMS MFA and suggesting customers use authenticator apps instead. It is therefore troubling to see Xenomorph’s ability to access these apps on the same device.
cookie thief
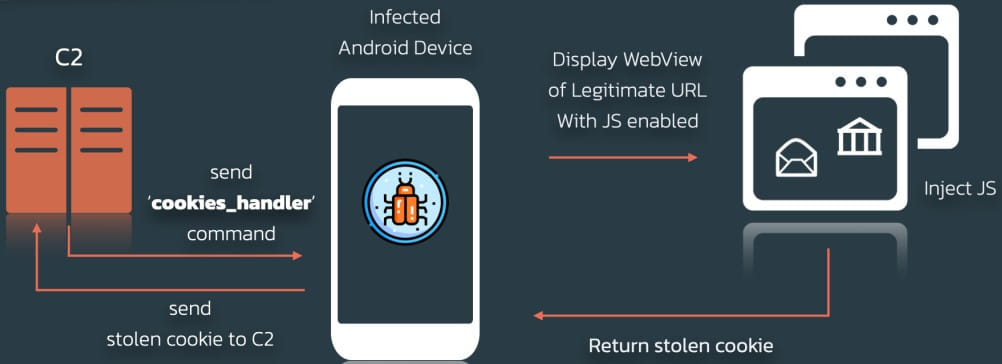
In addition to the above, the new Xenomorph has a cookie stealer that can snatch cookies from Android CookieManager, which stores user session cookies.
The thief launches a browser window with the URL of a legitimate service with the JavaScript interface enabled, prompting the victim to enter their login information.
Threat actors steal the cookie, allowing the victim’s web sessions to be hijacked and gaining control over their accounts.
An Android Malware to Worry About
Xenomorph was a notable new malware that entered the cybercrime space a year ago.
Now, with the release of its third major version, it’s a much bigger threat to Android users around the world.
Given its current distribution channel, the Zombinder, users should be careful with the apps they install from Google Play, read reviews and check the publisher’s track record.
As a general rule, it’s a good idea to keep the number of apps running on your phone to a minimum and only install apps from known and trustworthy vendors.
[ad_2]
Source link
