[ad_1]

A serious security flaw in the Amazon ECR (Elastic Container Registry) public gallery could have allowed attackers to delete any container image or inject malicious code into images from other AWS accounts.
Amazon ECR Public Gallery is a public container image repository used to share out-of-the-box applications and popular Linux distributions, such as Nginx, EKS Distro, Amazon Linux, CloudWatch Agent, and Datadog Agent.
A Lightspin security analyst has discovered a new flaw in the ECR public gallery where it is possible to modify existing public images, layers, tags, registries and repositories of other users by abusing API actions undocumented.
The researcher reported the vulnerability to AWS Security on November 15, 2022, and Amazon deployed a fix within 24 hours.
While there are no signs of this flaw being abused in the wild, threat actors could have used it in large-scale supply chain attacks against many users.
Characteristically, the six most downloaded container images in ECR Public Gallery had over 13 billion downloads, so any malicious injections into them could have resulted in “out of control” infections.
Lightspin says its analysis showed that 26% of all Kubernetes clusters have at least one pod that pulls an image from the ECR public gallery, so the impact could have been significant.
Take advantage of undocumented API actions
The Lightspin researcher discovered that the ECR public gallery has several internal API actions that are used to support specific commands and user actions, but are not publicly exposed.
Four of these API actions, listed below, had no triggers, but were still active on the platform and therefore callable.
- DeleteImageForConvergentReplicationInternal
- RemoveTagForConvergentReplicationInternal
- PutImageForConvergentReplicationInternal
- PutLayerForConvergentReplicationInternal
After finding a way to authenticate to the internal ECR API using temporary Amazon Cognito credentials, the analyst forged malicious API requests that would be granted.
Of course, for the above to work, the request must have a valid JSON structure, and since there was no documentation for these API calls, inferring that it required some experimentation.
In the proof-of-concept example provided in Lightspin’s report, the request uses the “DeleteImage” API call and publicly available image and repository credentials to delete a publicly available image uploaded by the researcher .
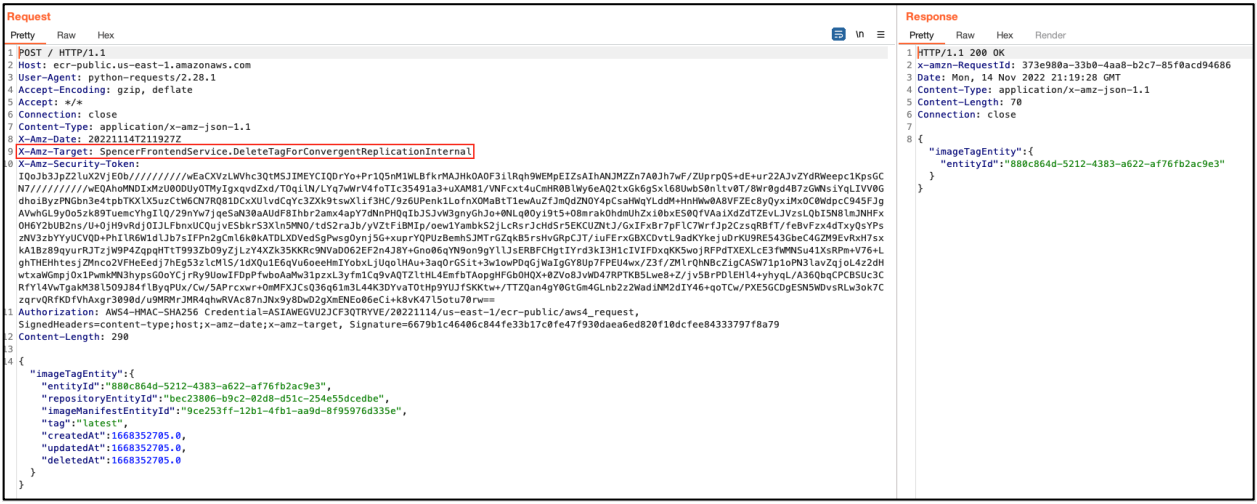
The researcher embedded the exploit steps into a Python script, so the process could have been automated to abuse undocumented API calls to attack public images.
Amazon’s response
Amazon told BleepingComputer that they immediately addressed the issue discovered by Lightspin, and internal investigation found no signs of exploitation by malicious actors.
Based on the logs and evidence reviewed, the internet giant is confident that no customer accounts, downloads or other assets were compromised.
The full statement from Amazon is below:
On November 14, 2022, a security researcher reported an issue in Amazon Elastic Container Registry (ECR) Public Gallery, a public website for finding and sharing public container images. The researcher identified an ECR API action that, if called, could have allowed the editing or deletion of images available on ECR Public Gallery.
On November 15, 2022, the identified issue was resolved. We performed an exhaustive analysis of all logs. We are confident that our review was conclusive and that the only activity associated with this issue was with accounts belonging to the researcher. No other customer accounts were affected and no customer action is required. We would like to thank Lightspin for reporting this issue.
[ad_2]
Source link
