[ad_1]

Interrupted classes, disrupted planning, and postponed events – IT outages have a big impact on modern university life. But as challenging as a typical IT outage may be, ransomware-induced downtime adds a whole new dimension of anxiety for IT teams.
On May 30th, 2023, the University of Waterloo was subject to a ransomware attack against their on-campus Microsoft Exchange email service.
As is typical in ransomware attacks, the University of Waterloo forced staff, faculty, and employee grad students to reset their passwords by June 8th. All non-employee grad students, incoming first-year undergraduates, and all remaining students had to reset their passwords by June 22nd.
Resetting the passwords for 42,000 people and their many connected devices is challenging, to say the least, for any IT team.
Let’s explore why organizations are forced into mass password resets and how to make the process manageable.
The burden mass password resets place on IT teams
As troublesome as a password reset account is for users, it’s helpdesk and IT staff who deal with the burden of hugely increased call volumes and service tickets. A student may often have several devices connected to a given network, and not all will properly authenticate after a password reset.
Walking users through each fix loses valuable time from the many day-to-day tasks IT staff also need to be doing.
In the case of the University of Waterloo, some students and staff may not have even seen the notices despite a widely distributed notification. Though the was lucky that the ransomware attack did not compromise their hosted Microsoft Exchange 365 accounts, students don’t always check their university email during summertime.
Come fall, many students may need assistance logging into university services, placing an already overworked IT helpdesk at the school with an even heavier burden.
As is true for both universities and other types of organizations, people access resources from various devices and locations. With so many different conditions, password resets don’t always work.
Users may need several methods to verify their identity and allow a successful password reset. This results in a lot of work for an IT team, when multiplied across every end user.
When to take the plunge and mass reset passwords
Whether out of an abundance of caution or already compromised systems, the time may come to force a mass reset of everyone’s password in an organization. This decision does not come lightly.
A mass reset may be warranted by weighing the disruption to users and IT staff against the potential cost and destruction of the ransomware itself.
Resetting many user passwords at once can take time. Windows architectures do not offer a built-in method for mass password resets. Through PowerShell scripting, on-premise Active Directory user passwords can be forced to change at the next logon.
If running a hybrid Azure Active Directory and local Active Directory or through integration with other authentication systems such as CAS and SAML systems, the complexity of scripting a mass reset increases quickly. Scripting large password resets in complex IT environments may be a challenge.
Over the years, NIST password recommendations have changed with the current best practices advocating that passwords are not required to be arbitrarily changed (unlike previous recommendations for every 90 or 120 days).
A password change is needed when appearing on a “blacklist of compromised values” (NIST section 5.1.1.1). Though it may not be clear what the compromised credential may be, it would be safe to assume that any account could potentially be compromised, warranting a reset of all accounts.
Many attacks may result in mass password resets, but few attacks are as potentially destructive and time-consuming as ransomware. The breadth and scope that this type of attack means that every user and system could be affected.
Preparing in advance for quick remediation and empowering your users and IT helpdesk with the necessary tools mean that the worst may be mitigated.
How to easily enable users to reset their own passwords
Ideally, a ransomware event doesn’t occur in the first place, but implementing solutions through proactive planning will save the IT staff and users valuable time and resources if it does. In the case of the University of Waterloo, 42,000 students represented a huge number to reset through one-on-one assistance.
Enabling users to reset their own passwords with Specops uReset, would have alleviated a significant burden on the IT helpdesk.
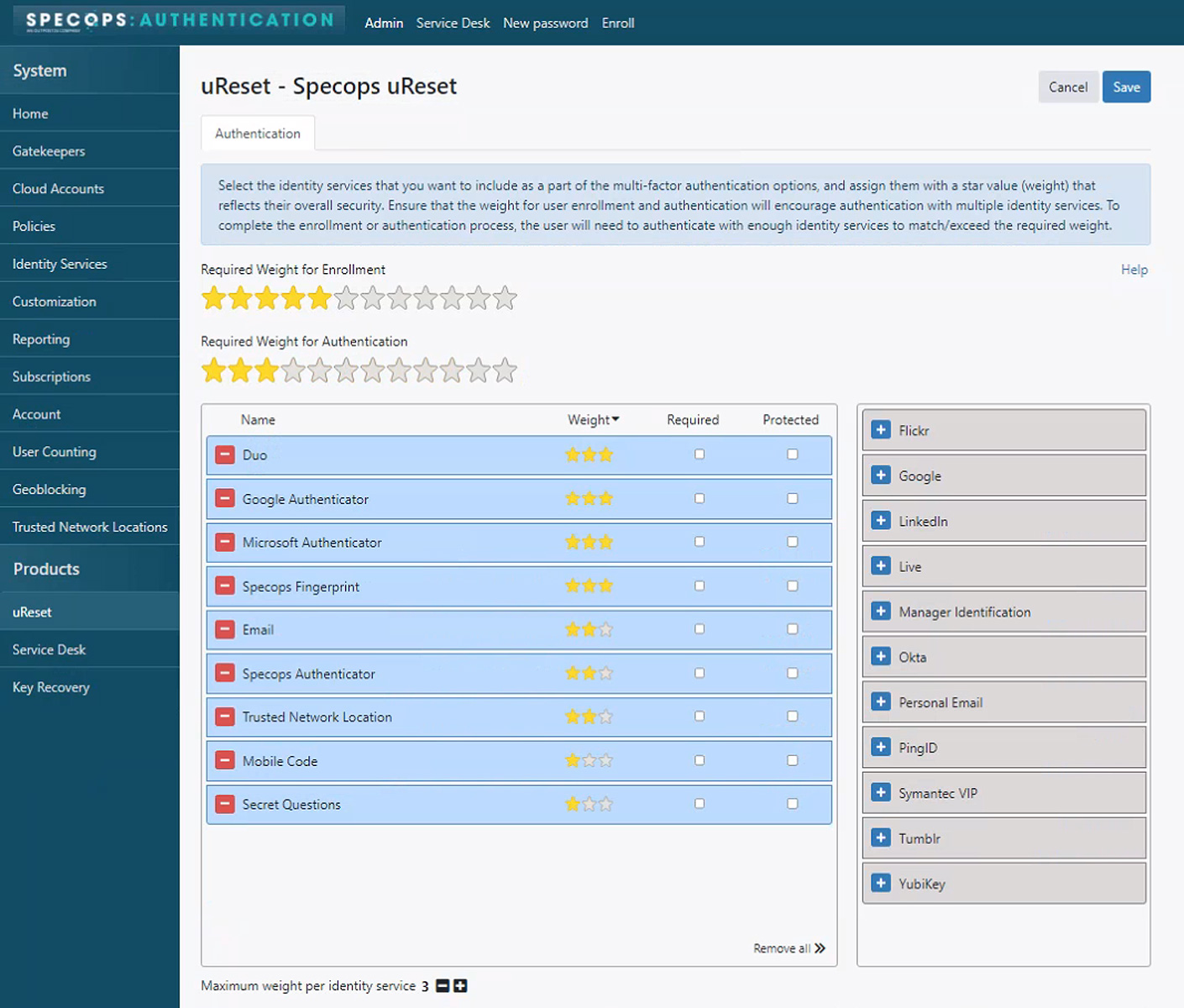
From an administration standpoint an easy guide is provided to set up uReset here. After set up, you can configure the uReset policy mode in these simple steps:
- Move any of the identity services you want to use from the Unselected Identity Services box to the Selected Identity Services
- Assign a weight (star value) for each selected identity service. This will allow you to assign a higher value to those identity services you believe provide a higher level of security.
- To require the user to use a specific identity service, select the Required
- Configure the required weight (stars) for enrollment.
- Configure the required weight (stars) for authentication.
- Click Save when you are done.
- Customize notifications and messages to users and administrators.
- Configure additional settings
uReset provides end users real time feedback at password resets. They will receive a message set up from administration and then take these simple steps at logon:
- Follow the Reset Password link in the Windows Logon screen to authenticate yourself using the identity services in your enrollment.
- Select one identity service at a time and perform the corresponding authentication. You will be authenticated when the star bar is full.
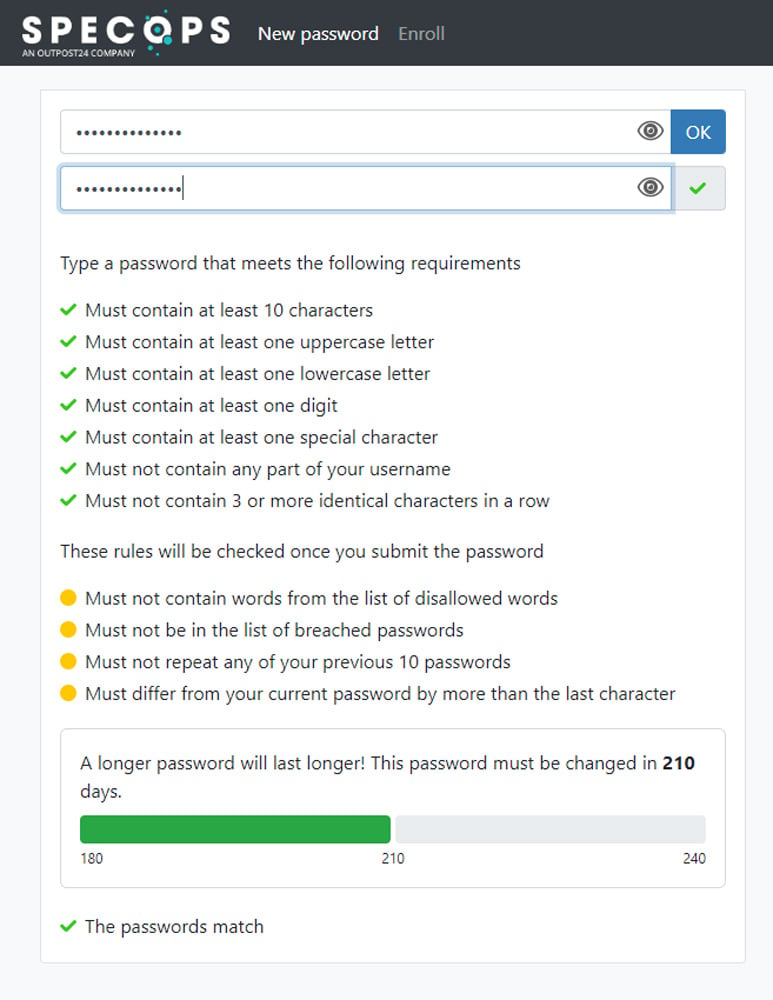
- Once you have identified yourself, you will be prompted to enter a new password.
- As you enter your new password, you will automatically see if you are meeting the complexity requirements of the password.
- The complexity requirements will each contain one of the four colors:
- Green indicates that the complexity requirement has been met
- Red indicates that the complexity requirement has not been met
- Grey indicates that the complexity is an optional requirement.
- Yellow indicates that the complexity requirement is a server side requirement and can only be verified once the password has been submitted
- Submit the password once you have fulfilled the complexity requirements.
Specops uReset integrates with many identity providers such as Duo Security, Okta, etc. No matter how your authentication scheme is configured, Specops uReset likely offers a solution to integrate.
To facilitate ease of password changes, Specops uReset offers integration with the Windows login prompt, which even works with cached credentials and offline domain directory services. This allows users to authenticate themselves and guides them towards creating a strong password that matches your organization’s password policy.
Contact Specops for a free trial of Specops uReset to see how your organization can securely enable end users to reset their own passwords, and in a worst case scenario greatly limit the damage from ransomware.
Sponsored and written by Specops Software
[ad_2]
Source link
