[ad_1]

Administrators of the Genesis Market for Stolen Credentials announced on a hacker forum that they had sold the store and that a new owner would take over “next month”.
This announcement comes about three months after the application of the law grabbed some of the market areas on the clearnet in Operation Cookie Monster.
Genesis Market package sold out in three weeks
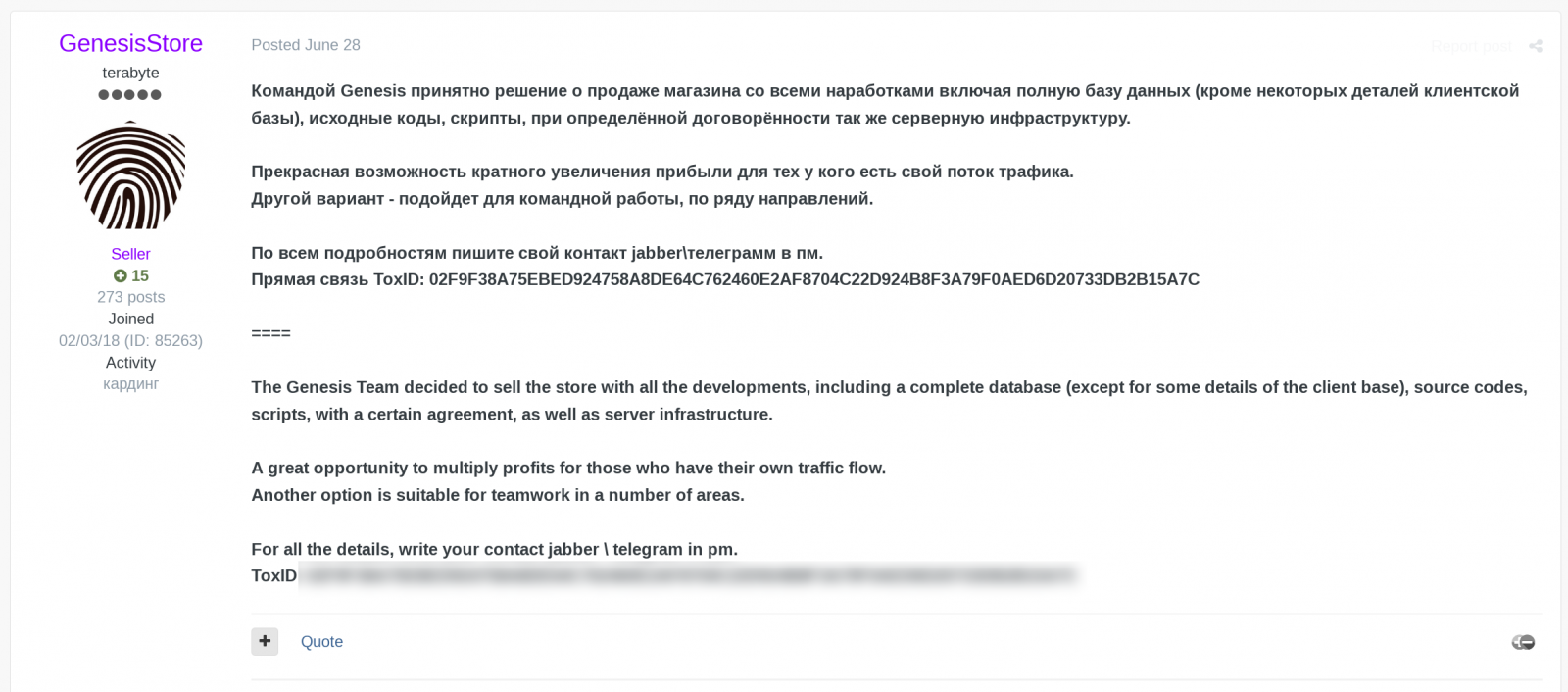
On June 28, the GenesisStore account, used by a Genesis Market operator for ads on a hacker forum, posted that the group behind the store had decided to sell the platform.
In a post shared by a cybersecurity company To burst with BleepingComputer, the seller said the package included “the store with all development”, a complete database without some details about clients, source code, scripts and server infrastructure.”
Source: Flare
The deal would also include the inventory that has made the market a thriving cybercriminal business:
- device fingerprinting (e.g. cookies, IP addresses, time zones, device information)
- cookies
- the form collector that collected all the data (custom JavaScript code)
- saved passwords
- other personal details from networked computers
GenesisStore appealed to potential buyers by saying that acquiring the platform would dramatically increase profits for those who already have a “flow of traffic”.
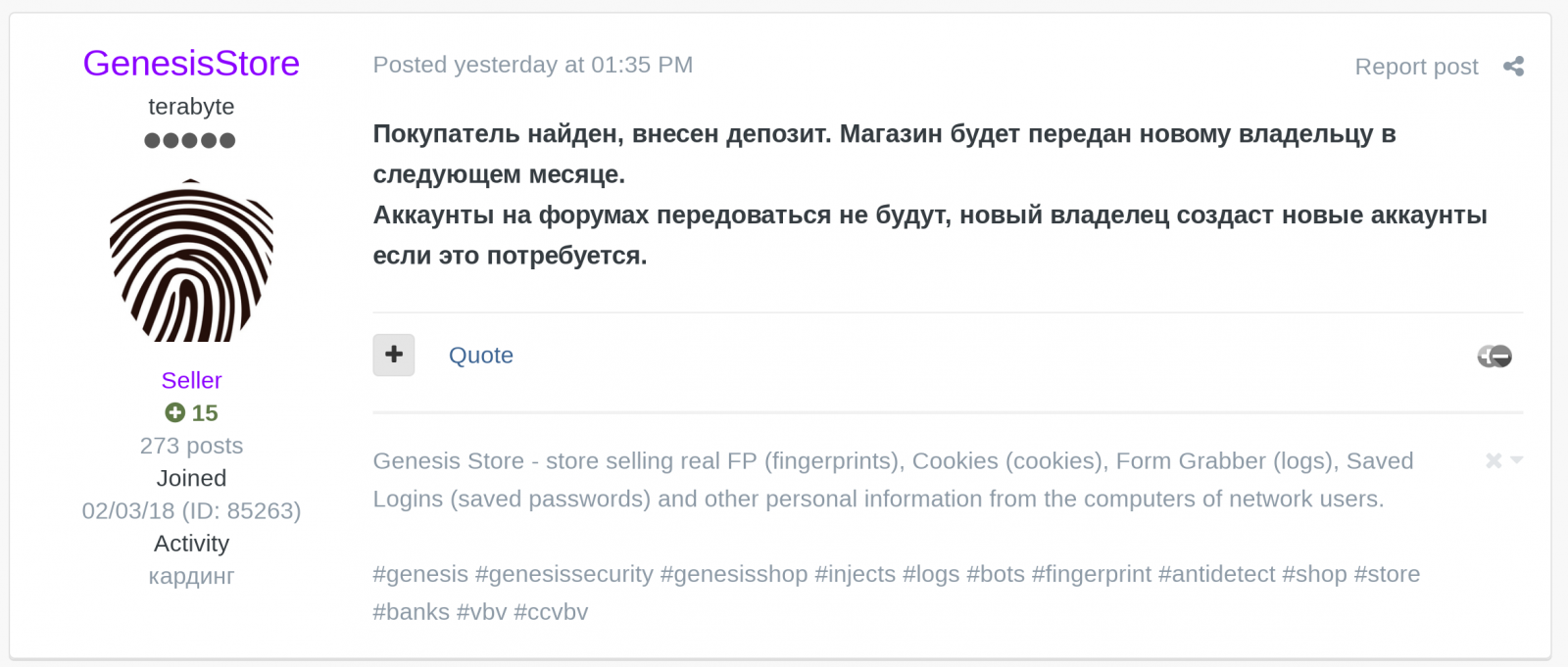
On Thursday, GenesisStore announced that a customer had made a deposit and the deal is expected to close “next month” with the new owner taking full control.
Marketplace admins also noted that they wouldn’t give away forum accounts, so the new owner would have to create new ones if they wanted that community segment.
Source: Flare
An automatic translation of the above message reads “A buyer has been found and a deposit has been made. The store will be handed over to a new owner next month. Accounts on the forums will not be transferred, the new owner will create new accounts if necessary.
Go-to market for device fingerprinting
Genesis Market was launched at the end of 2017 in the alpha phase. After three years, it was the most popular store selling account credentials for online services, device fingerprinting and cookies.
Part of the success was developing custom JavaScript code to collect all the data needed to create a fingerprint of the device to impersonate the victim machine connecting to a service.
To the service provider, this appeared as a regular login by the rightful account owner using their regular machine from the normal geo location.
The JavaScript was distributed via various information-stealing malware (RedLine, DanaBot, Raccoon, and AZORult).
Genesis Market hired bots that provided the customer with stolen account identities in real time. This way, if any details change on the victim machine, the bot would replicate almost instantly.
Depending on account type, the price of a bot ranged from $0.70 for mainstream accounts (Gmail, Facebook, Netflix, Spotify, WordPress, PayPal, Reddit, Amazon, LinkedIn, Cloudflare, Twitter, eBay) to hundreds of US dollars. for online banking.
When law enforcement seized the Genesis Market clearnet domains, the platform offered around 80 million credentials and digital fingerprints, according to the National Crime Agency in the UK.
Despite this action, the platform remained active on the dark web. ZeroFox researchers said at the time that the market increased its inventory with new bots after law enforcement’s Operation Cookie Monster reached clear web domains.
[ad_2]
Source link
