[ad_1]

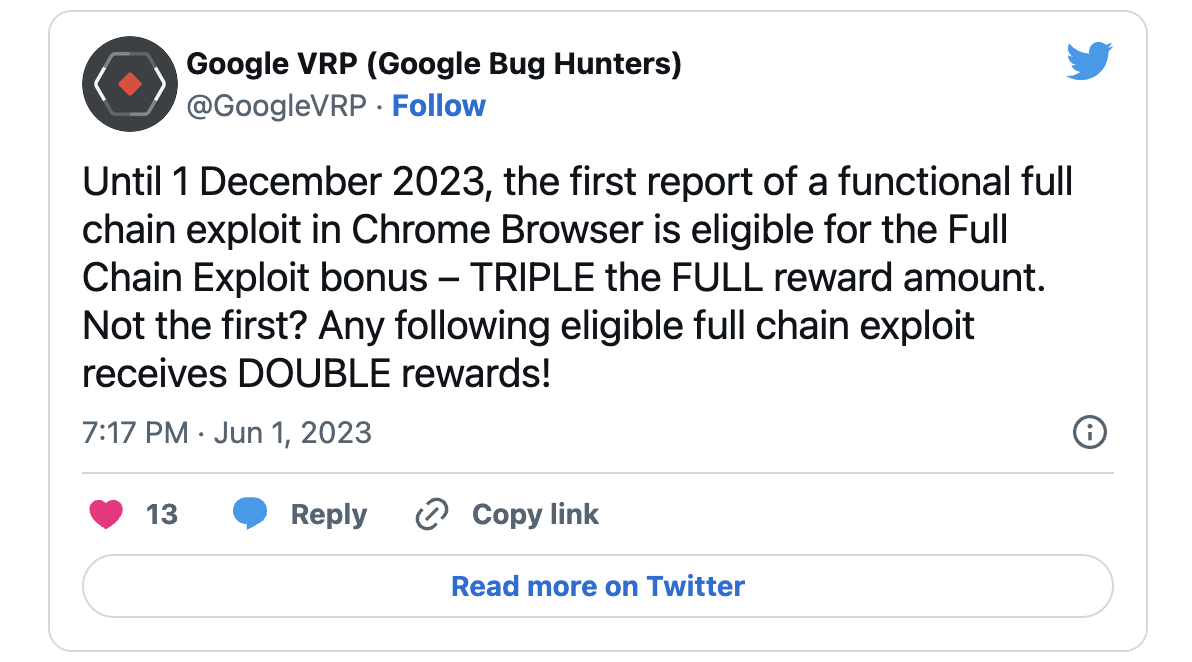
Google today announced that bug bounty hunters who report sandbox escape chain exploits targeting its Chrome web browser are now eligible for triple the standard reward through December 1, 2023.
The company’s initiative aims to encourage security researchers to identify and report vulnerabilities that could help hackers compromise Chrome Browser’s security mechanisms, helping to improve the software’s overall resilience against attack.
The Chrome Vulnerability Reward Program bonus is effective starting today, June 1, and only applies to the first working exploit in the full chain.
“The full chain exploit must result in an escape from the Chrome Browser sandbox, with a demonstration of attacker control / code execution outside of the sandbox. The exploit scenario must be completely remote and the exploit must be usable by a remote attacker”, Google explain.
“Eligible full-chain exploits should work with stable extended, stable, or beta versions of Chrome at the time of initial bug reports. If the exploit is provided after the bug has been fixed, it should only work with versions of production of Chrome. at the time of the initial report.”
Subsequent full chain achievements submitted through the Chrome VRP will also receive a significant bonus that will double the regular reward.
By submitting a full chain achievement, participants could get a reward of up to $180,000, potentially augmented by other bonuses, and up to $120,000 for other achievements received throughout the six-month submission window. month.
“These exploits provide us with valuable insight into potential attack vectors for Chrome exploitation and allow us to identify strategies to better harden specific Chrome features and insights for future large-scale mitigation strategies. “, said Amy Ressler, Senior Technical Program Manager for the Chrome Security Team.
Recent developments of Google VRP
Today’s announcement follows the launch of the new mobile vulnerability rewards program (Mobile VRP) in May, which comes with awards for security flaws found in Google’s Android apps.
In August, the company also announcement that it would pay for reported bugs in the latest released versions of Google’s open source software, including projects such as Bazel, Angular, Golang, Protocol buffers, and Fuchsia.
In a decade, Google has paid out more than $50 million in bounties to researchers who reported more than 15,000 vulnerabilities under its Vulnerability Reward Program (VRP). since its creation in 2010.
Last year alone, Google paid $12 millionwith a record $605,000 reward to gzobqq (the highest amount ever rewarded in Android VRP history) for a series of five security bugs that are part of an Android exploit chain.
The same researcher reported another critical Android exploit string the previous year, earning another impressive payout of $157,000.
[ad_2]
Source link