[ad_1]

A Chinese state-sponsored hacking group named “Camaro Dragon” is infecting residential TP-Link routers with custom “Horse Shell” malware used to attack European foreign affairs organizations.
The backdoor malware is deployed in custom, malicious firmware designed specifically for TP-Link routers so hackers can launch attacks that appear to originate from home networks.
“It should be noted that this type of attack does not specifically target sensitive networks, but rather classic residential and home networks,” the Check Point report explains.
“Therefore, infecting a home router does not necessarily mean that the owner was a specific target, but rather that their device was just a means for the attackers.”
The deployed malware allows hackers full access to the device, including executing shell commands, uploading and downloading files, and using it as a SOCKS proxy to relay communication between devices.
Horse Shell TP-Link firmware implant was discovered by Searching for checkpoints in January 2023, which claims that hacker activity overlaps with that of the Chinese hacking group “Mustang Panda” recently detailed in Avast And ESET reports.
Check Point tracks this business separately using the “Camaro Dragon” name for the business cluster despite the similarities and considerable overlap with Mustang Panda.
The attribution was made based on the IP addresses of the attackers’ servers, requests containing hard-coded HTTP headers found on various Chinese websites, numerous typos in the binary code which show that the author is not English speaking and functional similarities of the Trojan horse with the APT31 “Pakdoor” ripper implant.
TP-Link Firmware Implementation
While Check Point has not determined how attackers infect TP-Link routers with the malicious firmware image, they said it could be by exploiting a vulnerability or brute-forcing administrator credentials. .
Once a hacker gains admin access to the management interface, they can remotely update the device with the custom firmware image.
Upon investigation, Check Point found two sample firmware images containing Trojans for TP-Link routers, both containing significant changes and file additions.
Check Point compared the malicious TP-Link firmware with a legitimate version and found that the kernel and uBoot sections were the same. However, the malware used a custom SquashFS file system that contained additional malicious file components that were part of the Horse Shell backdoor malware implant.
“Parts of it have the internal name Horse Shell, so we use that to name the implant as a whole. The implant provides the attacker with 3 main functionalities: remote shell, file transfer and tunneling”, explains Check Point.
The firmware also changes the web-based management panel, preventing the device owner from flashing a new firmware image for the router and ensuring the infection persists.
The Horse Shell Backdoor
When the Horse Shell backdoor implant is initialized, it will instruct the operating system not to terminate its process when SIGPIPE, SIGINT, or SIGABRT commands are issued, and to be converted into a daemon to run in the background .
The backdoor will then connect to the command and control (C2) server to send the victim’s machine profile, including username, OS version, time, device, IP address, MAC address and supported implant features.
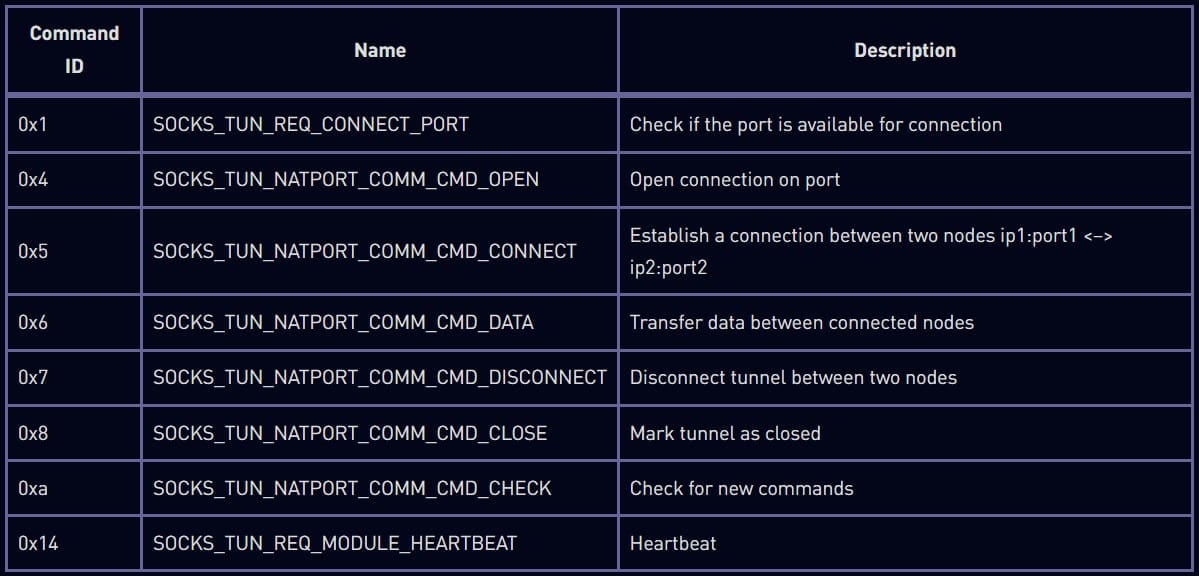
Horse Shell will now run silently in the background while waiting for one of three commands:
- Start a remote shell giving hackers full access to the compromised device.
- Perform file transfer activities including uploading and downloading, basic file manipulation, and directory enumeration.
- Start tunneling to hide the origin and destination of network traffic and hide the C2 server address.
The researchers say the Horse Shell firmware implant is firmware independent, so it could theoretically work in firmware images for other routers from different vendors.
It’s no surprise to see state-sponsored hackers targeting poorly secured routers, often targeted by botnets for DDoS attacks or crypto-mining operations. Indeed, routers are often overlooked when implementing security measures and can act as a stealthy launch pad for attacks, obscuring the origin of the attacker.
Users are advised to apply the latest firmware update for their router model to fix existing vulnerabilities and change the default admin password to something strong. However, even more critical, disable remote access to the device admin panel and make it only accessible from the local network.
A recurring theme
Edge Network devices have become a popular target for state-sponsored threat actors, with Chinese hackers previously targeting FortinetVPN And SonicWall SMA routers with custom firmware implants.
More recently, UK cybersecurity agencies NCSC and US CISA warned that Russian state-sponsored threat actors were also breach cisco routers to install custom malware.
Because these devices typically do not support Endpoint Detection and Response (EDR) security solutions, hackers can use them to steal data, spread laterally, and carry out other attacks with less opportunity for detection.
“There is a recurring theme of cyber espionage’s continued focus on the China nexus on network devices, IOT devices, etc. that do not support EDR solutions,” said Charles Carmakal, CTO of Mandiant. , to BleepingComputer.
For this reason, it is essential that network administrators install all available security patches on edge devices as soon as they are available and do not publicly expose management consoles.
[ad_2]
Source link
