[ad_1]

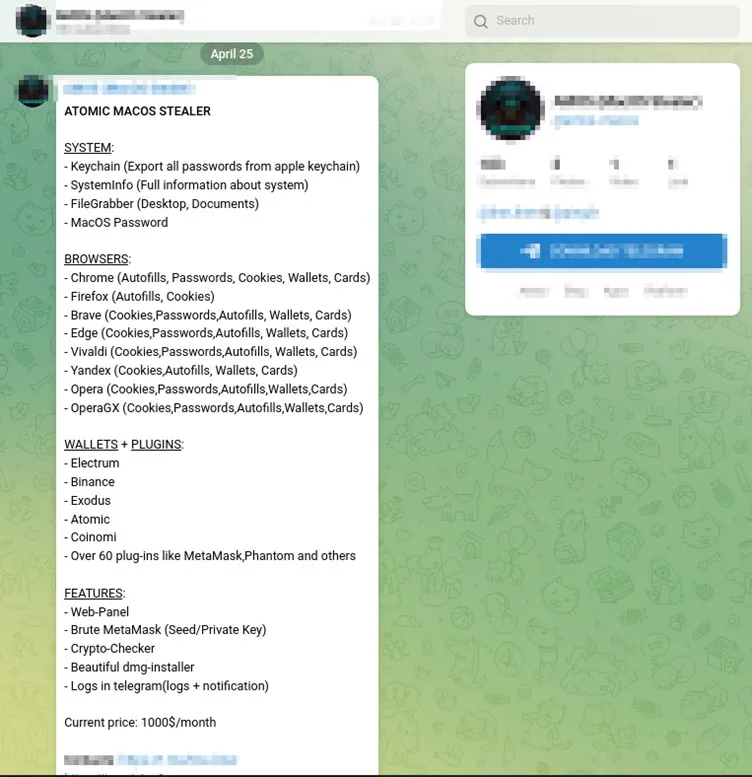
A new macOS information-stealing malware named “Atomic” (aka “AMOS”) is being sold to cybercriminals via private Telegram channels for a $1,000 monthly subscription.
For this hefty price, buyers get a DMG file containing 64-bit Go-based malware designed to target macOS systems and steal keychain passwords, local file system files, passwords, cookies, and credit cards stored in browsers.
The malware also attempts to steal data from over 50 cryptocurrency extensions, which have become a popular target for info-stealing malware.
For the price, cybercriminals also get an out-of-the-box web panel for easy victim management, MetaMask brute forcer, cryptocurrency checker, dmg installer, and the possibility of receiving stolen logs on Telegram.
The malware was recently spotted by a Trellix Researcher and researchers from Cyblabswhich analyzed a sample of ‘Atomic’ and reported that the author released a new version on April 25, 2023, so this is an actively developed project.
At the time of writing, the malicious dmg file will largely undetected on VirusTotalwhere only one out of 59 antivirus engines flags it as malicious.
Regarding its distribution, buyers are responsible for setting up their own channels, which may include phishing emails, malicious advertisements, social media posts, instant messages, black SEO, interlaced torrents, etc.
Atomic Features
The Atomic Stealer has a full suite of data theft features, giving its operators better opportunities to penetrate deeper into the target system.
While executing the malicious dmg file, the malware shows fake password prompt to get the system passwordallowing the attacker to obtain elevated privileges on the victim’s machine.
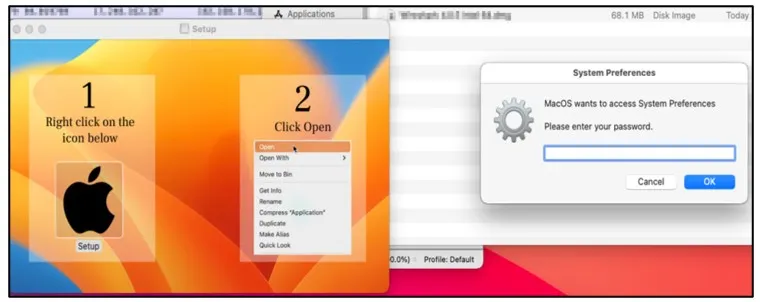
This is a requirement to access sensitive information, but a future update might also take advantage of it to change system settings or install additional payloads.
After this first compromise, the malware attempts to extract the Keychain PasswordmacOS’s built-in password manager that holds Wi-Fi passwords, website logins, credit card data, and other encrypted information.
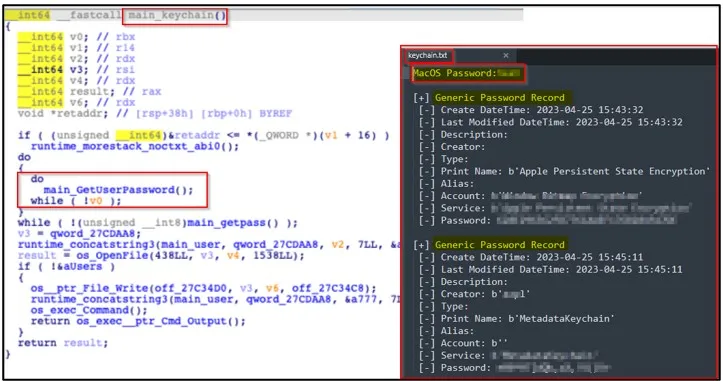
After doing the above, Atomic proceeds to extract information from the software running on the hacked macOS machine, including:
- Desktop cryptocurrency wallets: Electrum, Binance, Exodus, Atomic
- Cryptocurrency Wallet Extensions: 50 extensions are targeted in total, including Trust Wallet, Exodus Web3 Wallet, Jaxx Liberty, Coinbase, Guarda, TronLink, Trezor Password Manager, Metamask, Yoroi and BinanceChain.
- Web browser data: autofills, passwords, cookies and credit cards from Google Chrome, Mozilla Firefox, Microsoft Edge, Yandex, Opera and Vivaldi.
- System information: model name, hardware UUID, RAM size, number of cores, serial number and others.
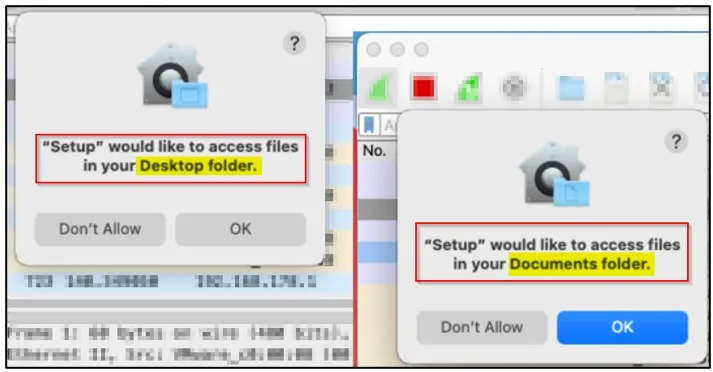
Atomic also gives operators the ability to steal files directly from the victim’s ‘Desktop’ and ‘Documents’ directories.
However, the malware must request permission to access these files, which creates an opportunity for victims to perform the malicious activity.
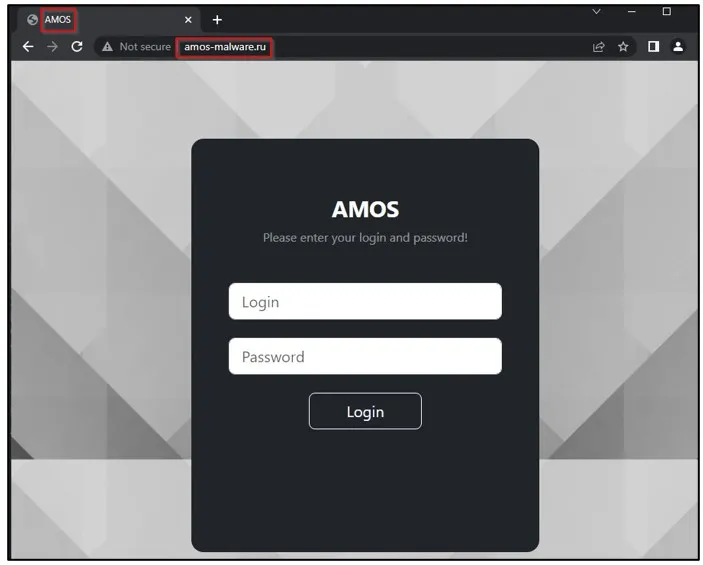
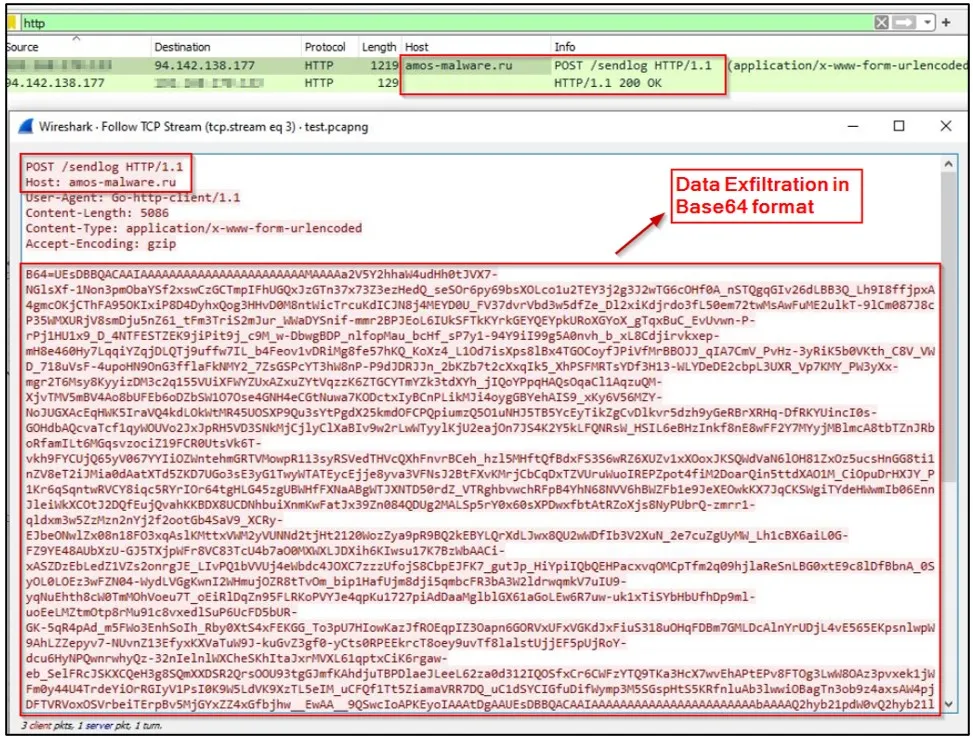
When stealing data, the malware packs everything into a ZIP file and then sends it to the threat actor’s command-and-control server, which Cyble says is located at “amos-malware[.]ru/sendlog.”
Of particular interest, the security researcher from Trellix noted that the IP address associated with the Atmos command and control server and its build name are also used by the Raccoon Stealer, potentially linking the two operations.
From there, the selected information and the ZIP archive are also sent to the operator’s private Telegram channel.
Although macOS is not at the epicenter of malicious information theft activitylike Windows, it is increasingly targeted by hackers of all levels.
A North Korean APT group recently deployed a new macOS infostealer in the 3CX supply chain attackillustrating that Macs are now a target even for state-sponsored hacking groups.
[ad_2]
Source link
