[ad_1]
A malicious actor has uploaded three malicious packages to the Python Package Index (PyPI) repository that contain code to drop information-stealing malware onto developer systems.
Malicious packages, discovered by Fortinet, were all uploaded by the same author named “Lolip0p” between January 7 and January 12, 2023. Their names are “colorslib”, “httpslib” and “libhttps”. All three have been flagged and removed from the PyPI.
PyPI is the most widely used repository for Python packages that software developers use to source the building blocks for their projects.
Unfortunately, its popularity makes it a attractive for threat actors targeting developers or their projects. Typically, malicious packets are downloaded pretending to be something useful or they imitate renowned projects in change his name.
PyPI does not have the resources to review all package downloads, so it relies on user reports to find and remove malicious files. By the time they are removed, however, bad packages typically have several hundred downloads.
New campaign
Unlike typical malicious uploads on PyPI, the trio Fortinet discovered has full descriptions, which helps developers believe they are genuine resources.
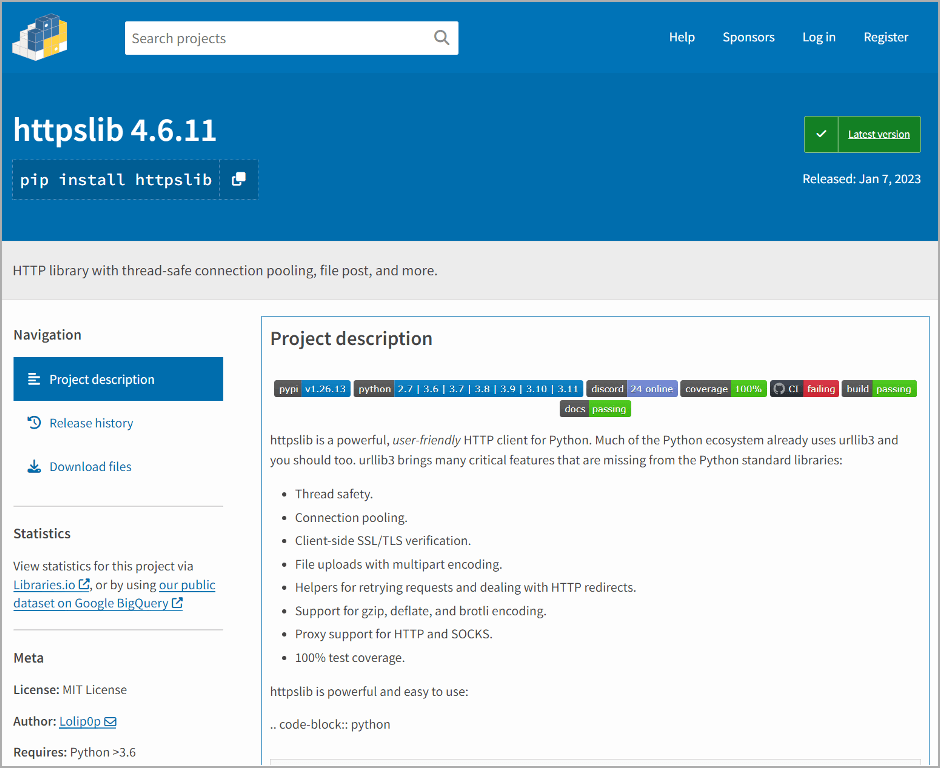
In this case, the names of the packages do not imitate other projects but seek to convince that they are delivered with reliable and risk-free code.
According to the PyPI package statistics count service “pepy.tech”, the three malicious entries had the following number of downloads at the time they were removed on Sunday, January 14.
Although the number of downloads may seem small, the potential impact of these infections as part of a supply chain makes them significant.
All three packages contain the same malicious “setup.py” file which attempts to run PowerShell which retrieves an executable from a suspicious URL, named “Oxyz.exe”. This malware steals browser information.
BleepingComputer discovered that Oxyz.exe is also released as a free Discord Nitro generator.
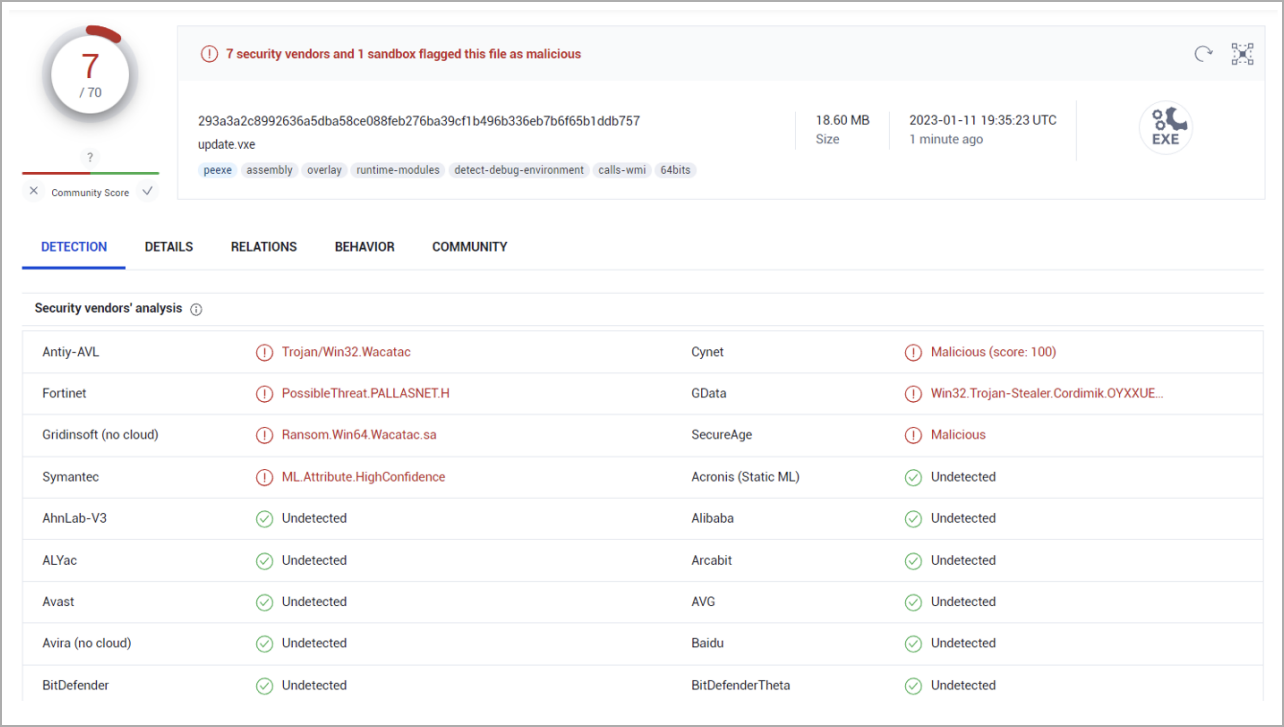
This second file is flagged by a few vendors on VirusTotal as malicious. Fortinet says “update.exe” removes several additional files on the host, including one (“SearchProtocolHost.exe”), which is flagged as malicious by some antivirus vendors as an information stealer.
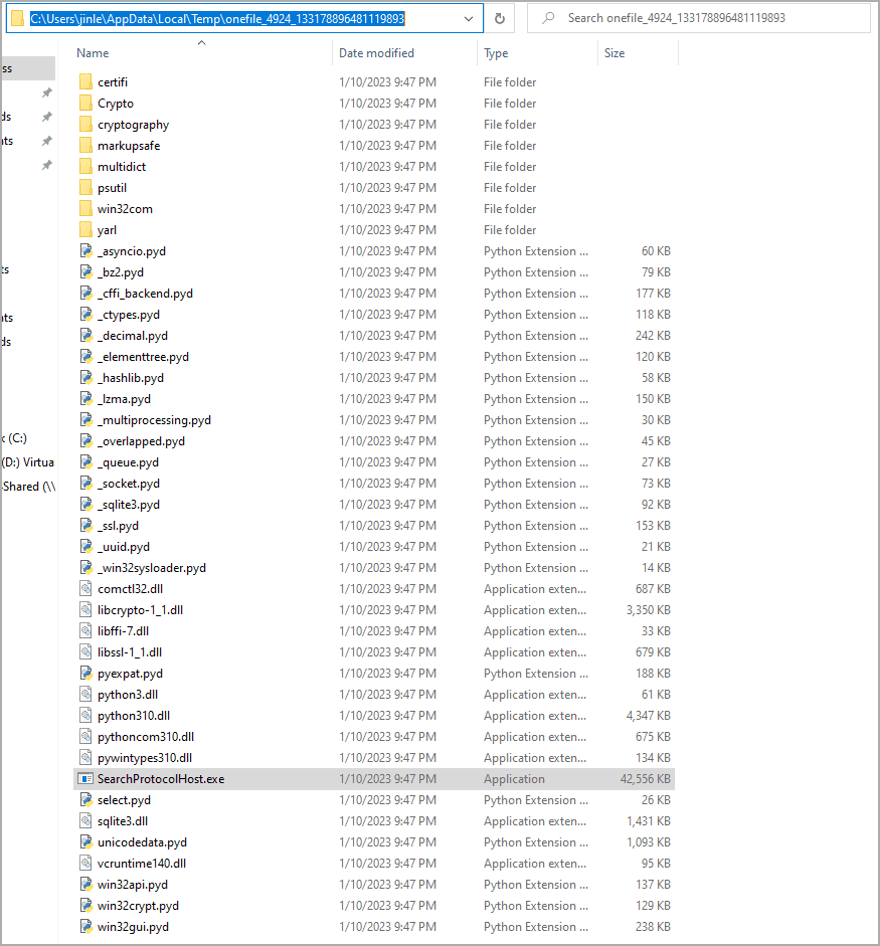
Looking a little deeper, BleepingComputer discovered that at least one of the abandoned processes is being used to collect Discord tokens, suggesting this is part of a general information-stealing malware campaign used to steal data. browser data, authentication tokens and other data from an infected device. .
The detection rates of the three executables used in this attack are quite low, ranging between 4.5% and 13.5%, allowing malicious files to evade detection from several security agents that may be running on the victim host.
Unfortunately, even after deleting these packages from the PyPI, hackers can always re-download them later under a different name.
To ensure the safety and security of their projects, software developers should be careful when selecting packages to download. This includes verifying package authors and examining code for suspicious or malicious intent.
[ad_2]
Source link
