[ad_1]

Amazon Simple Storage Service (S3) will now automatically encrypt all new objects added to server-side buckets, using AES-256 by default.
Although server-side encryption has been available on AWS for more than a decadethe tech giant has it enabled by default to enhance security.
Administrators won’t have to take any action for the new encryption system to affect their buckets, and Amazon promises it won’t have any negative performance impact.
“This change automatically enforces another security best practice, with no performance impact and no action required on your part,” it reads. Amazon’s announcement.
“S3 buckets that do not use default encryption will now automatically apply SSE-S3 as the default setting. Existing buckets currently using default S3 encryption will not change.”
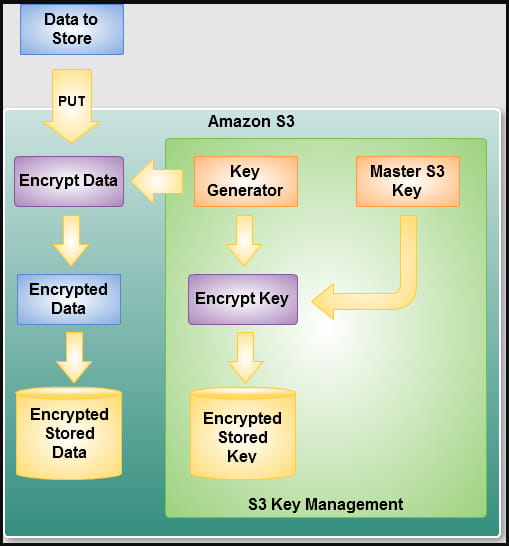
Administrators can leave the system encrypting at AES 256-bit by default or choose one of the alternative methods, namely SSE-C or SSE-KMS.
The first option (SSE-C) gives bucket owners control of the keys, while the second (SSE-KMS) lets Amazon do the key management. However, bucket owners can set different permissions for each KMS key to maintain more granular control over the asset access system.
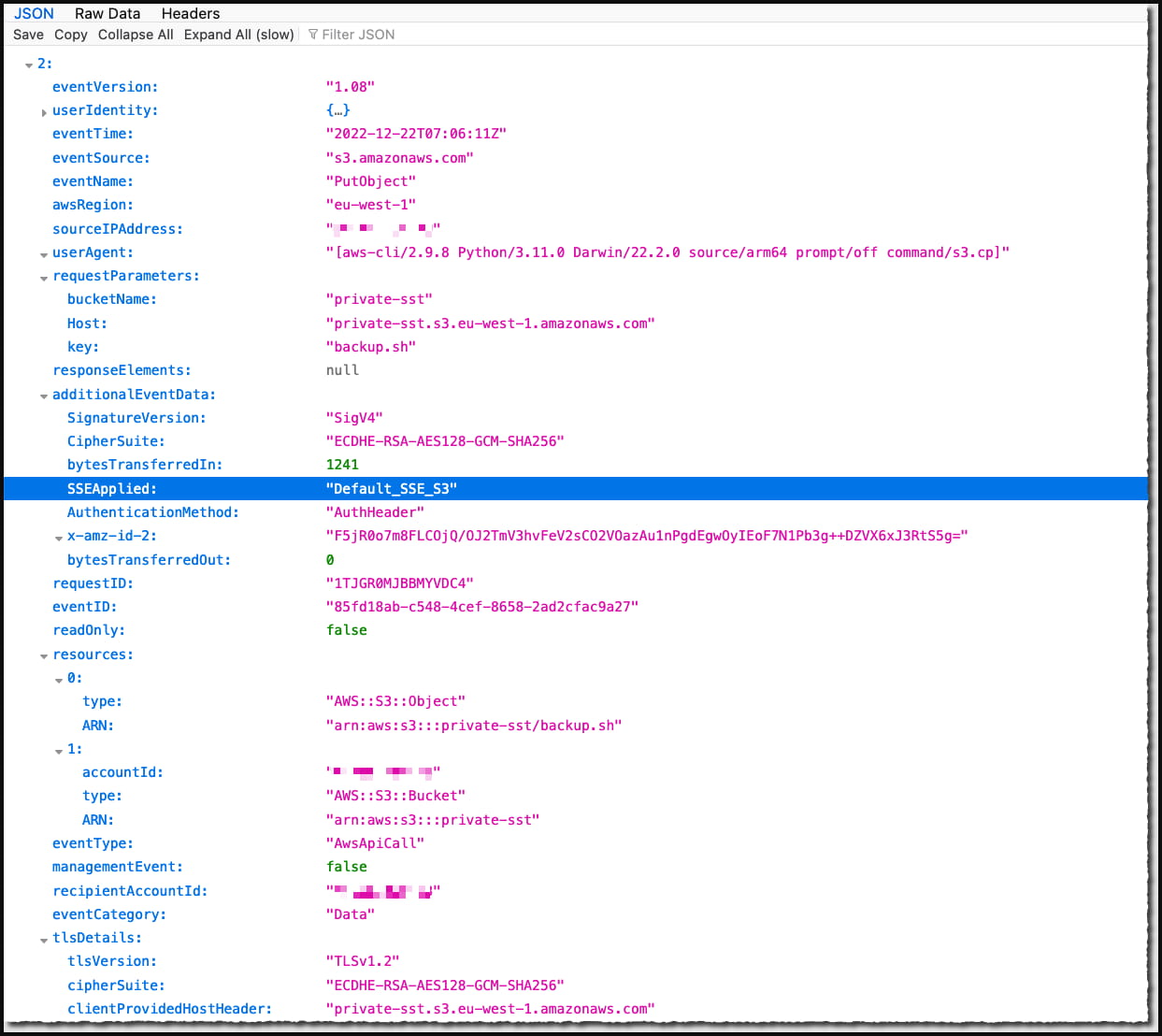
To confirm that the changes have been applied to your buckets, administrators can enable data event logging no additional cost. Then perform a test object download and search the event logs for “SSEApplied”: “Default_SSE_S3”. field in the log for the uploaded file.
To retroactively encrypt objects already in S3 buckets, follow this official guide.
Solve a big security problem
Database leaks have been a security blight for many years now, with bad practices and misconfigurations often exposing the sensitive details of millions of people.
Two notable examples regarding Amazon S3 storage buckets are the data leak from 123 million households in December 2017 and the leak of 540 million records of Facebook users in April 2019.
Had this data been encrypted, the leaks would not have had such dire consequences for those exposed, but unfortunately, due to overhead, operational complexity, and performance sacrifices, database encryption is generally avoided.
Amazon’s decision to make server-side encryption a “zero click” process is a fundamental step towards better security and is intended to mitigate the impact of future data incidents that will inevitably occur.
As for the strength of 256-bit AES encryption algorithm, it is still considered one of the strongest available, with the US government recommending its use. Moreover, despite many try to break itthe scheme has no known weaknesses.
[ad_2]
Source link
