[ad_1]

A security researcher has found a way to harness the data-erasing capabilities of widely used endpoint detection and response (EDR) and anti-virus (AV) software from Microsoft, SentinelOne, TrendMicro, Avast, and AVG to turn them into data erasers.
Wipers are a special type of destructive malware that deliberately erases or corrupts data on compromised systems and attempts to ensure that victims cannot recover data.
SafeBreach researcher Or Yair came up with the idea of leveraging existing security tools on a targeted system to make attacks more stealthy and remove the need for a threat actor to be a privileged user to carry out destructive attacks. .
Also, the misuse of EDRs and AVs for data erasure is a good way to circumvent security defenses, since the file deletion capabilities of security solutions are expected behavior and would likely be missed.
Trigger (bad) deletion
Antivirus and EDR security software constantly scans a computer’s file system for malicious files and, when malware is detected, attempts to quarantine or delete them.
Additionally, with real-time protection enabled, when a file is created, it is automatically scanned to determine if it is malicious and, if so, deleted/quarantined.
“There are two main events when an EDR deletes a malicious file. First, the EDR identifies a file as malicious and then deletes it,” Yair explained in his report.
“If I could do something in between these two events, using a junction, I might be able to steer the EDR down a different path. It’s called time-to-use verification vulnerabilities. (TOCTOU).
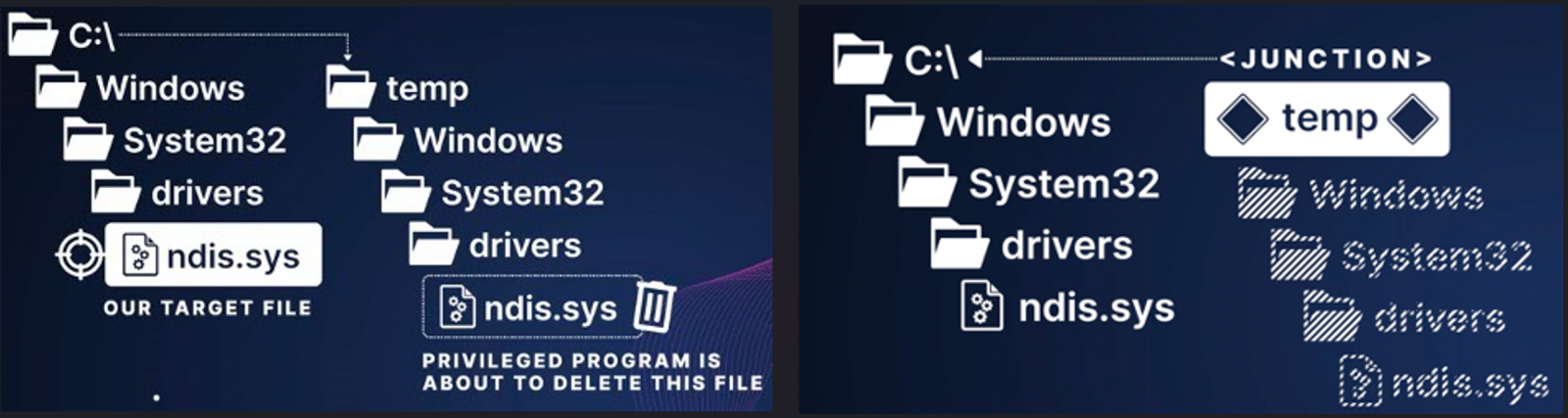
Yair’s idea was to create a C:\temp\Windows\System32\drivers folder and store the Mimikatz program in the folder under ndis.sys.
Since Mimikatz is detected by most EDR platforms, including Microsoft Defender, it was expected to be detected as malicious when it was created. However, before the EDR could delete the file, the seeker would quickly delete the C:\Temp folder and create a Windows junction from C:\Temp to C:\Windows.
The hope was that the EDR would attempt to delete the ndis.sys file which, due to the junction, now points to the legitimate C:\Windows\system32\drivers\ndis.sys file.
This didn’t work because some EDRs prevented further access to a file, including deletion, once it was detected as malicious. In other cases, the EDRs detected the removal of the malicious file, so the software rejected the pending erase action.
The solution was to create the malicious file, maintain its handle by keeping it open, and not define what other processes are allowed to write/delete it so that EDRs and AVs detecting it cannot erase it.
Once the detection was triggered and having no rights to delete the file, the security tools tricked the researcher into approving a system reboot which would free the handle, thus freeing the malicious file for deletion.
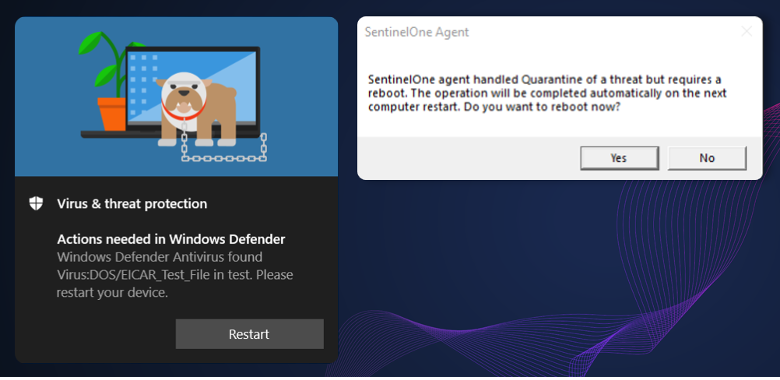
The delete file command, in this case, is written under the PendingFileRenameOperations Registry value, which will cause it to be deleted on reboot.
However, when deleting files in this value, Windows deletes the files while “blindly” following the junctions.
“But the surprising thing about this default Windows feature is that once it restarts, Windows starts stripping all paths and blindly following junctions,” Yair warned.
Therefore, by implementing the following five-step process, Yair could delete files in a directory for which he had no modify privileges.
- Create a special path with the malicious file at C:\temp\Windows\System32\drivers\ndis.sys
- Hold its handle and force the EDR or AV to postpone the deletion until the next reboot
- Delete the C:\temp directory
- Create a junction C:\temp → C:\
- Reboot when prompted.
“This exploit is also effective for a ransomware protection feature in Windows called Controlled Folder Access. This feature prevents untreated processes from modifying or deleting files contained in any of the folders listed in the protected folder list. However, since an EDR or AV is the most trusted entity in a system, this feature does not prevent it from deleting these files.” – SafeBreach.
The analyst implemented the exploit in a wiper tool he named “Aikido Wiper”, which is completely undetectable, can be launched by unprivileged users to wipe data from admin user directories, and can even make the system unbootable.
Impact and response
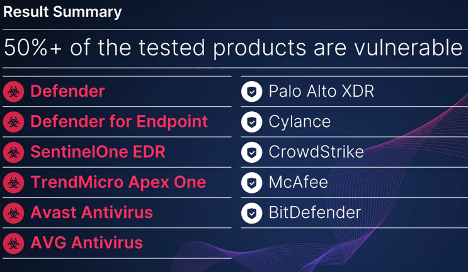
Yair tested the exploit against 11 security tools and found that Microsoft Defender, Defender for Endpoint, SentinelOne EDR, TrendMicro Apex One, Avast Antivirus, and AVG Antivirus were all vulnerable.
Non-exploitable security solutions include Palo Alto, Cylance, CrowdStrike, McAfee and BitDefender, which the analyst also tested.
Aikido offers exploits for vulnerabilities found in Microsoft Defender, Defender for Endpoint, and SentinelOne EDR because they were the easiest to implement on the Wipe Tool.
Yair reported the flaws to all vulnerable vendors between July and August 2022, and they have all released patches to date.
The vendor-assigned vulnerability IDs for this issue are CVE-2022-37971 (Microsoft), CVE-2022-45797 (Trend Micro) and CVE-2022-4173 (Avast and AVG).
Fixed versions are:
- Microsoft Malware Protection Engine: 1.1.19700.2 or later
- TrendMicro Apex One: Hotfix 23573 and Patch_b11136 or later
- Avast and AVG Antivirus: 22.10 or later
It is recommended that all users of the above products apply security updates as soon as possible to mitigate the serious risk of having their files erased by malware that mimics Aikido’s erase functionality.
[ad_2]
Source link
