[ad_1]

US video game publisher 2K has confirmed that its support platform has been hacked and used to target customers with fake support tickets spreading malware via embedded links.
“Earlier today, we learned that an unauthorized third party had illegally accessed the credentials of one of our vendors on the support platform that 2K uses to provide support to our customers” , tweeted the 2K support account on Tuesday after BleepingComputer unveiled the history of the security breach.
“The unauthorized party has sent a communication to some players containing a malicious link. Please do not open any emails or click on any links you receive from the 2K Games support account.”
The company advised those who may have clicked on any of the malicious links sent by the attackers to take immediate action to mitigate the potential impact:
- Reset all user account passwords stored in your web browser (e.g. Chrome AutoFill)
- Enable multi-factor authentication (MFA) whenever available, especially on personal email, banking, and phone or ISP accounts. If possible, avoid using MFA which relies on text message verification – using an authenticator app would be the most secure method
- Install and run a reputable antivirus program
- Check your account settings to see if any forwarding rules have been added or changed on your personal email accounts
2K added that its support portal was taken offline earlier while the video game publisher investigated and dealt with the fallout from the incident.
The company said it will post a notice to let players know when it’s safe to start interacting with its support staff again.
“We will post a notice when you can resume interacting with official 2K Support emails, and we will also provide you with additional information on how best to protect yourself from malicious activity,” 2K said.
Hi folks, please read an important message from our customer support team. Thanks. pic.twitter.com/yKI18eL7mY
— 2K Support (@2KSupport) September 20, 2022
Malicious emails pushed information thief RedLine
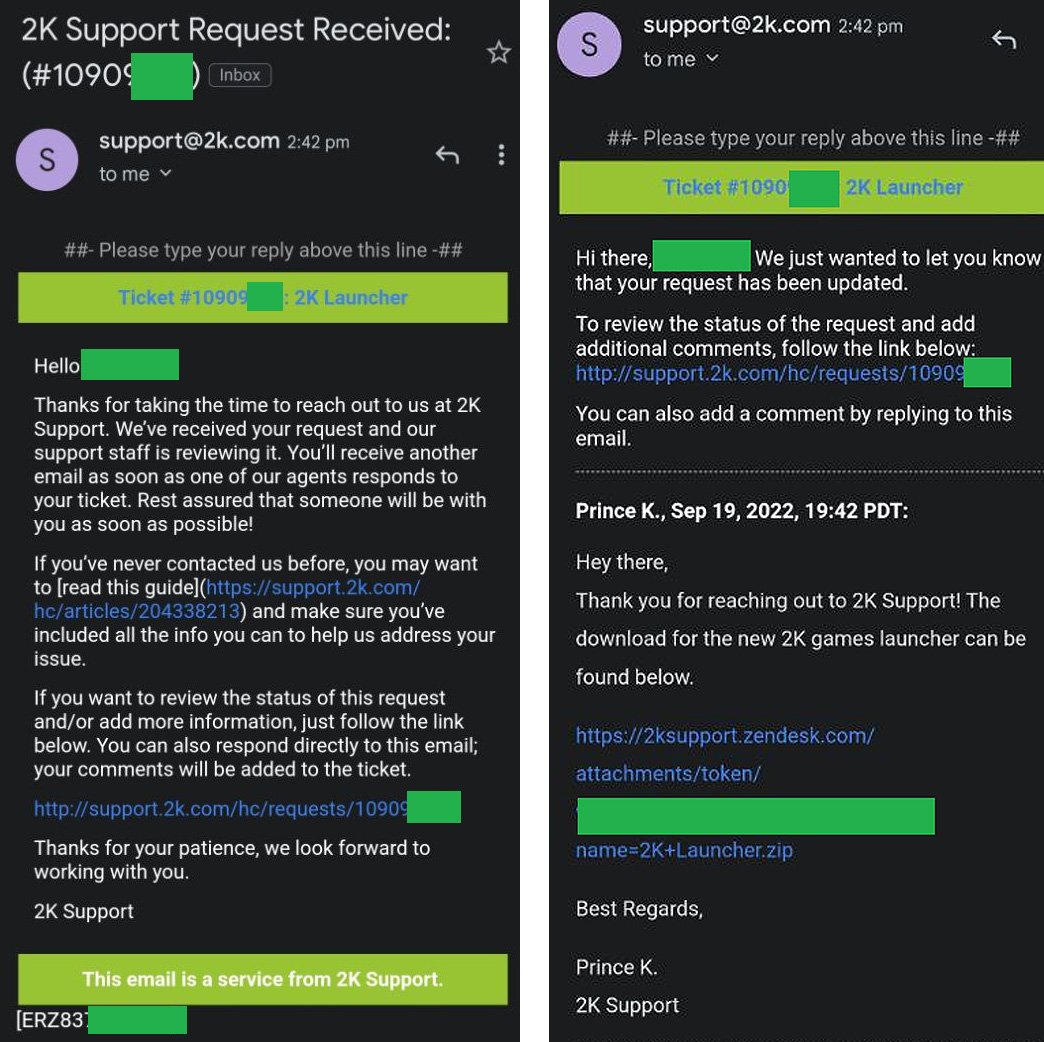
As BleepingComputer previously reported, 2K customers started receiving emails earlier today that they had opened support tickets on 2ksupport.zendesk.com, the support ticket system. 2K online.
While users have confirmed that these tickets can be accessed through 2K’s helpdesk portal, many recipients have said on Twitter and Reddit that they are not the ones who opened these support tickets.
Shortly after the tickets were opened, they also received another email in response to the original ticket (from an alleged 2K support representative named “Prince K”), emails also containing links to download a file named “2K Launcher.zip” from 2ksupport. .zendesk.com.
As BleepingComputer discovered, the archive contained an executable that is actually the RedLine info-stealing malware, according to VirusTotal and Any.Run scans.
RedLine Stealer is information stealing malware which threat actors use to steal wide range of data after infecting its system including web browser history, cookies, saved browser passwords , credit cards, VPN credentials, IM content, cryptocurrency wallets, and more. .
Although 2K has not yet provided any information on this, it is not clear if the attack on its support system is related to the Rockstar Games hack this weekendbut the timing is definitely suspicious.
Both companies are subsidiaries of Take-Two Interactive, one of the largest video game publishers in America and Europe.
The threat actor behind the Rockstar Games breach also claimed responsibility. recent Uber hackwho believes the attack was orchestrated by a hacker affiliated with Lapsus$ extortion group.
2K is the publisher of many popular game franchises including NBA 2K, Borderlands, WWE 2K, PGA Tour 2K, Bioshock, Civilization and Xcom.
BleepingComputer had contacted 2K about the hacking of their support systems before the game publisher confirmed the attack, but we are still awaiting a response.
[ad_2]
Source link
