[ad_1]

The Department of Justice today revealed that an 18-year-old man named Joseph Garrison of Wisconsin has been charged with hacking into the accounts of approximately 60,000 users of the DraftKings sports betting website in November 2022.
According to complaint, the suspect used a long list of credentials from other breaches to hack into the accounts. He then sold the hacked accounts and the buyers stole around $600,000 from around 1,600 compromised accounts.
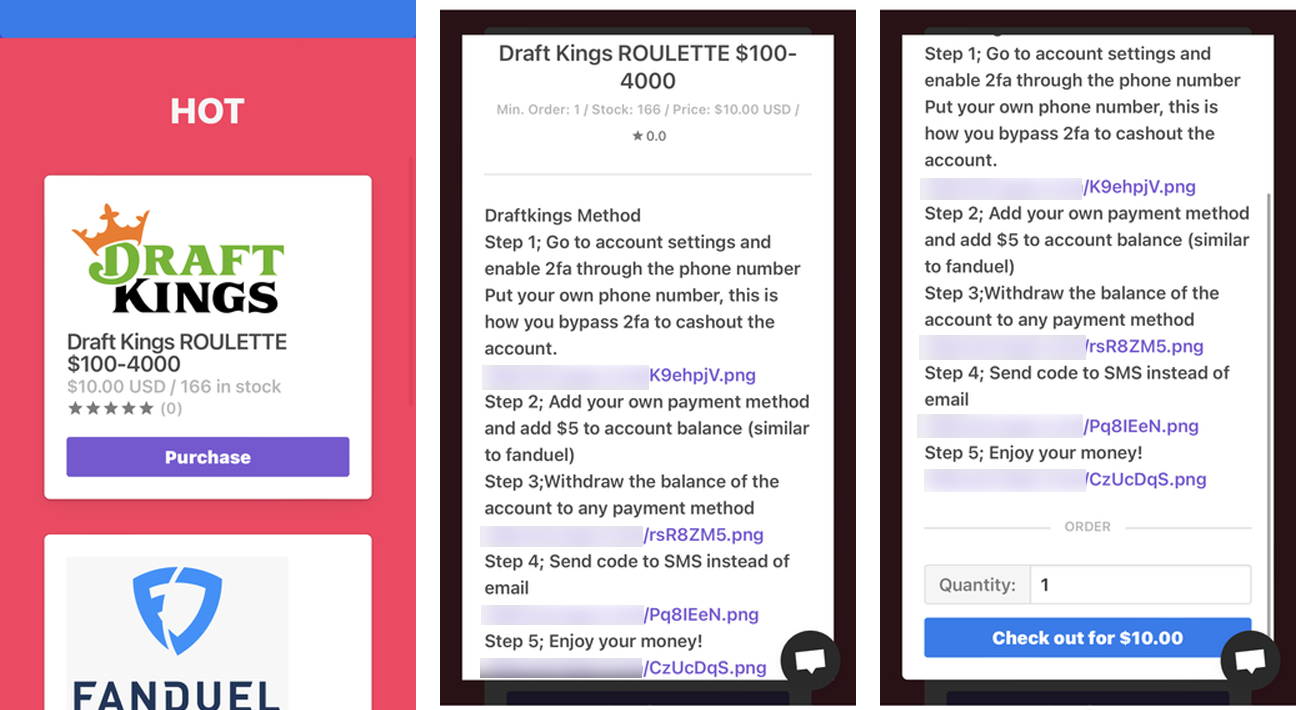
Garrison and his co-conspirators devised a method for buyers of the stolen accounts to withdraw all funds, instructing them to add a new payment method to the hacked accounts, deposit a nominal sum of $5 via the newly added to verify its validity and then withdraw all existing funds from the victims’ accounts to a separate financial account under the control of the attackers.
During a February 2023 search of Garrison’s residence, law enforcement found tools commonly used in credential stuffing attacks (including OpenBullet and SilverBullet) that require files from ” configuration” customized for each targeted website.
Around 700 configuration files for dozens of corporate websites were found on the suspect’s computer, including 11 separate files for the betting website attacked in November.
Additionally, the search also uncovered at least 69 files (known as wordlists) containing approximately 38,484,088 username and password combinations, which were also used in credential stuffing attacks.
While analyzing Garrison’s phone, law enforcement officers found additional evidence implicating the accused in the November 2022 ID attack on the betting platform, including discussions with co -conspirators regarding the hacking of the website.
In one such conversation, Garrison even expressed a belief that law enforcement would be unable to apprehend or prosecute him, stating, “cheating is fun…I’m addicted to seeing money on My account… I’m like obsessed with circumventing shit”.
Links to DraftKings Credentials Attack
Although the Department of Justice did not name the betting site targeted in the attack, BleepingComputer is aware of a scheme targeting both DraftKings [1, 2] And FanDuel in November 2022.
This was confirmed by someone close to the company who said DraftKings was the target of the credential stuffing attack described in today’s DOJ press release, according to CNBC.
DraftKings first unveiled November 21 that up to $300,000 was stolen from hacked accounts in an ID attack.
In November, after learning that over $300,000 had been stolen, BleepingComputer contacted DraftKings and was told, “Your source is incorrect on both the dollar amount and the number of customers involved.”
A month later, the sports betting company said reimbursed hundreds of thousands of dollars stolen after 67,995 customers had their accounts hacked in the incident (matching the number of accounts mentioned in the complaint and the DOJ press release).
During the same period in November, FanDuel customers reported account compromises after credential stuffing attacks, with compromised accounts being sold on cybercrime marketplaces for as little as $2.
Garrison is known to have run the “Goat Shop” website selling hacked DraftKings and FanDuel accounts after the two attacks.
“On the Garrison Phone, law enforcement found an undated photo showing Goat Shop sold 225,247 products for total revenue of $2,135,150.09,” the complaint states.
The same detailed instructions on how to purge breached DraftKings accounts were provided on another online store that match the instructions posted on the Garrison’s Goat Shop website in the complaint.
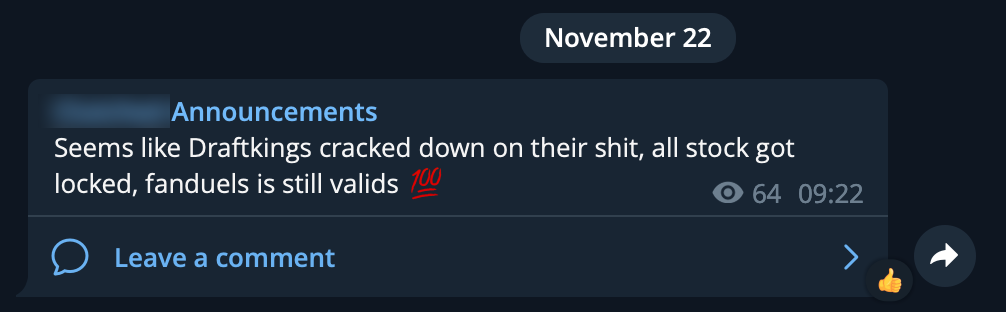
The co-conspirators were also monitoring DraftKings’ response to the incident, and at one point warned that all hacked accounts were now locked after the company reset passwords for affected accounts.
Following the November attack, DraftKings advised customers never to use the same password for multiple services, immediately enable 2FA on their accounts, and unlink their bank accounts or delete their bank details to block requests fraudulent withdrawals.
Chick-fil-A too confirmed in March (following an investigation which began in January) that 71,473 customers had their accounts hacked in an “automated” credential stuffing attack lasting several months between December 18, 2022 and February 12, 2023
The stolen accounts were also listed for sale on the Goat Shop website for up to $200, depending on account balance, linked payment method, or number of Chick-fil-A One reward points.
As the The FBI recently warnedCredential stuffing attacks are increasing in volume and frequency due to readily available automated tools and easy-to-obtain aggregated lists of stolen credentials.
“As alleged, Garrison gained unauthorized access to victims’ accounts using a sophisticated cyberattack to steal hundreds of thousands of dollars,” FBI Deputy Director-in-Charge Michael J. Driscoll said today.
“Cyber intrusions aimed at stealing individuals’ funds pose a serious risk to our economic security. Countering cyberattacks and holding threat actors accountable in the criminal justice system remain a top priority for the FBI.”
Update: Article revised after confirmation that DraftKings was indeed the target of the credential stuffing attack.
[ad_2]
Source link
