[ad_1]

More than 15 million utilities are susceptible to at least one of the 896 vulnerabilities listed in CISA’s known exploitable vulnerabilities (KEV) catalog.
This massive number is reported by cybersecurity firm Rezilion, which has conducted large-scale research to identify vulnerable systems exposed to cyberattacks from threat actors, whether state-sponsored gangs or ransomware. .
Rezilion’s findings are particularly concerning because the vulnerabilities examined are known and highlighted in CISA’s KEV catalog as being actively exploited by hackers, so any delay in patching them maintains a large attack surface, providing actors threat from many potential targets.
Exposed to attack
Rezilion used the web analytics service Shodan to find endpoints still vulnerable to CVEs added to Catalog of Known CISA Exploitable Vulnerabilities.
Using these custom search queries, researchers found 15 million instances vulnerable to 200 catalog CVEs.
More than half of those 7 million instances were vulnerable to one of the 137 CVEs affecting Microsoft Windows, making this component a top priority for defenders and a prime target for attackers.
With the exception of Windows, Rezilion has identified the following top ten CVEs:
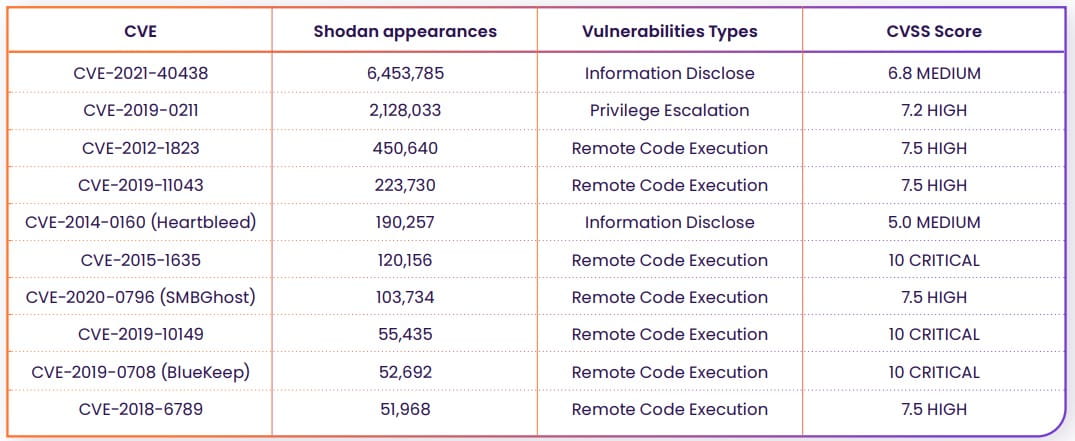
Nearly half of them are over five years old, so around 800,000 machines haven’t applied security updates for a significant period of time.
“Overall, more than 4.5 million internet-connected devices have been identified as vulnerable to KEVs discovered between 2010 and 2020,” Rezilion comments in The report.
“It is of great concern that these machines have not patched relevant released updates for years, even though a patch has been released, and these vulnerabilities are known to be exploited in the wild.”
Some notable CVEs highlighted in the Rezilion report are:
- CVE-2021-40438: Medium severity information disclosure flaw appearing in nearly 6.5 million Shodan results, impacting Apache HTTPD v2.4.48 and earlier servers.
- Proxyshell: A set of three vulnerabilities impacting Microsoft Exchange, which Iranian APTs chained together for remote code execution attacks in 2021. Shodan today returns 14,554 results.
- Proxy connection: a set of four flaws impacting Microsoft Exchange, which Russian hackers widely exploited in 2021 against American infrastructure. There are still 4,990 systems vulnerable to ProxyLogon, according to Shodan, including 584 located in the United States
- HeartBleed (CVE-2014-0160): medium severity flaw impacting OpenSSL, allowing attackers to disclose sensitive process memory information. Shodan says a whopping 190,446 are still vulnerable to this flaw.
Also, for CVE-2021-40438, this large number is the number of websites/services running on Apache, not on individual devices, as many websites can be hosted on a single server.
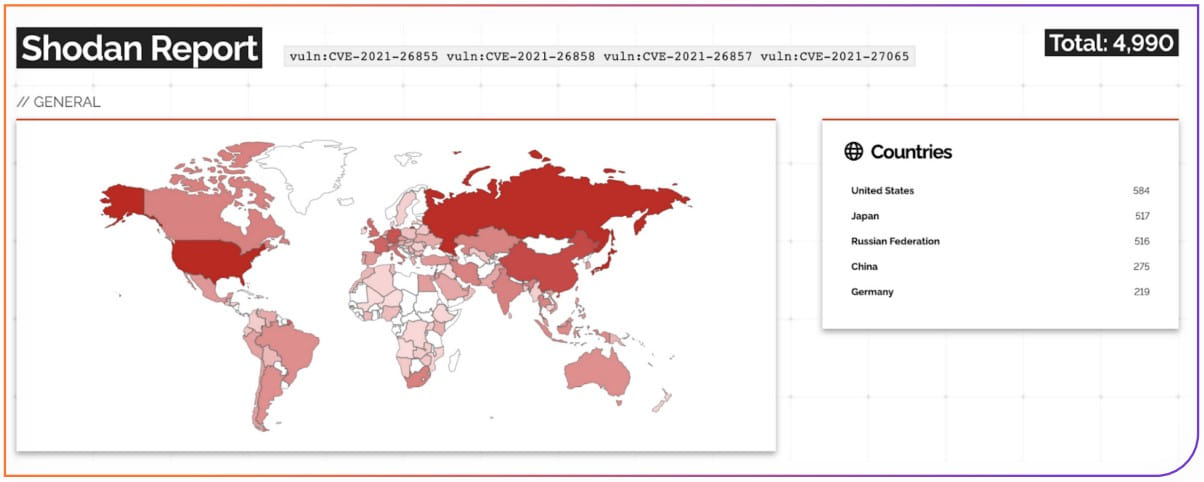
It’s also important to point out that Rezilion’s estimate of 15 million exposed endpoints is conservative, containing only non-duplicates and also omitting cases where researchers could not find queries that reduced the versions of the product.
Rezilion also told BleepingComputer that they not only relied on built-in Shodan CVE searches for their searches, but created custom search queries that determined the versions of software running on devices.
“For some of the vulnerabilities we have inherent Shodan tags, but for the most part we conducted our own analysis which included identifying specific vulnerable versions for each affected product and designing specific shodan queries that will allow us to ‘identify indications of these versions in the metadata visible to Shodan,” Rezilion Vulnerability Research Director Yotam Perkal told BleepingComputer.
Exploitation attempts
Exposure is one thing, but hacker interest is another, and to address it, Rezilion used data from Gray noise which monitors and categorizes attempts to exploit vulnerabilities.
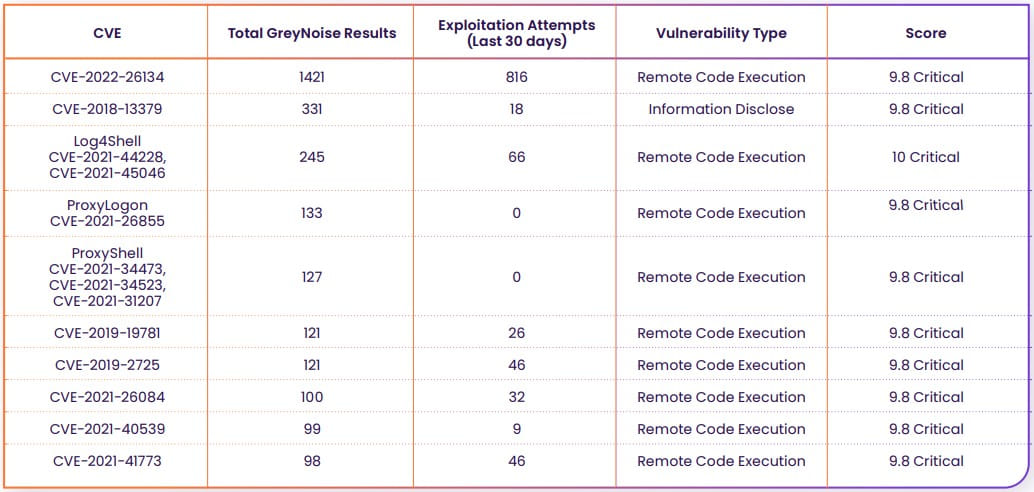
Topping the list with the most exploited flaws is CVE-2022-26134, with 1,421 hits in GreyNoise and 816 exploit attempts over the past month.
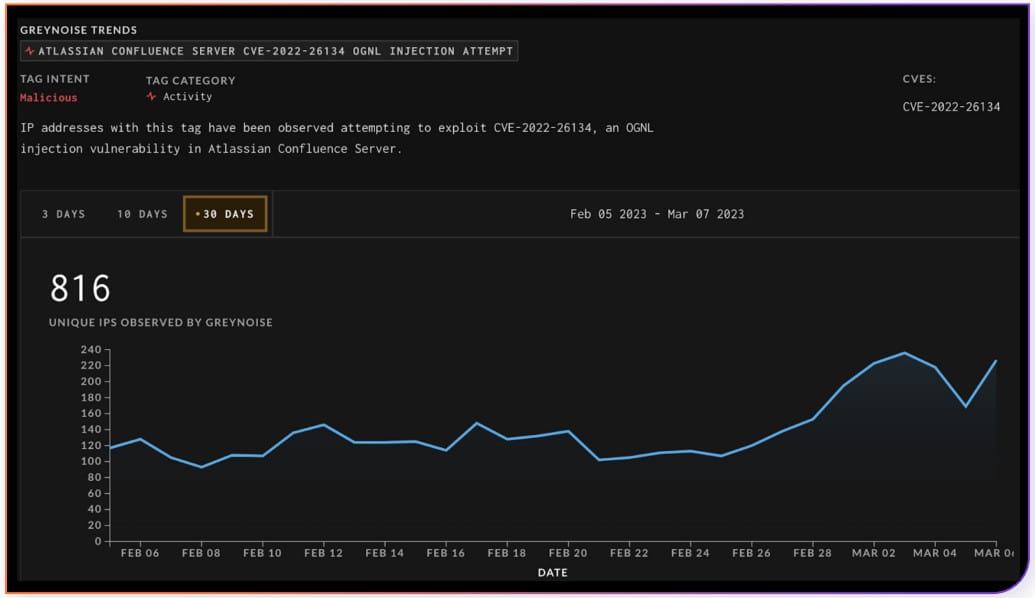
This critical severity flaw in Atlassian Confluence Server and Data Center allows a remote attacker to execute an Object-Graph Navigation Language expression on the vulnerable instance.
Other flaws at the top of the list include CVE-2018-13379, an arbitrary pre-authentication file reader impacting FortiOS devices, which has 331 hits on GreyNoise, and Log4Shell, a nasty code execution bug on Log4J2 which has had 66 exploit attempts in the past month.
Correcting all the flaws in your environment is the apparent solution to these risks,
However, if this is a complicated task for your organization, it is worth prioritizing critical vulnerabilities in your environment or securing them behind a firewall.
Rezilion says Microsoft Windows, Adobe Flash Player, Internet Explorer, Google Chrome, Microsoft Office, and Win32k flaws make up a quarter of CISA’s KEV catalog, so those products would be a good place to start.
[ad_2]
Source link
